- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Please help to setup alert
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please help to setup alert?
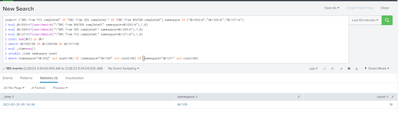
index=* ("ORC from FCS completed" OR "ORC from SDS completed." OR "ORC from ROUTER completed") namespace IN ("dk1692-b","dk1399-b","dk1371-b")
| eval dk1692=if(searchmatch("\"ORC from ROUTER completed\" namespace=dk1692-b"),1,0)
| eval dk1399=if(searchmatch("\"ORC from SDS completed\" namespace=dk1399-b"),1,0)
| eval dk1371=if(searchmatch("\"ORC from FCS completed\" namespace=dk1371-b"),1,0)
| stats sum(dk*) as dk*
| search dk1692>90 OR dk1399>60 OR dk1371>60
Am getting attached output
Problem statement ,
i would like setup alert where ever specific namespace **bleep** goes below its threshold which mention in search query.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry , please check latest screen shot , in this wherever namespace value less than threashhod it shoud throw email alert
For example - dk1399 is 45 which is less than 60
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK, so the fact that this search returns any rows means that at least one of the namespaces is below its threshold. You can use this fact as the trigger in your alert
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes but there are three namespaces with different threshould
Do i have to setup 3 different alerts by using less than trigger ??
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It depends on your requirement. You could have a single alert for any of them being below the threshold, or if you had them in different rows, you could still have a single alert that would trigger for each result.
| where dk1692<90 OR dk1399<60 OR dk1371<60
| eval _time=now()
| untable _time namespace count
| where (namespace="dk1692" and count<90) OR (namespace="dk1399" and count<60) OR (namespace="dk1371" and count<60)- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=* ("ORC from FCS completed" OR "ORC from SDS completed." OR "ORC from ROUTER completed") namespace IN ("dk1692-b","dk1399-b","dk1371-b")
| eval dk1692=if(searchmatch("\"ORC from ROUTER completed\" namespace=dk1692-b"),1,0)
| eval dk1399=if(searchmatch("\"ORC from SDS completed\" namespace=dk1399-b"),1,0)
| eval dk1371=if(searchmatch("\"ORC from FCS completed\" namespace=dk1371-b"),1,0)
| stats sum(dk*) as dk*
| search dk1692<90 OR dk1399<60 OR dk1371<60
| eval _time=now()
| untable _time namespace count
| where (namespace="dk1692" and count<90) OR (namespace="dk1399" and count<60) OR (namespace="dk1371" and count<60)
-------------------------------------------------------------------------------------------------------------
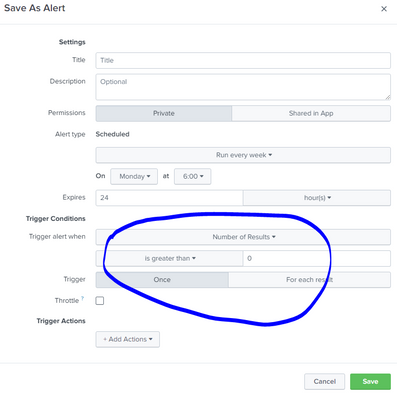
this query good as per my requirement , however how can i setup alert with trigger
Because its giving one row and count.
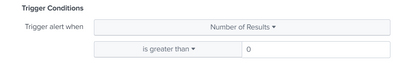
for setting up condition can i use
number of results - is greater than = 0
*** So whenever there is record in above query it will send alert.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
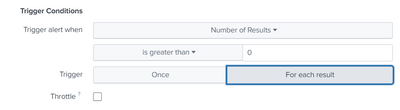
If you also set "For each result", you will get a triggered action for each row i.e. each namespace that is below its threshold
You would need to set an action to be triggered, e.g. an email being sent for each trigger.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
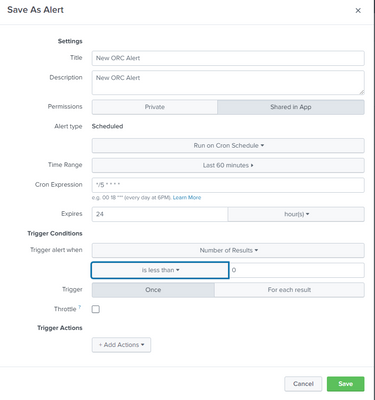
I would like to use throttle option
But when am using each result option for trigger its asking field name suppressing.
how to manage that ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You could try
namespace = $result.namespace$- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
you mean i need to add value
namespace = $result.namespace$
into Suppress results containing field value ??
please confirm
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is what I mean - give it a try 😀
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you so much
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your search is looking for values greater than specific values. Do these indicate that the namespace has gone below its threshold? If so, just copy the search into an alert and trigger when there are greater than zero results.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=* ("ORC from FCS completed" OR "ORC from SDS completed." OR "ORC from ROUTER completed" OR "ORC from EMS completed" OR "ORC from TDS completed") namespace IN ("dk1692-b","dk1399-b","dk1371-b","dk1398-b","dk1400-c")
| eval dk1692=if(searchmatch("\"ORC from ROUTER completed\" namespace=dk1692-b"),1,0)
| eval dk1399=if(searchmatch("\"ORC from SDS completed\" namespace=dk1399-b"),1,0)
| eval dk1371=if(searchmatch("\"ORC from FCS completed\" namespace=dk1371-b"),1,0)
| eval dk1398=if(searchmatch("\"ORC from EMS completed\" namespace=dk1398-b"),1,0)
| eval dk1400=if(searchmatch("\"ORC from TDS completed\" namespace=dk1400-c"),1,0)
| stats sum(dk*) as dk*
| search dk1692<90 OR dk1399<60 OR dk1371<60 OR dk1398<60 OR dk1400<60
| eval _time=now()
| untable _time namespace count
| where (namespace="dk1692" and count<90) OR (namespace="dk1399" and count<60) OR (namespace="dk1371" and count<60) OR (namespace="dk1398" and count<60) OR (namespace="dk1400" and count<60)
----------------------------------------------------------------------------------------------------------------
Thanks in above query , i would like to add one more column which says which namespace is below threshold
example if namespace dk1399-b below 60 it column is should show name SDS