Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to use tstats and get raw last event?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to use tstats and get raw last event?
Hello,
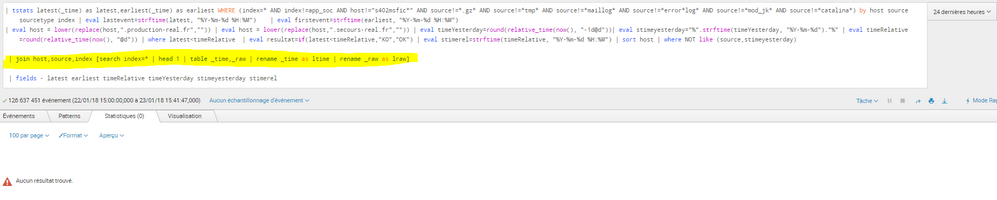
I would like to get raw last event for each source listed by tstats, how to do? I've tried tstats ... | join but no result (see attached)
Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Solved with stats
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
remove |table _time, _raw as here you are considering only two fields in results and trying to join with host, source and index
or you can replace that with |table _time, _raw, host, source, index
Let me know if it gives output...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
no result 😞
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried reverse way and it said tstats must be the first command.
table _time,host,source,index,_raw | head 1
| join host,source,index [search | tstats latest(_time) as latest,earliest(_time) as earliest WHERE (index=* by host source index | eval lastevent=strftime(latest, "%Y-%m-%d %H:%M") | eval firstevent=strftime(earliest, "%Y-%m-%d %H:%M")
| eval stimeyesterday="%".strftime(timeYesterday, "%Y-%m-%d")."%" | eval timeRelative=round(relative_time(now(), "@d")) | where latest < timeRelative | eval datacenter=if(match(host,"s303|s403|s503|s603|s703"),"N","S") | eval resultat=if(latest < timeRelative,"KO","OK") | eval stimerel=strftime(timeRelative, "%Y-%m-%d %H:%M") | sort datacenter,index,host | where NOT like (source,stimeyesterday) | fields - latest earliest timeRelative timeYesterday stimeyesterday stimerel]
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes tstats should be first command .
when you search your query starting with |tstats and ends with
|where NOT like(source,stimeyesterday)
are you getting output?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, this works. My question was about _raw data I want to show (of last event)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
so finally you are getting _raw data as expected...:)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No unfortunately 😞
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
so can you share one sample output after running:
| tstats latest(_time) as latest,earliest(_time) as earliest WHERE (index=* by host source index | eval lastevent=strftime(latest, "%Y-%m-%d %H:%M") | eval firstevent=strftime(earliest, "%Y-%m-%d %H:%M") | eval stimeyesterday="%".strftime(timeYesterday, "%Y-%m-%d")."%" | eval timeRelative=round(relative_time(now(), "@d")) | where latest < timeRelative | eval datacenter=if(match(host,"s303|s403|s503|s603|s703"),"N","S") | eval resultat=if(latest < timeRelative,"KO","OK") | eval stimerel=strftime(timeRelative, "%Y-%m-%d %H:%M") | sort datacenter,index,host | where NOT like (source,stimeyesterday)