Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to calculate time difference / duration not sh...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
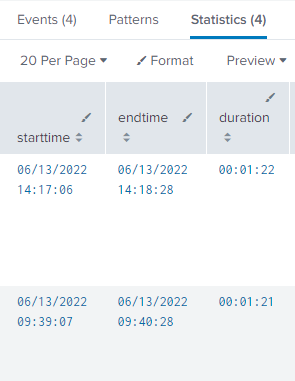
Hi all, I need to calculate the duration i.e. difference between endtime & starttime and display the same in a user friendly format. I have looked at different posts on the forum and am using the same logic yet if you see my splunk results below, the duration column shows numbers like 81, 82 , 96... which doesn't make sense. Are these difference in secs ? Even if its secs, the math doesn't seem to be correct. How can I make diff value show in a readable format like 81 seconds, or 00:00:81 ( HH:MM:SS) ?
| transaction eventID startswith=starting endswith=end
| eval starttime = _time | eval endtime=_time+duration
| eval duration = endtime-starttime
| convert ctime(starttime)| convert ctime(endtime)
| table starttime, endtime, duraton
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @neerajs_81,
all the time calculations must be done on numbers, so the tostring option is good to display a duration in human readable format, but it isn't good for calculations.
So make calculations before the tostring transformation, as @PickleRick and @ITWhisperer hinted:
if you want a duration greater one hour you have to calculate something like this.
| eval condition=if(duration>3600),"More than 1 hour","Less than 1 hour")If this or another one answer solves your need, please, accept it for the other people of Community.
Ciao.
Giuseppe
P.S.: Karma Points are appreciated by all the Contributors 😉
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It does make perfect sense.
14:17:06 + 82 seconds = 14:18:06+22 seconds = 14:18:28
And so on.
I'd also advise to not use eval to convert from this seconds-based duration to string but use fieldformat. This way you retain the possibility to do any manipulation you want but you'll present the time to the user in a readable way.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @neerajs_81,
di you explored the use of tostring option?
somthing like this:
| transaction eventID startswith=starting endswith=end
| eval starttime = _time | eval endtime=_time+duration
| eval duration = tostring(endtime-starttime,"duration")
| convert ctime(starttime)| convert ctime(endtime)
| table starttime, endtime, duratonCiao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are the man !!!. Thank you.
One more related question, now that we have the duration calculated, how do i enable a condition to check if duration > N hours or N mins ? Basically i need to filter for events where duration is past 1 hour say. Will the below where clause work ? Doesn't appear to be working
| where duration > 00:60:00 OR | where duration > 60
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @neerajs_81,
all the time calculations must be done on numbers, so the tostring option is good to display a duration in human readable format, but it isn't good for calculations.
So make calculations before the tostring transformation, as @PickleRick and @ITWhisperer hinted:
if you want a duration greater one hour you have to calculate something like this.
| eval condition=if(duration>3600),"More than 1 hour","Less than 1 hour")If this or another one answer solves your need, please, accept it for the other people of Community.
Ciao.
Giuseppe
P.S.: Karma Points are appreciated by all the Contributors 😉
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have your where command before the tostring() function remembering that the value will be in seconds, so use 3600 for 1 hour.