Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to split a table-formatted event into mult...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
davidcraven02
Communicator
02-09-2018
03:35 AM
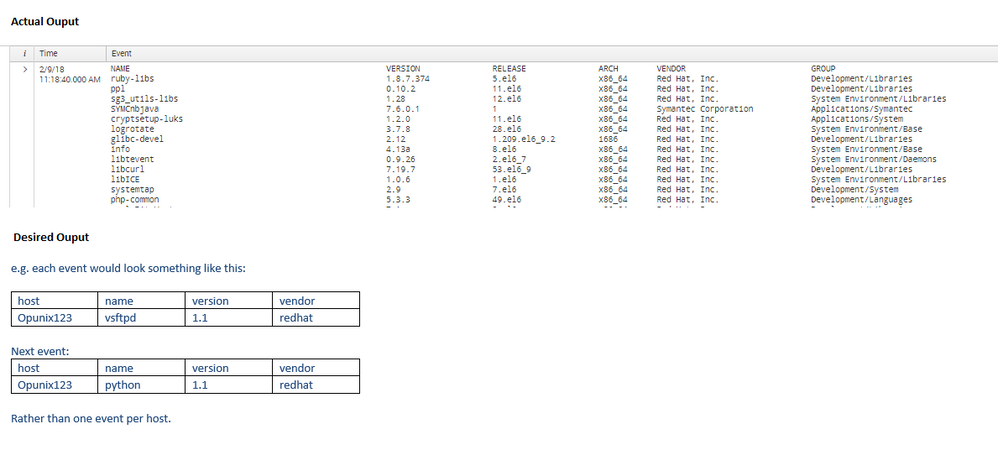
Is it possible to have each piece of software as an event of its own so that I could search for a particular item?
Could some cool regex break this up into searchable data?
Desired output in screenshot below
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yunagi
Communicator
02-09-2018
04:03 AM
To split a table-formatted event into multipe events during search time, you can use the multikv command.
Try it like this:
your search | multikv
You should get an event for each line. Each event should have the fields NAME, VERSION, RELEASE etc.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yunagi
Communicator
02-09-2018
04:03 AM
To split a table-formatted event into multipe events during search time, you can use the multikv command.
Try it like this:
your search | multikv
You should get an event for each line. Each event should have the fields NAME, VERSION, RELEASE etc.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
davidcraven02
Communicator
02-09-2018
04:38 AM
Thank you so much
Get Updates on the Splunk Community!
Stronger Security with Federated Search for S3, GCP SQL & Australian Threat ...
Splunk Lantern is a Splunk customer success center that provides advice from Splunk experts on valuable data ...
Accelerating Observability as Code with the Splunk AI Assistant
We’ve seen in previous posts what Observability as Code (OaC) is and how it’s now essential for managing ...
Integrating Splunk Search API and Quarto to Create Reproducible Investigation ...
Splunk is More Than Just the Web Console
For Digital Forensics and Incident Response (DFIR) practitioners, ...