Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Limit the number of characters in a field in a...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello community,
I have a problem with my research. My searches are then sent to Splunk OnCall to manage alerts.
However, I noticed that some fields in my request can sometimes have a lot of characters, and in this case, the information does not go to Splunk OnCall.
The large number of characters is not useful and I would like to limit the number so that it does not block towards Splunk OnCall. I therefore seek to limit the number of characters in a field of my request, whatever the result. I came across this post (https://community.splunk.com/t5/Splunk-Search/Limit-length-of-field-of-characters-in-search-results/...) but the command does not work.
Here is an example request:
index=my_index state=* | fields hostname service_description output state
It is the "output" field that I would like to limit. Based on the link above, I wrote:
index=my_index state=* | fields hostname service_description output state | eval output=substr(output,1,15)
But that doesn't fix it.
Do you have any idea where I should dig for this?
FYI, I'm on Enterprise 8.2.3
Thank you in advance
Rajaion
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI @Rajaion,
did you tried to invert the command order?
I tried the following search and it's running
index=_internal
| eval event_message=substr(event_message,1,15)
| table event_messageCiao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello,
Indeed, I was not very precise. What I meant was that despite adding the fix, I still have more than 15 characters in my "output" field.
I haven't tested the use of a table (but I don't see what it represents either) because as it stands, with the exception of the "output" field which is sometimes too long, what I have is enough to send the info to Splunk OnCall.
Best regards,
Rajaion
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI @Rajaion,
did you tried to invert the command order?
I tried the following search and it's running
index=_internal
| eval event_message=substr(event_message,1,15)
| table event_messageCiao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello,
Indeed, by putting the provision that you indicate to me, I have a result which corresponds to the cutting.
Thank you for your help. I still have to check that this is not a problem for sending to Splunk OnCall now.
I'll keep you posted on progress.
Best regards,
Rajaion
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Rajaion
ok, good for you, tell me if I can help you more, otherwise, please, accept my answer for the other people of Community.
Ciao and happy splunking
Giuseppe
P.S.: Karma Points are appreciated 😉
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello
I come back with news.
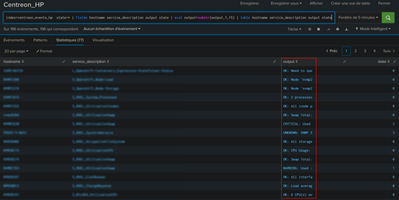
After a night of letting the query run, I confirm that we have the expected cut in the "table" display:
I cut to 15, it's not usable but it was to see how it works.
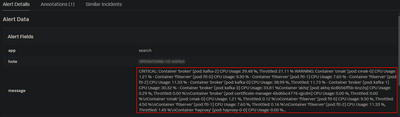
The less good news is that when sending to Splunk OnCall, the cut is not supported and I still have my potentially too long output:
I feel like Splunk OnCall doesn't handle the "table" part and therefore doesn't support clipping.
Do you know another way to cut the size of a field without using "table"?
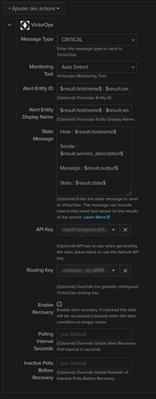
The problem can also come from the way I configured my alert sending (configured when the "table" part did not exist). Maybe there is something more to add? I provide a screen of my configuration:
Best regards,
Rajaion
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Rajaion,
did yu tried to use both table and fields?
something like this?
index=_internal
| eval event_message=substr(event_message,1,15)
| table event_message
| fields event_messageCiao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Rajaion,
what doi you mean with "But that doesn't fix it" what's the result, have you more than 15 chars?
Did you tried to use table instead fields?
Ciao.
Giuseppe