Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to setup a search where we look for single sou...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I am trying to setup a search where we look for single source IP's hitting multiple destination IP's on our firewall.
1. When I do a search, I get TONS of results for destinations, but I want to limit the destination results to only show a few sample set.
2. I also have results showing up which only show one destination IP, which we do not want.
The search I am using as an example is
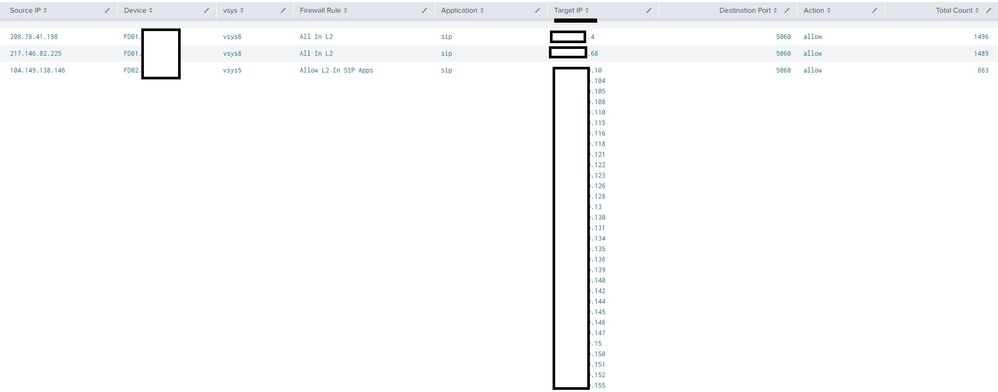
index=pan_logs eventtype=pan_traffic dvc="FD0*.*" action=allow OR action=allowed OR action=alert app=sip OR dest_port=5060 OR dest_port=5061 AND src_ip!=10.0.0.0/8 AND src_ip!=172.16.0.0/12 AND src_ip!=192.168.0.0/16 | stats values(rule) values(dest_ip) values(dest_port) count by src_ip vendor_action app dvc vsys | sort bt count desc limit=10 | sort dest_ip | where count > 500 | fields src_ip dvc vsys values(rule) app values(dest_ip) values(dest_port) vendor_action count | rename src_ip AS "Source IP", vendor_action AS "Action", values(rule) AS "Firewall Rule", values(dest_ip) AS "Target IP", values(dest_port) AS "Destination Port", count AS "Total Count", dvc AS "Device", app AS "Application" | head 20
Example search result
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
highest count at the top to the lowest.
My mistake in the sort command. (Forgot I renamed 'count'.)
index=pan_logs eventtype=pan_traffic dvc="FD0*.*" action=allow OR action=allowed OR action=alert app=sip OR dest_port=5060 OR dest_port=5061 AND src_ip!=10.0.0.0/8 AND src_ip!=172.16.0.0/12 AND src_ip!=192.168.0.0/16
| stats values(rule) AS "Firewall Rule" values(dest_ip) AS dest_ip values(dest_port) AS "Destination Port" dc(dest_ip) as dest_count count as "Total Count" by src_ip vendor_action app dvc vsys
| where 'Total Count' > 500 AND dest_count > 5
| sort - "Total Count" dest_count
| eval range = mvrange(0, if(dest_count < 10, dest_count - 1, 9))
| eval dest_ip = mvmap(range, mvindex(dest_ip, range))
| fields src_ip dvc vsys "Firewall Rule" app "Destination Port" vendor_action "Total Count"
| rename src_ip AS "Source IP", vendor_action AS "Action", dvc AS "Device", app AS "Application", dest_ip AS "Sample Target IP", dest_count as "Target Count"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I got it working. Thank you very much.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see these are Palo Alto logs. I suppose you have a lot of them and searching takes time.
You might look into using accelerated datamodels to get your results relatively quickly.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
On the second point, dc(dest_ip) will allow you to only look at multiple-destination events. (The following example looks at 5+ destinations. On the first, combine mvcount, mvmap, and mvindex. (The following example samples up to 10 destinations.)
index=pan_logs eventtype=pan_traffic dvc="FD0*.*" action=allow OR action=allowed OR action=alert app=sip OR dest_port=5060 OR dest_port=5061 AND src_ip!=10.0.0.0/8 AND src_ip!=172.16.0.0/12 AND src_ip!=192.168.0.0/16
| stats values(rule) AS "Firewall Rule" values(dest_ip) AS dest_ip values(dest_port) AS "Destination Port" dc(dest_ip) as dest_count count as "Total Count" by src_ip vendor_action app dvc vsys
| where 'Total Count' > 500 AND dest_count > 5
| sort - count dest_count
| eval range = mvrange(0, if(dest_count < 10, dest_count - 1, 9))
| eval dest_ip = mvmap(range, mvindex(dest_ip, range))
| fields src_ip dvc vsys "Firewall Rule" app "Destination Port" vendor_action "Total Count"
| rename src_ip AS "Source IP", vendor_action AS "Action", dvc AS "Device", app AS "Application", dest_ip AS "Sample Target IP", dest_count as "Target Count"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much. That worked. Now I am trying to figure out how to display the results with the highest count at the top to the lowest.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
highest count at the top to the lowest.
My mistake in the sort command. (Forgot I renamed 'count'.)
index=pan_logs eventtype=pan_traffic dvc="FD0*.*" action=allow OR action=allowed OR action=alert app=sip OR dest_port=5060 OR dest_port=5061 AND src_ip!=10.0.0.0/8 AND src_ip!=172.16.0.0/12 AND src_ip!=192.168.0.0/16
| stats values(rule) AS "Firewall Rule" values(dest_ip) AS dest_ip values(dest_port) AS "Destination Port" dc(dest_ip) as dest_count count as "Total Count" by src_ip vendor_action app dvc vsys
| where 'Total Count' > 500 AND dest_count > 5
| sort - "Total Count" dest_count
| eval range = mvrange(0, if(dest_count < 10, dest_count - 1, 9))
| eval dest_ip = mvmap(range, mvindex(dest_ip, range))
| fields src_ip dvc vsys "Firewall Rule" app "Destination Port" vendor_action "Total Count"
| rename src_ip AS "Source IP", vendor_action AS "Action", dvc AS "Device", app AS "Application", dest_ip AS "Sample Target IP", dest_count as "Target Count"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One last thing,
Is there a way to show the total number of destinations that a source IP is hitting instead of a list of ALL the destination IP's?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In my pseudo code,
| stats ... dc(dest_ip) as dest_count by src_ip ...
...
| rename ... dest_count as "Target Count"gives the number of dest_ip per src_ip. The code should only list up to 10 in "Sample Target IP" field. If you don't need the sampling, just remove codes related to values(dest_ip).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I figured it out. Thank you so much
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
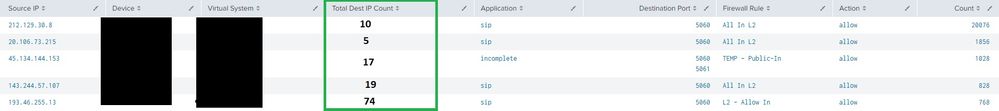
I am basically trying to accomplish the following now. Screenshot attached (Example in green)
I want a count of how many IP's the source is hitting and to now show the IP's, just a count.
index=pan_logs eventtype=pan_traffic dvc="FD0*.*" action=allow OR action=allowed OR action=alert app=sip OR dest_port=5060 OR dest_port=5061 AND src_ip!=10.0.0.0/8 AND src_ip!=172.16.0.0/12 AND src_ip!=192.168.0.0/16 AND src_zone=*-untrust | stats values(rule) AS "Firewall Rule" values(dest_port) AS "Destination Port" dc(dest_ip) as dest_count count as "Total Count" by src_ip vendor_action app dvc vsys_name | sort by "Total Count" desc limit=10 | where 'Total Count' > 500 AND dest_count > 5 | eval range = mvrange(0, if(dest_count < 10, dest_count - 1, 5)) | eval dest_ip = mvmap(range, mvindex(dest_ip, range)) | fields src_ip dvc vsys_name dest_ip app "Destination Port" "Firewall Rule" vendor_action "Total Count" | rename src_ip AS "Source IP", vendor_action AS "Action", dvc AS "Device", vsys_name AS "Virtual System", app AS "Application", dest_ip AS "Total Dest IP Count", "Total Count" AS "Count"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If destination IPs are not of interest at all, you can greatly simplify by eliminating calculations related to values(dest_ip).
index=pan_logs eventtype=pan_traffic dvc="FD0*.*" action=allow OR action=allowed OR action=alert app=sip OR dest_port=5060 OR dest_port=5061 AND src_ip!=10.0.0.0/8 AND src_ip!=172.16.0.0/12 AND src_ip!=192.168.0.0/16 AND src_zone=*-untrust
| stats values(rule) AS "Firewall Rule" values(dest_port) AS "Destination Port" dc(dest_ip) AS "Total Dest IP Count" count as Count by src_ip vendor_action app dvc vsys_name
| where Count > 500 AND 'Total Dest IP Count' > 5
| sort limit=10 - Count
| fields src_ip dvc vsys_name "Total Dest IP Count" app "Destination Port" "Firewall Rule" vendor_action Count
| rename src_ip AS "Source IP", vendor_action AS "Action", dvc AS "Device", vsys_name AS "Virtual System", app AS "Application"In the above, I switched the "sort limit=10 - Count" to after "where" clause because it is slightly more efficient. (Note sort doesn't use "by" or "desc" in syntax.)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Basically the Total Count should be highest at top and then to the lowest count.
The search works great, but the order of the results are out of order. I need them Highest count to lowest.