Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to add another column which shows TRUE/False b...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to add another column which shows TRUE/False based on row values
vinaykataaig
Explorer
08-09-2019
10:31 AM
HI all,
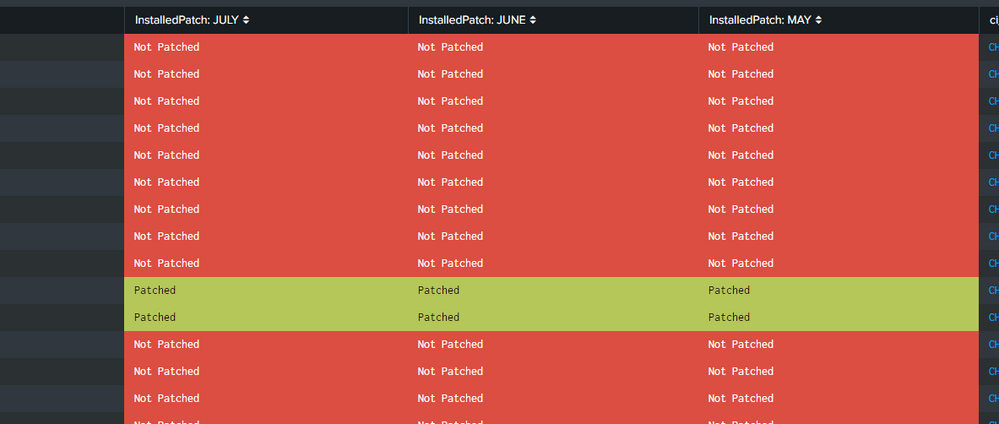
Could anyone help me to add another column which shows true/false based on values on the other 3 rows.
When all the three columns says "Not Patched" I want that row to be defined as False at the end of the table the same way when the three columns says "Patched" i want that to show as True. Below is my query.
index="oswinsec" sourcetype="windowsupdatelog" | search "*Patch Deployment*" AND "*AGENT_INSTALLING_SUCCEEDED*"
| rex field=_raw "^(?:[^:\n]*:){9}\s+(?P.+)"
| eval servers = Upper(mvindex(split(host,"."),-0))
| eval start=strptime(Time, "%Y-%m-%d %H:%M:%S.%N")
| eval day = strftime(start, "%a")
| eval month = Upper(date_month)
| replace "*KB*" WITH "Patched" IN ApplicablePatch
| stats values(count) as count values(ApplicablePatch) as ApplicablePatch by servers month | mvexpand servers
| chart values(ApplicablePatch) as InstalledPatch by servers | fillnull value="Not Patched"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
renjith_nair
Legend
08-10-2019
05:56 AM
@vinaykataaig,
Since the field names are dynamic for each month you run, try adding this to your current search
"your current search"|eval Result="True"
|foreach InstalledPatch* [eval Result=if(<<FIELD>>=="Not Patched","False",Result)]
---
What goes around comes around. If it helps, hit it with Karma 🙂
What goes around comes around. If it helps, hit it with Karma 🙂
Get Updates on the Splunk Community!
Accelerating Observability as Code with the Splunk AI Assistant
We’ve seen in previous posts what Observability as Code (OaC) is and how it’s now essential for managing ...
Integrating Splunk Search API and Quarto to Create Reproducible Investigation ...
Splunk is More Than Just the Web Console
For Digital Forensics and Incident Response (DFIR) practitioners, ...
Congratulations to the 2025-2026 SplunkTrust!
Hello, Splunk Community! We are beyond thrilled to announce our newest group of SplunkTrust members!
The ...