Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to display and group events in a timechart tha...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
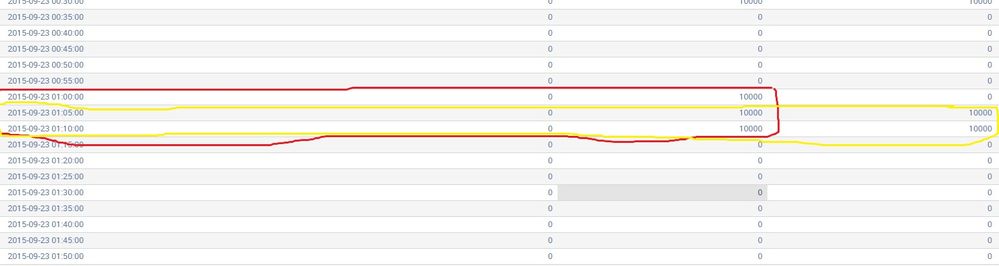
How to display and group events in a timechart that are continuous for 10 minutes?
kartik13
Communicator
08-03-2016
12:08 AM
Hi ,
I have a timechart with different columns. I want to display those events from a time chart which are continuous at least for 10 minutes.
I want to group the events which are marked red and yellow on based on the time or event. Help required.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
somesoni2
Revered Legend
08-03-2016
08:29 PM
Give this a shot (check the field names)
your current search with timechart | streamstats current=f windows=1 values('Total Error') as prev_error values('Total Auth') as prev_auth
| where (prev_error='Total Error' AND 'Total Error'!=0) OR (prev_auth='Total Auth' AND 'Total Auth'!=0)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
somesoni2
Revered Legend
08-03-2016
02:19 PM
Are the column names fixed in your time chart?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
kartik13
Communicator
08-03-2016
08:20 PM
yes they are , these are spikes in the Total Errors and authorization and authentication failures respectively .
Get Updates on the Splunk Community!
Automatic Discovery Part 1: What is Automatic Discovery in Splunk Observability Cloud ...
If you’ve ever deployed a new database cluster, spun up a caching layer, or added a load balancer, you know it ...
Real-Time Fraud Detection: How Splunk Dashboards Protect Financial Institutions
Financial fraud isn't slowing down. If anything, it's getting more sophisticated. Account takeovers, credit ...
Splunk + ThousandEyes: Correlate frontend, app, and network data to troubleshoot ...
Are you tired of troubleshooting delays caused by siloed frontend, application, and network data? We've got a ...