Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Multivalue-Field Filter
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Multivalue-Field Filter
I receive a bunch of messages that all are assigned to a group by the groupID.
I also have a dynamic set of a range as a Multivalue-Field, that needs to be used as a filter for these messages.
I tried it like this so far, but couldn't get any results:
index=my_index sourcetype=my_source
| eval range=case("case1", mvrange(1,9), "case2", mvrange(10,19),...)
| where groupID in (range)
| stats count(_raw) as count by groupdID
So if case1 happens, i only want to see the amount of Messages in the specified groupID-range, and so on..
Can anyone help me with that ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@kamlesh_vaghela @ITWhisperer
So Here is a little follow up, as i am still not able to get any results:
These are the results without the 'where' clause:
index=my_index sourcetype=my_sourcetype
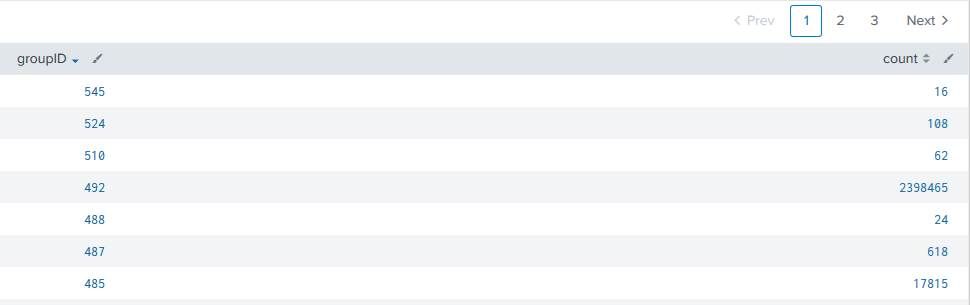
| stats count by groupID
So e.g. there are 2398465 Events for the groupID 492.
However as soon as i add the 'where' clause:
index=my_index sourcetype=my_sourcetype
| eval range=mvrange(492,545)
| where groupID in (range)
| stats count by groupID
I am not getting any results anymore.
Same goes for the above suggestions with:
| where groupID=492
OR
| where tonumber(groupID)=492
OR
| where groupID="492"
Any more ideas ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try it the other way around
index=my_index sourcetype=my_sourcetype
| stats count by groupID
| eval range=mvrange(492,546)
| where groupID in (range)- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sadly didn't change anything
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you can share about the condition in case statements then we can search for optimum solution.
| eval range=case("case1", mvrange(1,9), "case2", mvrange(10,19),...)like, case1 & case2.. how many case are there, etc
/
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am currently trying to get any results, hence why i left the 'case' statement out for now.
However here are the cases i will need for the future:
| eval range=case("case1", mvrange(493,511), "case2", mvrange(436,448), "case3", mvrange(470,480))- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your approach should work.
| makeresults
| eval groupID=8
| eval range=case(groupID<10,mvrange(1,9))
| where groupID in (range)
| stats count by groupID
I found typo (groupdID) in your search. Is this a reason for no results?
index=my_index sourcetype=my_source
| eval range=case("case1", mvrange(1,9), "case2", mvrange(10,19),...)
| where groupID in (range)
| stats count(_raw) as count by groupID
Thanks
KV
▄︻̷̿┻̿═━一 ?
If any of my reply helps you to solve the problem Or gain knowledge, an upvote would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your reply. Sorry about the typo, but that is not the issue because in my actual search i am using different field names anyway - 'groupID' is just for a better visualization.
Hower i found out that if e.g. i add
| where groupID = 8 meaning i just want the messages for groupID 8, i get the following error:
Error in 'where' command: Type checking failed. The '==' operator received different types.
Could that be the issue ?
I also tried:
| where groupID = "8"Then the search does not return an error but again also no results.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| where tonumber(groupID)=8- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try something like this
index=my_index sourcetype=my_source
| eval range=case("case1", mvrange(1,9), "case2", mvrange(10,19),...)
| mvexpand range
| where groupID=range
| stats count by groupdID- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your Reply. Unfortunately that does not return any results either.