Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Infoblox reporting splunk question: How to pull in...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, I'm using the following search string in Infoblox reporting:
sourcetype=ib:audit index=ib_audit | sort -_time | rename TIMESTAMP as "Timestamp", ADMIN as "Admin", ACTION as "Action", OBJECT_TYPE as "Object Type", OBJECT_NAME as "Object Name", EXEC_STATUS as "Execution Status", MESSAGE as "Message", host as "Member" | search Admin=* Action=Created OR Action=Deleted "Object Type"="IPv4 Network Container" OR "Object Type"="IPv4 Network" | fields + Action, Admin, Member, "Object Name", "Object Type", "Comment" Timestamp |fields - _raw, _time
This search is to alert on new network or network containers created via the audit log. What I would like to do in addition to this, is pull in the comment from the network, which looks like this from the splunk search:
2022-10-03 15:00:23.984Z [guestrw]: Created Network 192.168.100.0/24 network_view=default extensible_attributes=[[name="Building",value="B2"]],address="192.168.100.0",auto_create_reversezone=False,cidr=24,comment="DDIguy Reporting test",common_properties=[domain_name_servers=[],routers=[]],disabled=False,discovery_member=NULL,enable_discovery=False,enable_immediate_discovery=False,network_view=NetworkView:default,use_basic_polling_settings=False,use_member_enable_discovery=False
"commentDDIGUY Reporting test"
Can someone please help me understand how I can pull that into the first search query?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The following is the answer.
sourcetype=ib:audit index=ib_audit | sort -_time | rename TIMESTAMP as "Timestamp", ADMIN as "Admin", ACTION as "Action", OBJECT_TYPE as "Object Type", OBJECT_NAME as "Object Name", EXEC_STATUS as "Execution Status", MESSAGE as "Message", host as "Member" | search Admin=* Action=Created OR Action=Deleted "Object Type"="IPv4 Network Container" OR "Object Type"="IPv4 Network" |rex "comment\s(?<comment>\w+)\s" | table Admin, Action, "Object Type", "Object Name", comment
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The following is the answer.
sourcetype=ib:audit index=ib_audit | sort -_time | rename TIMESTAMP as "Timestamp", ADMIN as "Admin", ACTION as "Action", OBJECT_TYPE as "Object Type", OBJECT_NAME as "Object Name", EXEC_STATUS as "Execution Status", MESSAGE as "Message", host as "Member" | search Admin=* Action=Created OR Action=Deleted "Object Type"="IPv4 Network Container" OR "Object Type"="IPv4 Network" |rex "comment\s(?<comment>\w+)\s" | table Admin, Action, "Object Type", "Object Name", comment
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Three things:
1) As I wrote earlier - order of operations matters. So sorting the data unnecessarily makes the search slower. Especially if you don't need the data sorted. But even if you do, sort it at the end.
2) Don't use table unless you absolutely need to. it would be enough to select a set of fields using fields command. Why am I bringing this up? Because if you decide to extend this search further by appending more commands with table you move the processing to the search heads and you can't take advantage of distributed nature of Splunk environment.
3) For one-off jobs, using rex is perfectly OK, but in general case if the comment field is not extracted, it should be added to extractions for the sourcetype so it can be used easily by anyone and searching on this field can operate efficiently.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
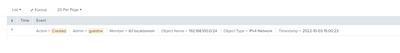
I am generating a report which includes all the networks and network containers created. This is working with the criteria I've provided. However, the "comment" isn't included and I would like it to be. I would like this line to be included in the search "comment="DDIguy Reporting test" but can't figure out how to add that into the search criteria.
I'd like to pull the highlighted bit out of this stock report and include it in the report above ^.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm not sure what you want to achieve in the end. Your search should return some fields and then what? What do you mean by "pull"? You want to search for some other events based on some set of fields returned by this search?
Anyway, get that sort to the end of your pipeline. And just search for the original fields before the rename. Splunk can be sometimes smart and optimize some things but I wouldn't count on that and it's best to be as specific as you can with your search terms.
Also it may be just my personal taste but I don't like counting on the built-in precedence on conditions - adding parentheses helps readability IMHO.
So I'd start with
sourcetype=ib:audit index=ib_audit ADMIN=* (ACTION=Created OR ACTION=Deleted) (OBJECT_TYPE="IPv4 Network Container" OR "Object Type"="IPv4 Network")
| rename TIMESTAMP as "Timestamp", ADMIN as "Admin", ACTION as "Action", OBJECT_TYPE as "Object Type", OBJECT_NAME as "Object Name", EXEC_STATUS as "Execution Status", MESSAGE as "Message", host as "Member"
| fields + Action, Admin, Member, "Object Name", "Object Type", "Comment" Timestamp
| fields - _raw, _time
| sort -_time
(I wouldn't sort if I was to do later something that doesn't rely on event order)
And then think what next.