Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Is it possible to create a text field where users ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it possible to create a text field where users can type keywords to search the results in a table?
I'm making a table that reports the error events on servers. I was able to make this work fine, allowing it to show the error string, the host and directory it occurred on, and the time it occurred. Now, I would like to make it so the user can type in key words in a text field and the table will only show the events that have these word. When I tried to do this, however, the table returned "No results found." For example, I can have the text input set to the default * and it will show the errors fine, but if I type in "ERROR," which all the events have, it will give me know results found.
Here is the string I am using:
host=$hosttok1$ "ERROR" sourcetype=streamer_nohup source=$sourcetok1$| regex _raw!="WARN"| rex "(?<error>\w{5}\s+.{100})"| table _time host source error| search error=$texttok1$
This is based on a previous table I made that shows IP address and allows you to seek specific IP addresses:
index=qp_mds sourcetype=mds_perf host=$hosttok1$| rex "(?<IP>\d+\.\d+\.\d+\.\d+)" | table _time host IP| search IP=$texttok1$
Note that the IP table works exactly as intended.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I found a simple work around.
The text box was looking for the exact string, the whole error string. All I had to do was put wild cards on each side of the word I type in.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume the token are referring to is $texttok1$. Put it within quotes like this error="$texttok1$"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
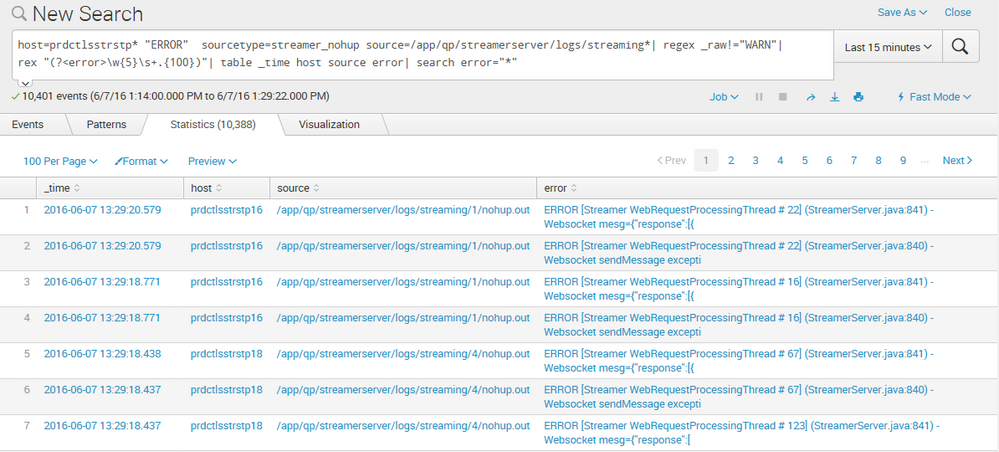
This is the table I see. I couldn't post this image into the comments.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Still nothing.
Here's the rest of the source code, if it helps at all.
<panel>
<input type="time" token="timetok1">
<label>Select a time range.</label>
<default>
<earliest>-15m@m</earliest>
<latest>now</latest>
</default>
</input>
<input type="dropdown" token="hosttok1">
<label>Select a host.</label>
<default>prdctlsstrstp*</default>
<choice value="prdctlsstrstp*">All</choice>
<choice value="prdctlsstrstp09">prdctlsstrstp09</choice>
<choice value="prdctlsstrstp10">prdctlsstrstp10</choice>
<choice value="prdctlsstrstp11">prdctlsstrstp11</choice>
<choice value="prdctlsstrstp12">prdctlsstrstp12</choice>
<choice value="prdctlsstrstp13">prdctlsstrstp13</choice>
<choice value="prdctlsstrstp14">prdctlsstrstp14</choice>
<choice value="prdctlsstrstp15">prdctlsstrstp15</choice>
<choice value="prdctlsstrstp16">prdctlsstrstp16</choice>
<choice value="prdctlsstrstp17">prdctlsstrstp17</choice>
<choice value="prdctlsstrstp18">prdctlsstrstp18</choice>
<choice value="prdctlsstrstp19">prdctlsstrstp19</choice>
<choice value="prdctlsstrstp20">prdctlsstrstp20</choice>
<choice value="prdctlsstrstp21">prdctlsstrstp21</choice>
<choice value="prdctlsstrstp22">prdctlsstrstp22</choice>
<choice value="prdctlsstrstp23">prdctlsstrstp23</choice>
<choice value="prdctlsstrstp24">prdctlsstrstp24</choice>
<choice value="prdctlsstrstp25">prdctlsstrstp25</choice>
<choice value="prdctlsstrstp26">prdctlsstrstp26</choice>
<choice value="prdctlsstrstp27">prdctlsstrstp27</choice>
<choice value="prdctlsstrstp28">prdctlsstrstp28</choice>
<choice value="prdctlsstrstp29">prdctlsstrstp29</choice>
<choice value="prdctlsstrstp30">prdctlsstrstp30</choice>
</input>
<input type="dropdown" token="sourcetok1">
<label>Select a directory</label>
<default>/app/qp/streamerserver/logs/streaming*</default>
<choice value="/app/qp/streamerserver/logs/streaming*">All</choice>
<choice value="/app/qp/streamerserver/logs/streaming/1/nohup.out">/app/qp/streamerserver/logs/streaming/1/nohup.out</choice>
<choice value="/app/qp/streamerserver/logs/streaming/2/nohup.out">/app/qp/streamerserver/logs/streaming/2/nohup.out</choice>
<choice value="/app/qp/streamerserver/logs/streaming/3/nohup.out">/app/qp/streamerserver/logs/streaming/3/nohup.out</choice>
<choice value="/app/qp/streamerserver/logs/streaming/4/nohup.out">/app/qp/streamerserver/logs/streaming/4/nohup.out</choice>
</input>
<input type="text" token="texttok1">
<label>Enter an error.</label>
<default>*</default>
</input>
<table>
<search>
<query>host=$hosttok1$ "ERROR" sourcetype=streamer_nohup source=$sourcetok1$| regex _raw!="WARN"| rex "(?<error>\w{5}\s+.{100})"| table _time host source error| search error="$texttok1$"</query>
<earliest>$timetok1.earliest$</earliest>
<latest>$timetok1.latest$</latest>
</search>
<option name="wrap">false</option>
<option name="rowNumbers">false</option>
<option name="dataOverlayMode">none</option>
<option name="drilldown">cell</option>
<option name="count">10</option>
</table>
</panel>
<panel>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What does the search look like when you click on the little magnifying glass at the bottom of the panel?
<query>host=$hosttok1$ "ERROR" sourcetype=streamer_nohup source=$sourcetok1$| regex _raw!="WARN"| rex "(?<error>\w{5}\s+.{100})"| table _time host source error| search error=$texttok1$</query>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content