Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to correlate to multi-value fields from one ev...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to correlate to multi-value fields from one event?
gnostic_device
Engager
03-31-2022
10:23 AM
Hello,
I have logs where there are multiple values for two fields. This data looks like this example below for each event.
| dest | user | builtinadmin |
| computer1 | user1 user2 |
true false |
It comes from this raw data:
<computer N=computer1 D=corp OS=Windows DC=false>
<users>
<user N='user1" builtinadmin="false" />
<user N="user2" builtinadmin="true" />
</users>
</computer>
Is there a way to show the data like this instead where each user correctly correlates to the builinadmin value?
| dest | user | builtinadmin |
| computer1 | user1 | true |
| computer1 | user2 | false |
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yuanliu

SplunkTrust
04-01-2022
02:49 AM
Since your data is in XML, here is an alternative to mvzip-split combination, using path option in builtin function spath.
| rename computer{@N} AS dest ``` you already did this in your original search ```
| spath path=computer.users output=users ``` retain complete path as a single XML field ```
| eval users = split(users, "
") ``` for some reason users is single string; turn into multivalue ```
| mvexpand users
| spath input=users ``` extract user attrib from XML after mvexpand ```
| rename user{@N} as user, user{@builtinadmin} as builtinadmin ``` do this AFTER mvexpand, not before ```
| table dest user builtinadmin
Sample data gives
| dest | user | builtinadmin |
| computer1 | user1 | false |
| computer1 | user2 | true |
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
mayurr98
Super Champion
03-31-2022
10:49 AM
Hey
Not sure if there is any other easy way to do this but you can give this a try:
<user search>
|eval tagged=mvzip(user,builtinadmin)
| mvexpand tagged
| makemv tagged delim=","
| eval user=mvindex(tagged,0)
| eval builtinadmin=mvindex(tagged,1)
| table dest user builtinadminlet me know if this helps!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
kamlesh_vaghela

SplunkTrust
03-31-2022
10:49 AM
Can you please try this?
YOUR_SEARCH
| eval t=mvzip(user,builtinadmin,"|")
| mvexpand t
| eval user=mvindex(split(t,"|"),0),builtinadmin=mvindex(split(t,"|"),1) | table dest user builtinadmin
My Sample Search :
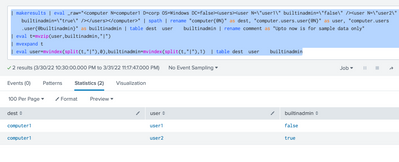
| makeresults | eval _raw="<computer N=computer1 D=corp OS=Windows DC=false><users><user N=\"user1\" builtinadmin=\"false\" /><user N=\"user2\" builtinadmin=\"true\" /></users></computer>" | spath | rename "computer{@N}" as dest, "computer.users.user{@N}" as user, "computer.users.user{@builtinadmin}" as builtinadmin | table dest user builtinadmin | rename comment as "Upto now is for sample data only"
| eval t=mvzip(user,builtinadmin,"|")
| mvexpand t
| eval user=mvindex(split(t,"|"),0),builtinadmin=mvindex(split(t,"|"),1) | table dest user builtinadmin
Thanks
KV
If any of my reply helps you to solve the problem Or gain knowledge, an upvote would be appreciated.
Get Updates on the Splunk Community!
Splunk Mobile: Your Brand-New Home Screen
Meet Your New Mobile Hub
Hello Splunk Community!
Staying connected to your data—no matter where you are—is ...
Introducing Value Insights (Beta): Understand the Business Impact your organization ...
Real progress on your strategic priorities starts with knowing the business outcomes your teams are delivering ...
Enterprise Security (ES) Essentials 8.3 is Now GA — Smarter Detections, Faster ...
As of today, Enterprise Security (ES) Essentials 8.3 is now generally available, helping SOC teams simplify ...