Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Programmatically parse random key name in json...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Programmatically parse random key name in json for subfield
Data resembles this pattern.
| makeresults
| eval _raw="{\"foo\": [{\"randstring1\": {\"fqdn\" : \"ibar.example.com\"}}, {\"randstring2\": {\"fqdn\" : \"jbar.example.com\"} }]}"
I am trying to extract the two FQDNs when the containing field name foo{}.* is a random string. Any hints on how to get this data?
I've tried a few different options with spath and can't seem to get it to work. I could try a rex, but I was really hoping to avoid that.
Basically, what I want at the end is a field (multivalue in this case) that has as value ibar.example.com and jbar.example.com.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Like this:
| makeresults
| eval _raw="{\"foo\": [{\"randstring1\": {\"fqdn\" : \"ibar.example.com\"}}, {\"randstring2\": {\"fqdn\" : \"jbar.example.com\"} }]}"
| kv
| foreach *fqdn [ eval mvfield=mvappend(mvfield, '<<FIELD>>') ]
This way, as long as the fields end in fqdn, you get them merged into a field called mvfield.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
....
|rex max_match=0 "\"fqdn\" : \"(?<fqdn>.*?)\""
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
such a neat solution 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
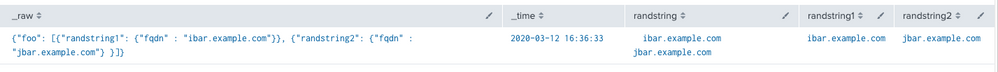
@mmccul_fe like this?
| makeresults
| eval _raw="{\"foo\": [{\"randstring1\": {\"fqdn\" : \"ibar.example.com\"}}, {\"randstring2\": {\"fqdn\" : \"jbar.example.com\"} }]}"
| spath
| rename foo{}.* as * randstring*.fqdn as randstring*
| eval fqdn = ""
| foreach randstring* [eval fqdn = fqdn + " " + '<<FIELD>>']
Note: the screenshot is an older image, i've renamed column3 "randstring" to fqdn in my answer
Results:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why I don't want to use rex...
I have some events that have more than one foo above and I need to basically grab foo..fqdn sometimes, and later grab otherfoo..fqdn, knowing which one I am grabbing.