Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Palo/Splunk Parsing Issue - Field values are Trunc...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
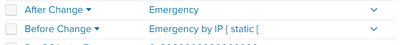
Having a strange issue and not sure what my culprit/problem is. Have a panorama to syslogng to Heavy Forwarder to Indexer with a single search head. I see the parsing (I think) where fields are found and values= but they are truncating. Specifically, my raw event has this in it:
before_change_detail="Emergency by IP { static [ ""Jim CentOS"" ]; } " after_change_detail=Emergency by IP { }
but when i look at the field values, this is what i get:
Any ideas on why my field values are getting cut short?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Finally got this all straightened out. Needed to use cef utils for splunk along with a separate syslog destination from my panorama with custom cef events setup for the config section to get what i wanted.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Finally got this all straightened out. Needed to use cef utils for splunk along with a separate syslog destination from my panorama with custom cef events setup for the config section to get what i wanted.