- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to get the event count for the last 24 hours a...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can you please tell us, how to get the last 24 hours event count to schedule the report?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Save you splunk search.
- Click on Settings -> Searches and Reports -> [your saved search]
- Schedule it.
If you want count of all events in the last 24 hours you could try this:
* earliest=-24h latest=now | stats count (searches the default index only)
If you want the event count for specific search try this:
[your splunk search] earliest=-24h latest=now| stats count
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Save you splunk search.
- Click on Settings -> Searches and Reports -> [your saved search]
- Schedule it.
If you want count of all events in the last 24 hours you could try this:
* earliest=-24h latest=now | stats count (searches the default index only)
If you want the event count for specific search try this:
[your splunk search] earliest=-24h latest=now| stats count
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
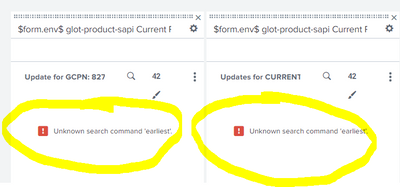
Hello, I tried using the 'earliest' option and I'm getting this error
<search>
<query>index="mulertf" "$form.env$-glot-product-sapi-v1" AND "Before updating data for GCPN:" |earliest=-24h latest=now | stats count</query>
</search>