Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to edit my "rex" search in order to extrac...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Another regular expression/rex field extraction question: How do I get USERID between timestamp and '@JavaClient' ?
- Does USERID always have to begin with
(?<and end with>.*)? - What syntax represents all of these to use rex command ?
- number, integer, and digit
- date time (specific format? )
- letter
- special characters
Currently, I have it like this but it's not returning XBATCH, and ABCSRV
| rex field=_raw "\.\d\d\d\s(?.*)\@JavaClient\s"
Raw data
PSAPPSRV.3204 (770) [2017-01-12T15:00:32.028 XBATCH@JavaClient IntegrationSvc](3) Returning context. ID=XBATCH, Lang=ENG, UStreamId=150032028_3204.770, Token=DU_CS/2017-01-12-09.00.31.708254/XBATCH/ENG/B82gf3Amj/f5Lx/k1J4f6t9RRtI=
PSAPPSRV.3204 (771) [2017-01-12T15:01:02.551 GetCertificate](3) Returning context. ID=SRBTTRAN, Lang=ENG, UStreamId=150102551_3204.771, Token=DU_CS/2017-01-12-09.01.02.708281/SRBTTRAN/ENG/o0fY1oj0zd5Es1vl3xMOnUaB5t0=
PSAPPSRV.3204 (785) [2017-01-12T15:01:05.037 ABCSRV@JavaClient IntegrationSvc](3) Processing WssecIsAuthenticatedUser command. CtxUser=ABCSRV/ENG, SwUser=XBATCH/+
PSAPPSRV.3204 (785) [2017-01-12T15:01:05.037 ABCSRV@JavaClient IntegrationSvc](3) Processing SwitchUser command. CtxUser=ABCSRV/ENG, SwUser=DPRBATCH/+, SwConnInfo=-, SwToken=-
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
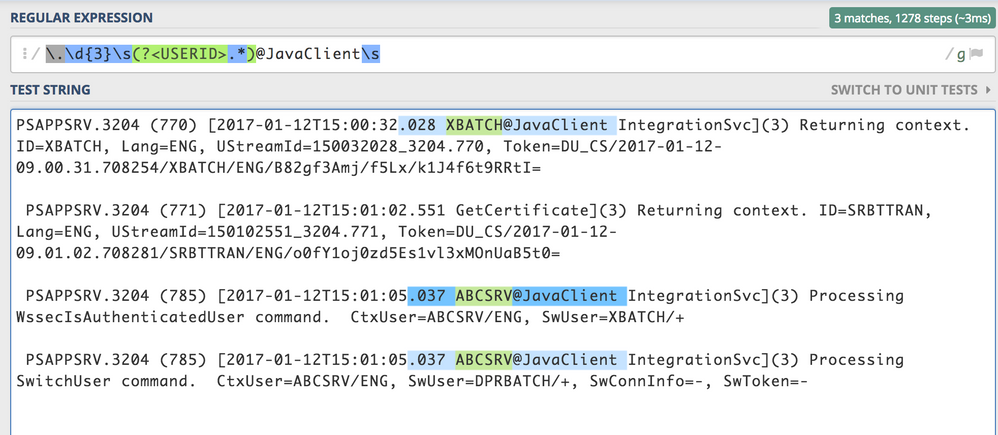
So it seems to work here for all the examples you provided. Now if you put exactly what I have here in the quotes of the rex command and it still isn't correctly pulling. Then pick out some events that aren't correctly pulling it and add them so I can see whats wrong with the regex.
This is the tool I use to test my regex out. https://regex101.com/
EDIT: Note the text highlighted in green is what regex is saying is getting captured by the capture group. And that group is given the name USERID.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So it seems to work here for all the examples you provided. Now if you put exactly what I have here in the quotes of the rex command and it still isn't correctly pulling. Then pick out some events that aren't correctly pulling it and add them so I can see whats wrong with the regex.
This is the tool I use to test my regex out. https://regex101.com/
EDIT: Note the text highlighted in green is what regex is saying is getting captured by the capture group. And that group is given the name USERID.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
the link is very useful. Thank you!
These are data that don't work out. I can't upload screenshot because i don't have karma points 😞
PSAPPSRV.152 (132) 2017-01-13T10:28:59.614 DPRBATCH@JavaClient IntegrationSvc Returning context. ID=DPRBATCH, Lang=ENG, UStreamId=102859614_152.132, Token=DU_CS/2017-01-13-04.28.59.519666/DPRBATCH/ENG/jOYUAqpyw2rafErYxid/+2tm8gY=
PSAPPSRV.152 (132) 2017-01-13T10:28:59.614 DPRBATCH@JavaClient IntegrationSvc Returning SwitchUser variables. ID=m6c8RnSP6uzj1TlfV3Hmk7iOO7CrHSvcuI47sKsdK9y4jjuwqx0r3LiOO7CrHSvcuI47sKsdK9y4jjuwqx0r3A==, Pswd=+, ConnInfo=-, Lang=-, Token=-
PSAPPSRV.592 (9389) 2017-01-13T11:16:59.969 SAMSGSRV@JavaClient IntegrationSvc Processing SwitchUser command. CtxUser=SAMSGSRV/ENG, SwUser=DPRBATCH/+, SwConnInfo=-, SwToken=-
PSAPPSRV.592 (9389) 2017-01-13T11:16:59.969 SAMSGSRV@JavaClient IntegrationSvc Processing WssecIsAuthenticatedUser command. CtxUser=SAMSGSRV/ENG, SwUser=DPRBATCH/+
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see the problem there is a period followed by three digits earlier on those events... Here is a regex that matches the whole timestamp try this out.
\[\d{4}-\d{2}-\d{2}T\d{2}:\d{2}:\d{2}\.\d{3}\s(?<userid>.*)\@JavaClient\s
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yep! it works thank you!! But i also try with shorter one \d{2}.\d{3}\s(?.*)@JavaClient\s
that works too. which event has "a period followed by three digits" i only see a period before three digits.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is what I meant. The extra events you sent me had PSAPPSRV.XXX in the beginning that was matching and messing it up.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see. Thanks for pointing this out to me. I didn't know it would go all the way from the beginning of the string at the beginning of the line.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your regex is correct in matching XBATCH and ABCSRV however for Splunk's rex command you will need to give your extraction a name. That is what the <? ... > in the capture group is for.
Try doing this
\.\d\d\d\s(?<USERID>.*)\@JavaClient\s
As for regex syntax here is a cheat sheet I regularly reference when writing regex. https://www.cheatography.com/davechild/cheat-sheets/regular-expressions/
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
was it @ sign that's the issue? maybe it needs special escape character that is not \
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The @ symbol is not a reserved character for regex so you shouldn't need to escape it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| rex field=_raw ".\d\d\d\s(?.*)@JavaClient\s"
still not working
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
same result...not working either way 😞
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are some events correctly pulling the user id out? Is it just some events that pull the numbers before?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes i got 2 results coming out correctly but a lot still in format "(785) [2017-01-12T15:01:05.037 ABCSRV"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you post some samples of events that didn't get it correctly pulled? That way I can put those into my regex tester and tweak the regex.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also can you show me exactly the rex command that you are using?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your regex seems to have changed. The one you posted originally seems like it should work.
Use this regex
\.\d\d\d\s(?<userid>.*)\@JavaClient\s
instead of
.\d\d\d\s(?<userid>.*)\@JavaClient\s
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, sorry, I missed that tag.
| rex field=_raw ".\d\d\d\s(?.*)\@JavaClient\s"
I get the result but some of USERIDs still show up in as "(785) [2017-01-12T15:01:05.037 ABCSRV"