- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to use an addcoltotals result for eval?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
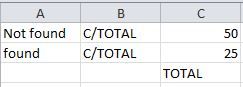
Hello dear Splunk experts 🙂
I have this in my search:
addcoltotals labelfield=fieldtosum label=TOTAL
However I would like to reuse the result of it like fieldtosum/TOTAL, how to do?
Example attached.
Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try like this
your current search | eventstats sum(fieldtosum) as TOTAL | addcoltotals labelfield=fieldtosum label=TOTAL | eval fieldtosum=fieldtosum/TOTAL
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is the search :
| multisearch [ search index="xxx" sourcetype="XXX_Search" | where NB_Result = 0 | rename NB_Result as SZERO ] [ search index="xxx" sourcetype="XXX_Search" | where NB_Result > 1 ] | stats count(AZERO) as totalsearch, count (SZERO) as totalfailed by Result | eval wresult=round(totalfailed/(totalfailed+totalsearch)*100,0) | eval ctotal=totalfailed+totalsearch | eval Searches=case(Result="null","Something", Result="YES","Yes",Result="NEAR","Near") | eventstats sum(Searches) as totalr | table Searches,totalsearch,totalfailed, ctotal, wresult, totalr
Field totalr is empty however totalr is not empty if I use eventstats sum(wresult) as totalr
So is it a problem with case?
Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is very helpful but I need to see the actual output, too, (which is what I was asking to see before). What I mean is that you obviously don't have field names A, B, and C. Your search shows that you should have 5 fields. Show your output as it really is (good and bad).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your picture does not match your search. Type it in and get the field names correct.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try like this
your current search | eventstats sum(fieldtosum) as TOTAL | addcoltotals labelfield=fieldtosum label=TOTAL | eval fieldtosum=fieldtosum/TOTAL
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It works!
I was using the wrong fieldtosum : it's ok with eventstats sum(totalsearch) as totalr