Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to compare and save the values between som...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
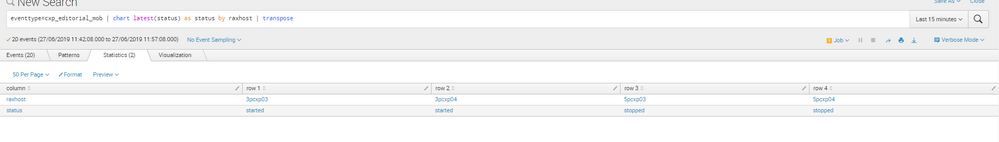
I have below input:
Now I want to do below comparision:
(Row1 = started AND row2=started ) OR (row3="started" AND Row4="started")
The result is good otherwise result is bad.
I don't know how to do that comparison and save the value, can anyone please help?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ruchijain,
You have almost the solution in your question itself. Probably you haven't specified the fields correctly
| eval result=if(('row 1' = "started" AND 'row 2'="started" ) OR ('row 3'="started" AND 'row 4'="started"),"good","bad")
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ruchijain,
You have almost the solution in your question itself. Probably you haven't specified the fields correctly
| eval result=if(('row 1' = "started" AND 'row 2'="started" ) OR ('row 3'="started" AND 'row 4'="started"),"good","bad")
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Renjith,
Please find the image attahced:
But if i will look for bad it will alert for the first row but i think i got the option like if number of result if greater than 1 then it will alert.
Can i use this query?
eventtype=cxp_editorial_mob | chart latest(status) as status by raxhost | transpose | eval result=if(('row 1'!= "started" AND 'row 2'!="started" ) OR ('row 3'="started" AND 'row 4'="started"),"good","bad")

- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
eventtype=cxp_editorial_mob | chart latest(status) as status by raxhost | transpose | eval result=if(('row 1'!= "started" AND 'row 2'!="started" ) OR ('row 3'="started" AND 'row 4'="started"),"good","bad")
|where result=="bad"
and then trigger alert if Number of Results is greater than 0.
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks renjith for the answer.
Just need one more i got below output:

I want to juts check for the row status if it is good or bad...
Means i want to get alert if the status row is bad... how to do that
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ruchijain,
the image is not available. You could add |where result=="bad" to your search and trigger alert if Number of Results is greater than 0
What goes around comes around. If it helps, hit it with Karma 🙂