Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to merge and map two splunk multi value fi...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to merge and map two splunk multi value fields and creating a seperate field?
Hi All,
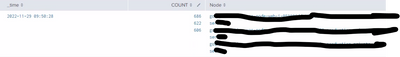
We have below data extracted in splunk and the ask is , in the "Node" field we need to make first two values as one value, next two values as one value and so on and map these values to the corresponding COUNT value.
For Eg: in the first row in "Node" field , we need to create three separate values of consecutive two values and map these values to corresponding COUNT value.
expected result:
COUNT Node
682 gol************,ser****
---------------------------------------------------------
622 gol************,ser****
----------------------------------------------------------
606 gol************,ser****
Note: *********** is just for masking not the requirement. Only above format is the requirement.
COUNT and Node are multi value fields and we need single value fields in above format
Can someone please help me in achieving this. I have spent 2 days and not getting the solution.
Any help would be appreciated a lot.
Thanks,
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'd try looking into your pipeline somewhere earlier. With multivalued fields there is no guarantee that the results from one fields will be in the order corresponding to the other field.
Is this a result of some summarization command or you're getting the data as some ugly json/xml which gets parsed this way?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
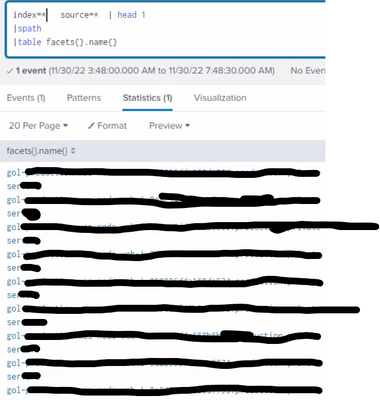
index=*
source=*
|rename facets{}.total.results{}.count AS COUNT,facets{}.name{} as Node
|table _time,COUNT,Node
Above is the simple SPL i'm using.
As you mentioned the data is json/xml which gets parsed this way.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'd try parsing the fields differently (spath and mvsplit?) so it doesn't aggregate as much. Because as I said - there is no guarantee on the order and contents of multivalued fields so even if you did some mvfunctions() magic in order to get the values, it will fall apart completely if for some reason you had one value missing or you had them reordered or whatever.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
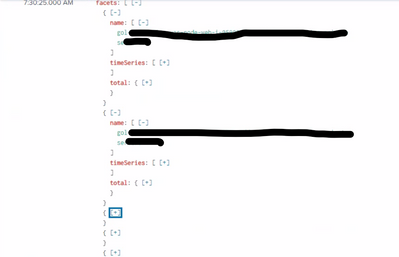
This how the data is coming into splunk. gol********* and serv******** are coming in as multiple values in a single field. Where as our requirement is to capture them as single field and corresponding count in "total" element.
Like this in facets there are more facets.name entries and corresponding count which we need to extract. But when we use auto extracted field below is what we are getting all in facets.name values captured as multivalue filed. Whereas we need seperate row for each facets.name entry.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can use spath to "pick out" separate parts of the main json. This way you can do a multivalued field with the "subjsons". Something akin to this (run anywhere example):
| makeresults
| eval json="{\"a\":[{\"b\":\"c\"},{\"b\":\"e\"}]}"
| spath input=json path="a{}" output=a
| mvexpand a
| spath input=a
This is of course a very simple json but you can similarily "untangle" much more complicated structures so you get each substructure into a separate event.