Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to sum the values of a multivalue field.?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi my query is:
index=_internal earliest=-60m@m latest=now|transaction method | table root method status bytes | nomv bytes
result for above query is:
Here, I want to sum of all the values of "bytes" field . i.e single value of bytes field for each method.
Thanks in advance
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Switch from transaction to stats. Add sourcetype/source to your query if it is applicable. _internal index contains a lot of Splunk's sourcetypes for internal purpose.
index=_internal sourcetype=* earliest=-60m latest=now
| stats values(root) as root values(status) as status sum(bytes) as bytes by method
updated to remove count as you dont seem to require eventcount or duration.
PS: This is not a use case for transaction and stats should perform better in this case.
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
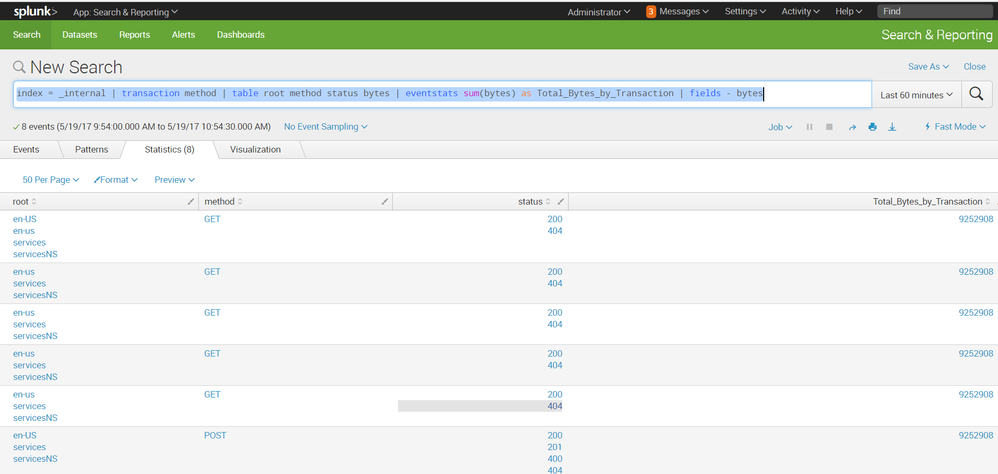
You need a unique field for each transaction in order for eventstats to give you a by-transaction sum of the bytes. If you want the total bytes associated with each transaction, then you can do this...
index=_internal earliest=-60m@m latest=now
| transaction method
| table root method status bytes
| streamstats count as tranno
| eventstats sum(bytes) as totalbytes by tranno
...then, only if you want to retain the byte details for some reason...
| nomv bytes
... or if not
| field - bytes
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This works, but I found out that you have to use mvlist=t option in transaction, otherwise, repeated values in the mv field are not accounted for. i.e.,
index=_internal earliest=-60m@m latest=now
| transaction mvlist=t method
| table root method status bytes
| streamstats count as tranno
| eventstats sum(bytes) as totalbytes by tranno
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for amazing explanation..!!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thank you for that!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Switch from transaction to stats. Add sourcetype/source to your query if it is applicable. _internal index contains a lot of Splunk's sourcetypes for internal purpose.
index=_internal sourcetype=* earliest=-60m latest=now
| stats values(root) as root values(status) as status sum(bytes) as bytes by method
updated to remove count as you dont seem to require eventcount or duration.
PS: This is not a use case for transaction and stats should perform better in this case.
| makeresults | eval message= "Happy Splunking!!!"