Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to replace a value of a field with other v...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
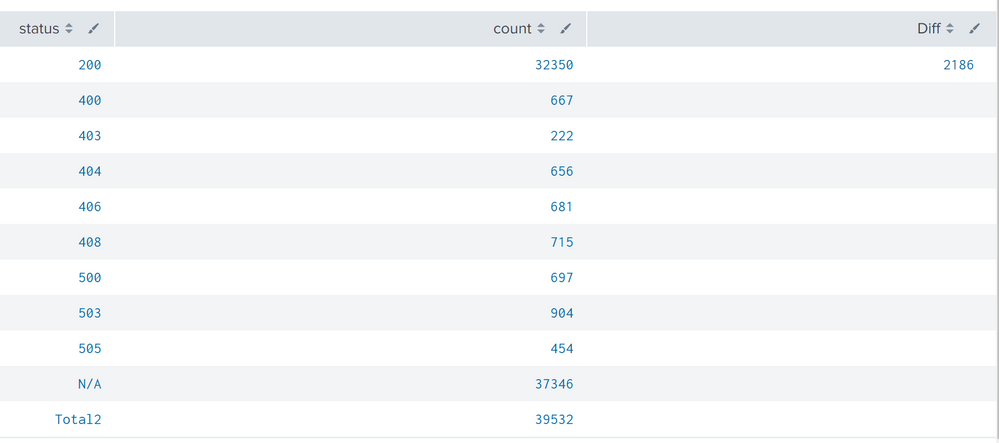
I have a splunk query which gives below tabular results in snap. But I want to replace the values of "count" field for Status="N/A" with the "Diff" field values. Values are dynamic and changes everytime. My query looks like this, I am trying to bring totals using two search queries and appending with the main search which brings column totals.
Can you advise on this or any better query which populates the results in the similar tabular format.
index=work sourcetype="access_combined_wcookie" Mozilla | stats count by status | addcoltotals count labelfield=status label=N/A
| append [search index=work sourcetype="access_combined_wcookie" | stats count | addcoltotals count labelfield=status label=Total2 | where isnotnull(status) ]
| appendcols [search index=work sourcetype="access_combined_wcookie" Mozilla |stats count by status| stats sum(count) as Total1 ]
| appendcols [search index=work sourcetype="access_combined_wcookie" | stats count as Total2 ]
| eval Diff=(Total2-Total1)
| fields - Total1, Total2
Thanks in Advance
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think for your search, you could just add something like this at the end.
... | filldown Diff | eval count = if(status = "N/A",Diff,count)
But I think this search is doing a lot of work to get where you going. It's a little hard to determine exactly what you're trying to do, but it looks like a status count for Mozilla events, along with a count of non-Mozilla events with a status of "N/A", and then a total count of events called Total2?
So maybe something like this (not at all tested)?
index=work sourcetype="access_combined_wcookie"
| eval status = if(match(_raw,"(?i)mozilla"),"N/A",status)
| stats count by status
| addcoltotals count labelfield=status label="Total2"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think for your search, you could just add something like this at the end.
... | filldown Diff | eval count = if(status = "N/A",Diff,count)
But I think this search is doing a lot of work to get where you going. It's a little hard to determine exactly what you're trying to do, but it looks like a status count for Mozilla events, along with a count of non-Mozilla events with a status of "N/A", and then a total count of events called Total2?
So maybe something like this (not at all tested)?
index=work sourcetype="access_combined_wcookie"
| eval status = if(match(_raw,"(?i)mozilla"),"N/A",status)
| stats count by status
| addcoltotals count labelfield=status label="Total2"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks a lot, it worked for me. Even the second query is bringing my results.