Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to write the regex to extract added, remov...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How can i extract the added, removed, and changed file/directory and list them to a field respectively using regular expressions?
Below is the sample Splunk event.
Start timestamp: 2016-06-02 05:00:01
Summary:
Total number of files: 76478
Added files: 4
Removed files: 3
Changed files: 3
Added files:
added: /test/dir1/dir2
added: /sample/dir/test
added: /testing/splunk/test
added: /application/test/splunk
Removed files:
removed: /removed/files
removed: /test/removing/files
removed: /sample.txt
Changed files:
changed: /changed/files/sample.txt
changed: /test/app.conf
changed: /app/local.meta
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is this what you are looking for?
You can obviously ignore the first 3 lines that I used to reproduce your use case:
| stats count
| fields - count
| eval _raw = "
Start timestamp: 2016-06-02 05:00:01
Summary:
Total number of files: 76478
Added files: 4
Removed files: 3
Changed files: 3
Added files:
added: /test/dir1/dir2
added: /sample/dir/test
added: /testing/splunk/test
added: /application/test/splunk
Removed files:
removed: /removed/files
removed: /test/removing/files
removed: /sample.txt
Changed files:
changed: /changed/files/sample.txt
changed: /test/app.conf
changed: /app/local.meta
"
| rex field=_raw max_match=0 "added: (?<added>[^\n]+)"
| rex field=_raw max_match=0 "removed: (?<removed>[^\n]+)"
| rex field=_raw max_match=0 "changed: (?<changed>[^\n]+)"
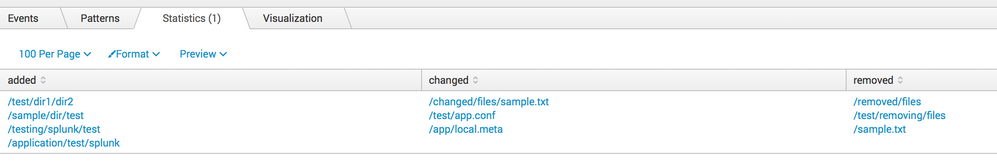
Output (see picture):
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is this what you are looking for?
You can obviously ignore the first 3 lines that I used to reproduce your use case:
| stats count
| fields - count
| eval _raw = "
Start timestamp: 2016-06-02 05:00:01
Summary:
Total number of files: 76478
Added files: 4
Removed files: 3
Changed files: 3
Added files:
added: /test/dir1/dir2
added: /sample/dir/test
added: /testing/splunk/test
added: /application/test/splunk
Removed files:
removed: /removed/files
removed: /test/removing/files
removed: /sample.txt
Changed files:
changed: /changed/files/sample.txt
changed: /test/app.conf
changed: /app/local.meta
"
| rex field=_raw max_match=0 "added: (?<added>[^\n]+)"
| rex field=_raw max_match=0 "removed: (?<removed>[^\n]+)"
| rex field=_raw max_match=0 "changed: (?<changed>[^\n]+)"
Output (see picture):