Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to remove this signal "-" and "OTHER" in resul...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
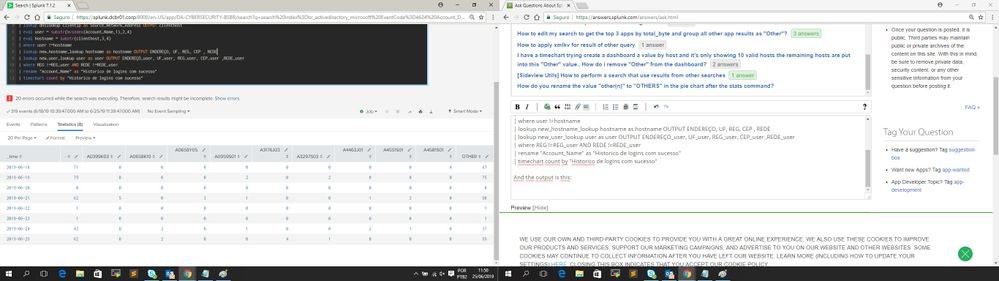
Hi Splunkers, I have this search bellow:
index=br_activedirectory_microsoft EventCode=4624 Account_Domain=AGBANESPA Account_Name=A* earliest=-169h latest=now()
| fields Account_Domain, Account_Name, Source_Network_Address
| dedup Account_Domain, Account_Name, Source_Network_Address
| lookup dnslookup clientip as Source_Network_Address OUTPUT clienthost
| eval user = substr(mvindex(Account_Name,1),2,4)
| eval hostname = substr(clienthost,3,4)
| where user !=hostname
| lookup new_hostname_lookup hostname as hostname OUTPUT ENDEREÇO, UF, REG, CEP , REDE
| lookup new_user_lookup user as user OUTPUT ENDEREÇO_user, UF_user, REG_user, CEP_user ,REDE_user
| where REG !=REG_user AND REDE !=REDE_user
| rename "Account_Name" as "Historico de logins com sucesso"
| timechart count by "Historico de logins com sucesso"
And the output is this: