Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to exclude results in search?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
alexspunkshell
Contributor
09-21-2022
11:12 AM
I want to exclude duration results if greater than 7 days. So i used search NOT but it is not working.
Can someone help here?
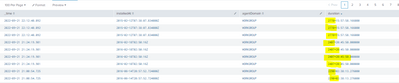
Query
index=sentinelone | eval duration=tostring(now()-strptime(installedAt,"%Y-%m-%dT%H:%M:%S.%6N"),"duration") | table _time installedAt agentDomain duration |search installedAt!="Null"
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yuanliu

SplunkTrust
09-21-2022
11:41 AM
Something like
index=sentinelone installedAt!="Null"
| eval duration=now()-strptime(installedAt,"%Y-%m-%dT%H:%M:%S.%6N")
| eval duration=if(duration < 7 * 86400, tostring(duration, "duration"), null())
| table _time installedAt agentDomain durationNote your last search is based on a field that already exists in raw data. Moving it to the base search is more efficient.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yuanliu

SplunkTrust
09-21-2022
11:41 AM
Something like
index=sentinelone installedAt!="Null"
| eval duration=now()-strptime(installedAt,"%Y-%m-%dT%H:%M:%S.%6N")
| eval duration=if(duration < 7 * 86400, tostring(duration, "duration"), null())
| table _time installedAt agentDomain durationNote your last search is based on a field that already exists in raw data. Moving it to the base search is more efficient.
Get Updates on the Splunk Community!
[Puzzles] Solve, Learn, Repeat: Dynamic formatting from XML events
This challenge was first posted on Slack #puzzles channelFor a previous puzzle, I needed a set of fixed-length ...
Enter the Agentic Era with Splunk AI Assistant for SPL 1.4
🚀 Your data just got a serious AI upgrade — are you ready?
Say hello to the Agentic Era with the ...
Stronger Security with Federated Search for S3, GCP SQL & Australian Threat ...
Splunk Lantern is a Splunk customer success center that provides advice from Splunk experts on valuable data ...