Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to filter out few data showing up from my sear...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello team,
My search string is as below:
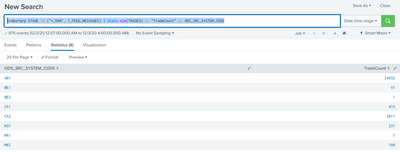
index=qrp STAGE IN ("*_RAW", T_FEED_MESSAGES) | stats sum(TRADES) as "TradeCount" by ODS_SRC_SYSTEM_CODE
And the result screenshot is above. The AR1, BE1 ect are source system codes and the numerical values for each source system in the rows are the aggregate trade counts for respective source system at the time span starting from 00:00:00 hours till 05:00:00 hours. However for source systems like BE2 and MA1 the count doesn't alter all through the day and is always 1.
Now when I want to custom trigger a notification alert using this search string when threshold value of trade counts for each individual source system is less than 10 at 08:00:00 then by default always BE2 and MA1 comes up in alert. Hence if I only want to exclude these two source system and take rest into consideration while setting up my custom trigger notification. How to achieve this?
Kindly help me with your valuable inputs.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=qrp STAGE IN ("*_RAW", T_FEED_MESSAGES) | stats sum(TRADES) as "TradeCount" by ODS_SRC_SYSTEM_CODE | search ODS_SRC_SYSTEM_CODE!="BE2" OR ODS_SRC_SYSTEM_CODE!="MA1" | where TradeCount < 10
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=qrp STAGE IN ("*_RAW", T_FEED_MESSAGES) | stats sum(TRADES) as "TradeCount" by ODS_SRC_SYSTEM_CODE | search ODS_SRC_SYSTEM_CODE!="BE2" OR ODS_SRC_SYSTEM_CODE!="MA1" | where TradeCount < 10