Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to edit my search to get the sum event cou...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to edit my search to get the sum event counts within a 4 minute window?
Hello,
I have the following data (this is the result of a transaction):
Date Hour Paypload event count SumCountDuring4Minutes
2015-01-01 13-21-112 azearzer 4
2015-01-01 13-21-008 azearzer 1
2015-01-01 13-22-220 azearzer 2
2015-01-01 13-23-100 azearzer 1
2015-01-01 13-31-100 azearzer 3
(I enclosed a more readable image of the log)
I need to have the sum of eventcount in a 4 minute window. I have seen that the streamstats function can use a window with a number of events. In my case, dealing with events has no meaning since the events may occur after 10 minutes of inactivity.
So in a perfect world, I would like to do simply:
transaction Data Payload | streamstats sum(eventcount) window=4m as SumCountDuring4Minutes
or in an other perfect world
transaction Data Payload | streamstats sum(eventcount) start=Hour end=Hour+4m as SumCountDuring4Minutes
I have understood that this is not possible with the current implementation of streamstats because the argument windows takes a number of event.
I have very little "SPLUNK knowledge" and I do not see an other way to perform that.
I read about the bucket command, but I am not sure that grouping event by time with allow me to get the SumCountDuring4Minutes per event. My understanding is that I would get a SumCountDuring4Minutes every 4 minutes.
Regards
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello ppablo,
I enclose my image in this answer. On my side it is displayed correctly in my browser as it was also the previous times.
Last times the url adress was : https://answers.splunk.com/storage/temp/65197-log-slidingsum.png
After a fews days, the image is not displayed any more in my browser.
And I have the feeling that I have been the only one to be able to see this image in my answer.
This time the image is here:/storage/temp/65254-log-slidingsum.png
Regards
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi clorne,
if I get you correct, you can use stats and bucket to get what you want.
Perfect world example 1:
transaction Data Payload | bucket _time span=4min | stats sum(eventcount) AS SumCountDuring4Minutes BY _time
or in an other perfect world example 2:
transaction Data Payload earliest=-64min latest=-60min | stats sum(eventcount) AS SumCountDuring4Minutes
Example 1 will return sum over 4 minutes, but based on the time range of your base search. If the time range is more than 4 minutes you will get multiple sum.
Example 2 will return one sum over 4 minutes one hour ago.
Hope this helps and makes some sense ...
cheers, MuS
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, For some reason, I am able to upload the image and it is displayed during a few days.
After 4-5 days, I receive an email saying that this I have updated the answer and when I look my imlage has been removed.
Splunk administrator ?Am I authorized to upload an image ?
Regards
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @clorne
You posted the image as an answer originally, so I just converted it to a comment under @MuS's answer. Your image hasn't been removed. Do you not see the image in your comment above? I see an image with columns hour, payload, eventcount, SumEventCountDuring4Minutes, and Time interval used for the sum. Is that the image you're talking about?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is the image again:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
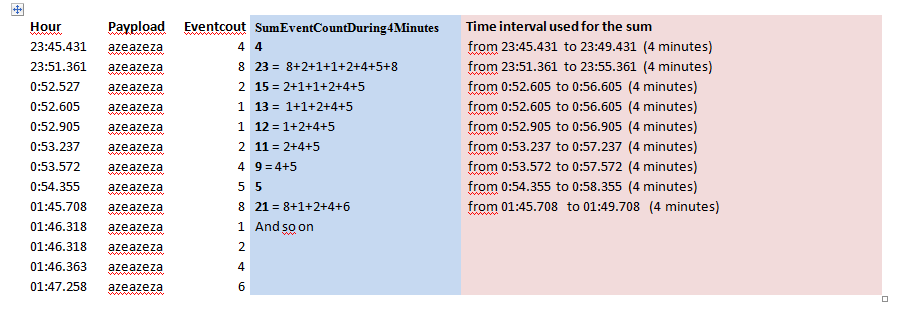
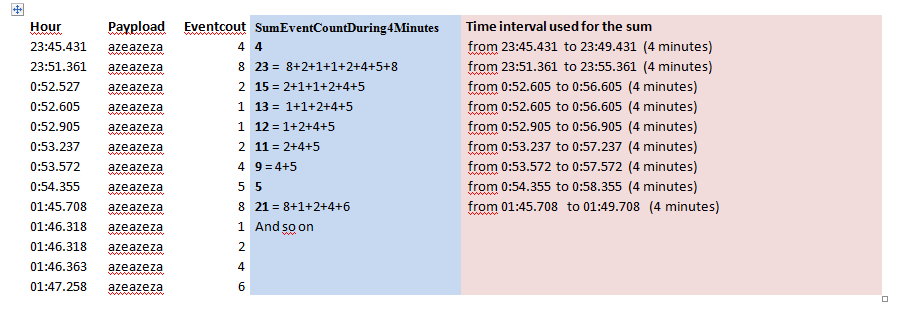
Hello MuS,
I created a new log sample in order to explain better the calculation I want to perform.!
In the blue column is what I want to get => a sum during 4 minutes for each event
In the pink column is the interval time ( 4 minutes).
Regards
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi clorne, the image is broken or missing
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Mus,
Thanks for your reply. I tested your suggestion; Unfortunately, I encountered what I was thinking.
There is a sum that is calculated every 4 minutes and not every event during 4 minutes.
Therefore for exemple, when I have 100 events to process, I got only 80 sums
I really think that is a limitation of Splunk today.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm still not 100% clear what you expect as result....
Have you tried head ?
transaction Data Payload | head limit=100 | stats sum(eventcount) AS SumCountDuring4Minutes
This will limit the result to 100 events...