Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to achieve grouping the results using field pr...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to achieve grouping the results using field present inside a json array?
I have below format log messages. At the end I want to group the messages by BID. I tried using the below query but I am not getting any events even though there are events that qualify my query.
{
"details" : [
{
"BID" : "123"
},
{
"BID" : "456"
}
]
}
Expected Output :
BID Count
123 4
456 3
Query I am using :
{my_search}
| rex field=MESSAGE "(?<JSON>\{.*\})"
| spath input=JSON path=details.BID
| stats values(details.BID) as "BID" by CORRID
| stats count as Count by "BID"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks you so much!! I just had one doubt. So these BIDs correspond to some static fields which describe what BID is. Like BID : 123 corresponds to Apple. This detail/description is however not present in the events or search results. Is there any way to configure these as static fields which will get displayed when the billing code is displayed Like below
Output
Description BID Count
Apple 123 4
Orange 456 3- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can create a lookup with BID and description mapping. And use the lookup in your search.
BID,Description
123,Apple
https://docs.splunk.com/Documentation/SplunkCloud/latest/Knowledge/ConfigureCSVlookups
https://docs.splunk.com/Documentation/SplunkCloud/latest/SearchReference/Lookup
I hope this will help you.
Thanks
KV
If any of my replies help you to solve the problem Or gain knowledge, an upvote would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please try this?
YOUR_SEARCH
| rename "details{}.BID" as BID
| stats count as Count by BIDOR
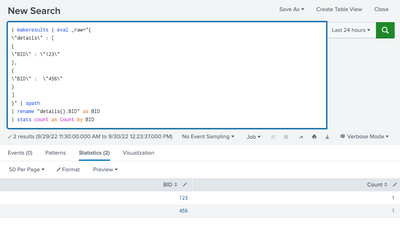
YOUR_SEARCH | spath
| rename "details{}.BID" as BID
| stats count as Count by BID
My Sample Search :
| makeresults | eval _raw="{
\"details\" : [
{
\"BID\" : \"123\"
},
{
\"BID\" : \"456\"
}
]
}" | spath
| rename "details{}.BID" as BID
| stats count as Count by BID
I hope this will help you.
Thanks
KV
If any of my replies help you to solve the problem Or gain knowledge, an upvote would be appreciated.