Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Search
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Lookup time-based not working with tstats
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Lookup time-based not working with tstats
avasquez
Loves-to-Learn Lots
12-03-2020
06:28 AM
Hi,
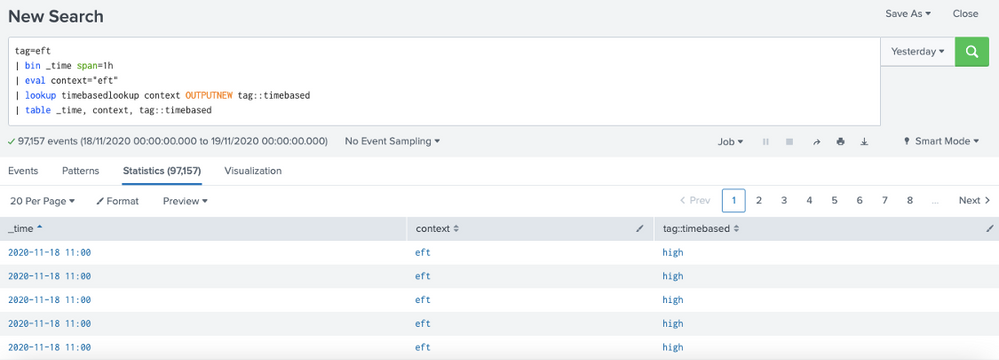
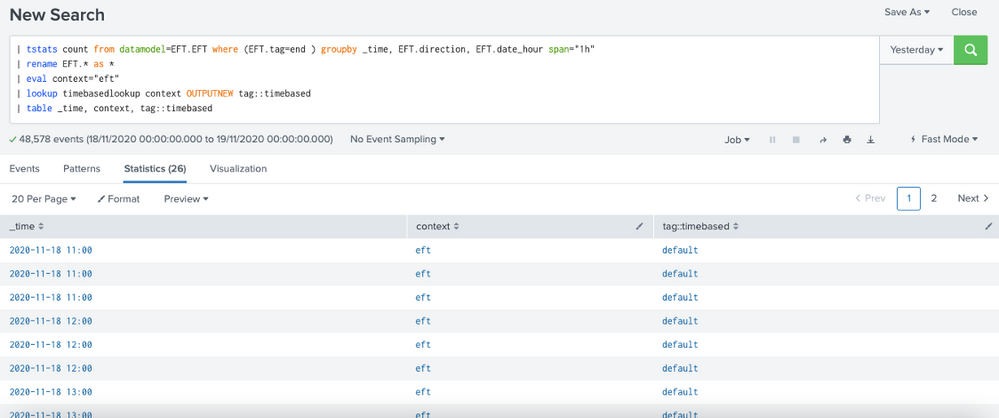
I'm trying to configure a time-based lookup (temporal lookup) but it doesn't seem to be working as expected.
1) The lookup definitions fields are: time, context, tag::timebased
time,context,tag::timebased
2020-11-18,eft,high
2020-11-11,eft,high
2020-11-04,eft,high
2020-10-28,eft,high
2020-10-21,eft,high
2) The The transforms.conf is on the SH
[timebasedlookup]
time_field = time
time_format = %Y-%m-%d
min_matches = 1
max_matches = 10
default_match = default
min_offset_secs = 0
max_offset_secs = 86400
collection = timebasedlookup
external_type = kvstore
fields_list = _key, time, context, tag::timebased
3) When i run a search to index the results are OK ("high" in tag::timebased)
4) But when i run search to datamodel (tstats) the results are NOK ("default" in tag::timebased)
The same _time in index query and tstats query return different results.
Get Updates on the Splunk Community!
Thanks for the Memories! Splunk University, .conf24, and Community Connections
Thank you to everyone in the Splunk Community who joined us for .conf24 – starting with Splunk University and ...
.conf24 | Day 0
Hello Splunk Community!
My name is Chris, and I'm based in Canberra, Australia's capital, and I travelled for ...
Enhance Security Visibility with Splunk Enterprise Security 7.1 through Threat ...
(view in My Videos)Struggling with alert fatigue, lack of context, and prioritization around security ...