Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Multiple values - mvexpand not doing what I ex...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
dbcase
Motivator
02-19-2018
11:44 AM
Hi ,
I have a query that looks like this
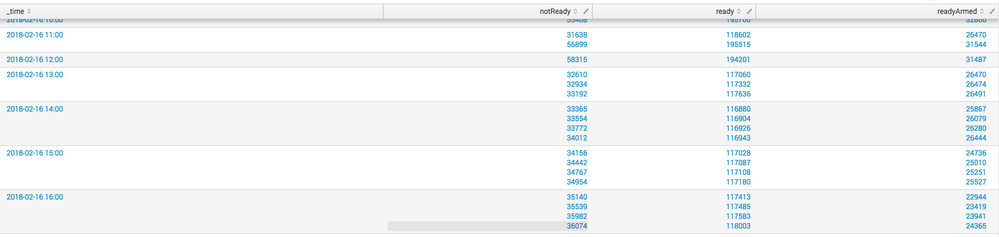
earliest=-100hr index=blahalarm STATUS=readyArmed OR STATUS=ready OR STATUS=notReady|mvexpand notReady|mvexpand ready|mvexpand readyArmed|mvexpand _time|timechart span=1hr values(field2) by STATUS
but the resulting dataset comes back as this. I'm confused, why wouldn't mvexpand create multiple events?
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
dbcase
Motivator
02-19-2018
11:55 AM
FIxed it. My data was coming in with 15min increments but my span=1hr, once I set my span to 15min all is well
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
dbcase
Motivator
02-19-2018
11:55 AM
FIxed it. My data was coming in with 15min increments but my span=1hr, once I set my span to 15min all is well
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
elliotproebstel
Champion
02-19-2018
11:54 AM
Doesn't the final timechart span=1h bring the events back into 1h buckets? The result looks like what I'd expect. Can you say more about what you're trying to achieve?
Career Survey
First 500 qualified respondents will receive a $20 gift card! Tell us about your professional Splunk journey.
Get Updates on the Splunk Community!
Data Persistence in the OpenTelemetry Collector
This blog post is part of an ongoing series on OpenTelemetry.
What happens if the OpenTelemetry collector ...
Introducing Splunk 10.0: Smarter, Faster, and More Powerful Than Ever
Now On Demand
Whether you're managing complex deployments or looking to future-proof your data ...
Community Content Calendar, September edition
Welcome to another insightful post from our Community Content Calendar! We're thrilled to continue bringing ...