Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Search
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to convert row values into fields with count?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
cindywee
New Member
08-22-2019
12:22 PM
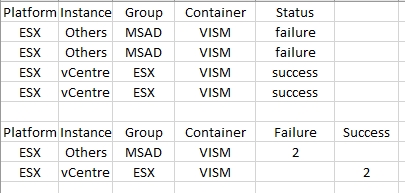
Hi. How do I get from the first table to look like the second table?
I have tried chart, transpose, different combination of eval and stats functions but just cannot get it to look right. I am working off a csv data set.
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
solarboyz1
Builder
08-22-2019
12:28 PM
Add the following to the search you used to generate the first table:
| stats sum(eval(if(status="failure",1,0)) as Failure, sum(eval(if(status="success",1,0)) as Success by Platform, Instance, Group, Container
https://docs.splunk.com/Documentation/Splunk/7.3.1/Search/Usestatswithevalexpressionsandfunctions
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
cindywee
New Member
08-22-2019
12:47 PM
You are a genius. The most simple solution is always to right solution.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
solarboyz1
Builder
08-22-2019
12:28 PM
Add the following to the search you used to generate the first table:
| stats sum(eval(if(status="failure",1,0)) as Failure, sum(eval(if(status="success",1,0)) as Success by Platform, Instance, Group, Container
https://docs.splunk.com/Documentation/Splunk/7.3.1/Search/Usestatswithevalexpressionsandfunctions
Get Updates on the Splunk Community!
Enterprise Security Content Update (ESCU) | New Releases
In December, the Splunk Threat Research Team had 1 release of new security content via the Enterprise Security ...
Why am I not seeing the finding in Splunk Enterprise Security Analyst Queue?
(This is the first of a series of 2 blogs).
Splunk Enterprise Security is a fantastic tool that offers robust ...
Index This | What are the 12 Days of Splunk-mas?
December 2024 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with another ...