Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to combine multiple searches into 1 related ta...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to combine multiple searches into 1 related table/graph?
lordhans
Explorer
06-14-2017
07:20 PM
I have two searches something like this:
"ns=my_project" message="*RESPONSE_CODE=200*" OR "*RESPONSE_CODE=400*" METHOD=API1 add|top RESPONSE_CODE
"ns=my_project" message="*RESPONSE_CODE=200*" OR "*RESPONSE_CODE=400*" METHOD=API2 something_else|top RESPONSE_CODE
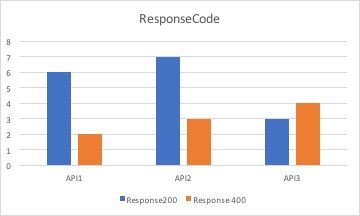
I want to combine them into one graph/table that will look something like this:
Any help or ideas are greatly appreciated!
Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
woodcock
Esteemed Legend
06-15-2017
04:56 PM
Try this:
index=YourIndexHere sourcetype=YourSourcetypeHere "ns=my_project" message="*RESPONSE_CODE=200*" OR "*RESPONSE_CODE=400*" ((METHOD="API1" AND "add") OR (METHOD="API2" AND "something_else")
| stats count(eval(searchmatch(message="*RESPONSE_CODE=200*"))) AS "Response 200" count(eval(searchmatch(message="*RESPONSE_CODE=400*"))) AS "Response 400" BYMETHOD
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
DalJeanis
Legend
06-15-2017
01:05 PM
start with this...
index=foo "ns=my_project"
(message="*RESPONSE_CODE=200*" OR message="*RESPONSE_CODE=400*")
((METHOD="API1" and "add") OR (METHOD="API2" and "something_else"))
| stats count as eventcount by METHOD RESPONSE_CODE
| chart sum(eventcount) by METHOD RESPONSE_CODE
The above code has not used the top command to limit the responses, but if you only have 2 response codes, then top is redundant.
Here's a run-anywhere sample to show how it works...
| makeresults | eval METHOD="API1 API2 API3" | makemv METHOD | mvexpand METHOD
| eval RESPONSE_CODE="200 400" | makemv RESPONSE_CODE| mvexpand RESPONSE_CODE
| eval rand=random()%155
| rename COMMENT as "The above just generates test data."
| stats sum(rand) as eventcount by METHOD RESPONSE_CODE
| chart sum(eventcount) by METHOD RESPONSE_CODE
Get Updates on the Splunk Community!
Automatic Discovery Part 1: What is Automatic Discovery in Splunk Observability Cloud ...
If you’ve ever deployed a new database cluster, spun up a caching layer, or added a load balancer, you know it ...
Real-Time Fraud Detection: How Splunk Dashboards Protect Financial Institutions
Financial fraud isn't slowing down. If anything, it's getting more sophisticated. Account takeovers, credit ...
Splunk + ThousandEyes: Correlate frontend, app, and network data to troubleshoot ...
Are you tired of troubleshooting delays caused by siloed frontend, application, and network data? We've got a ...