Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to get a count of all of the events in all dat...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to get a count of all of the events in all datamodels with tstats?
Hi, I am trying to get a list of datamodels and their counts of events for each, so as to make sure that our datamodels are working.
I have got a list of the datamodels here:
| datamodel | spath input=_raw output=datamodelname path="modelName" | table datamodelname
However, when I append the tstats command onto this, as in here, Splunk reponds with no data and "datamodel 'datamodelname' not found".
| tstats count from datamodel=datamodelname
I am guessing that the "datamodel" parameter in tstats should be a literal and not a variable field? If so, how do I execute this?
Kindest regards,
BlueSocket
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I stumbled across this while seeking a solution this week. I came up with something pretty similar to @patrickp_splunk . With a slight change. I kicked things into json before it comes out of the map command (because `map` only allowed me to bring back one field).
| datamodelsimple \
| map maxsearches=500 search="| tstats count FROM datamodel=$datamodel$ | eval dmName=\"$datamodel$\"
| tojson | fields - count,dmName" | extract | table dmName,count
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a very dumb solution, but I was looking for a quick and dirty way to see the numbers. Maybe this might spark another idea with someone else.
I amended the search and did this:
| datamodel
| spath input=_raw output=datamodelname path="modelName"
| table datamodelname
| map search="|tstats count($datamodelname$) count from datamodel=$datamodelname$"
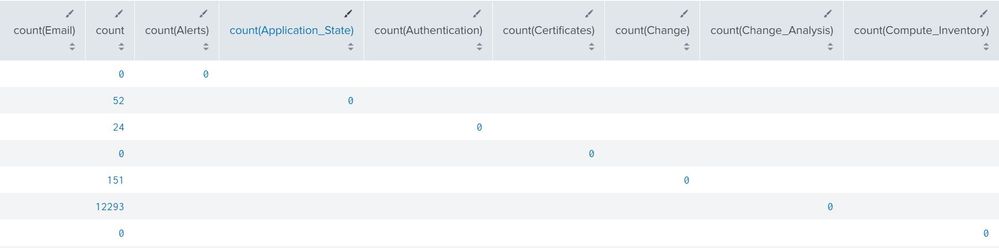
So this gave me this table:
Match the zero to the count table, and you get the number of events.
Again, I know it's a lame way to do it, but it works for my intents.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are probably going to want to use a map command based upon the output of the initial command. I don't have one handy, but I'll check and see if I can put one together when i get a chance, if no one has solved this for you by then.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks - I got a bit further, but not quite there with this query:
| datamodel | spath input=_raw output=datamodelname path="modelName" | table datamodelname | map search="|tstats count from datamodel=$datamodelname$ | eval datamodel=$datamodelname$ | table datamodel, count"
And I get this:
datamodel count
---------------- --------
1928
I get the index and the count, but not the datamodel in the table. I am looking for:
datamodel count
---------------- --------
security 1928
I tried:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi BlueSocket,
I know this is a pretty old thread, but I stumbled upon the same question today.
You almost had the solution yourself. You only missed escaped quotes.
| datamodel | spath input=_raw output=datamodelname path="modelName" | table datamodelname | map search="|tstats count from datamodel=$datamodelname$ | eval datamodel=\"$datamodelname$\" | table datamodel, count"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is what I have thus far. You have to specify the datamodel (which is fine as I'm not using all of them) but I can't seem to find the name of the field that has the datamodel name either.
| tstats summariesonly=t min(_time) as min, max(_time) as max count from datamodel=Web
| append
[| tstats summariesonly=t min(_time) as min, max(_time) as max count from datamodel=Malware]
| append
[| tstats summariesonly=t min(_time) as min, max(_time) as max count from datamodel=Intrusion_Detection ]
| eval "Start time"=strftime(min, "%c")
| eval "End time"=strftime(max, "%c")
| eval "Event count" = count
| fields "Start time" "End time" "Event count"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can't believe that no one has got an idea about this (and there have been 55 views with 44 people following this question)!