Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to sort a column chart to view the top 10 valu...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to sort a column chart to view the top 10 values?
bogdan_nicolesc
Communicator
05-23-2019
07:08 AM
Hi,
I try to make a column chart using this search:
index=webtrafic
| rename ProcessName AS RootObject.ProcessName timestamp AS RootObject.timestamp
| fields "_time" "sourcetype" "RootObject.ProcessName" "RootObject.timestamp"
| stats dedup_splitvals=t count(RootObject.timestamp) AS "Count of timestamp" by RootObject.ProcessName
| sort limit=5 RootObject.ProcessName
| fields - _span
| rename RootObject.ProcessName AS ProcessName
| fillnull "Count of timestamp"
| fields ProcessName, "Count of timestamp"
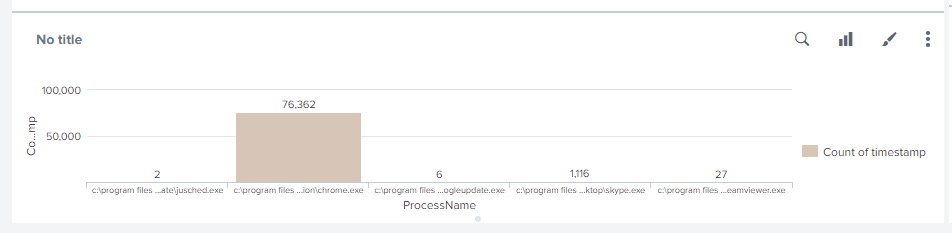
And i get this:
My question is: How can i sort columns so i can see top 5/10 highest values?
Thank you,
Bogdan
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
bogdan_nicolesc
Communicator
05-24-2019
02:17 AM
Hi marycordova,
If i use this command, i get this error:
Error in 'chart' command: The specifier 'Count of timestamp' is invalid. It must be in form (). For example: max(size).
The search job has failed due to an error. You may be able view the job in the Job Inspector.
if, however, i use this command:
(index=* OR index=_*) (index=webtrafic)
| rename ProcessName AS RootObject.ProcessName timestamp AS RootObject.timestamp
| fields "_time" "sourcetype" "RootObject.ProcessName" "RootObject.timestamp"
| stats dedup_splitvals=t count(RootObject.timestamp) AS "Count of timestamp" by RootObject.ProcessName
| sort limit=100000 RootObject.ProcessName
| fields - _span
| rename RootObject.ProcessName AS ProcessName
| fillnull "Count of timestamp"
| fields ProcessName, "Count of timestamp"
| sort -"Count of timestamp"
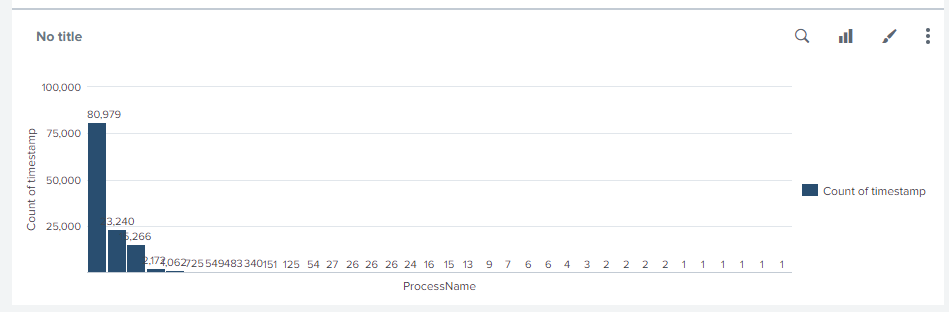
I get this:
Thank you.
Bogdan
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
marycordova

SplunkTrust
05-23-2019
10:52 AM
index=webtrafic
| stats dedup_splitvals=t count(timestamp) AS "Count of timestamp" by ProcessName
| fillnull "Count of timestamp" value="0"
| sort - "Count of timestamp"
| head 5
| chart "Count of timestamp" by ProcessName
@marycordova
Get Updates on the Splunk Community!
Splunk Mobile: Your Brand-New Home Screen
Meet Your New Mobile Hub
Hello Splunk Community!
Staying connected to your data—no matter where you are—is ...
Introducing Value Insights (Beta): Understand the Business Impact your organization ...
Real progress on your strategic priorities starts with knowing the business outcomes your teams are delivering ...
Enterprise Security (ES) Essentials 8.3 is Now GA — Smarter Detections, Faster ...
As of today, Enterprise Security (ES) Essentials 8.3 is now generally available, helping SOC teams simplify ...