Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to edit my search to identify blocked network ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
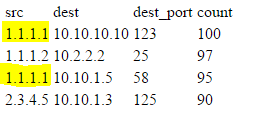
I am trying to identify worst offenders for blocked traffic and then identify all of the locations they are getting blocked. In my basic search index=cisco_asa action=blocked | top limit=30 src, dest, dest_port I am seeing results example:
Examples of outputs:
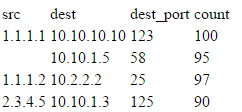
What i'm trying to do is get a list of all blocked events for a given source IP, and based on all blocked events, sort the top 25 offenders, and then list out each destination that machine is getting blocked events on. Something similar to this, preferably with the total count somewhere in the results:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there, try this.
... | stats count by dest dest_port src | stats list(dest) as dest, list(dest_port) as destPort, list(count) as count by src as Offender
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there, try this.
... | stats count by dest dest_port src | stats list(dest) as dest, list(dest_port) as destPort, list(count) as count by src as Offender
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
while this didn't get me what I was looking for, it got me in the right direction:
index=cisco_asa action=blocked | top limit=30 src, dest, dest_port | stats list(dest) as dest, list(dest_port) as destPort, list(count) as count by src | sort -count
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oh I see, I forget that | top limit=30 ... my bad. Glad It works tho