Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How do I sum the counts of all the similar values ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
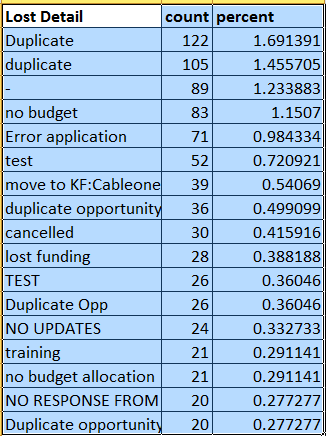
Below search command is giving the results as below
source="report1447097285313.csv" host="ca2indslogprd02" index="poc" sourcetype="csv" "Lost Detail"="*" host="*"| top limit=20 "Lost Detail"
How do I sum all the %duplicate% values in the field Lost Detail and show it as a single value?For example, I would like to show the results for Duplicate, duplicate, duplicate opportunity, Duplicate Opp in below table as one value with the sum of its count.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The essence here is using eval to match on case insensitive duplicate:
| eval "Lost Detail" = if(match('Lost Detail', "(?i)duplicate.*"), "duplicate", 'Lost Detail')
In the case that the regular expression (?i)duplicate.* is matched to the value of the field Lost Detail, return "duplicate" as the value, otherwise, just return return the value of Lost Detail (single quotes are crucial!).
source="report1447097285313.csv" host="ca2indslogprd02" index="poc" sourcetype="csv" "Lost Detail"="*" host="*"
| eval "Lost Detail" = if(match('Lost Detail', "(?i)duplicate.*"), "duplicate", 'Lost Detail')
| top limit=20 "Lost Detail"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The essence here is using eval to match on case insensitive duplicate:
| eval "Lost Detail" = if(match('Lost Detail', "(?i)duplicate.*"), "duplicate", 'Lost Detail')
In the case that the regular expression (?i)duplicate.* is matched to the value of the field Lost Detail, return "duplicate" as the value, otherwise, just return return the value of Lost Detail (single quotes are crucial!).
source="report1447097285313.csv" host="ca2indslogprd02" index="poc" sourcetype="csv" "Lost Detail"="*" host="*"
| eval "Lost Detail" = if(match('Lost Detail', "(?i)duplicate.*"), "duplicate", 'Lost Detail')
| top limit=20 "Lost Detail"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thank you johnson. Above eval function is giving me "Error in 'eval' command: The arguments to the 'case' function are invalid". I tried adding closing brace to case function ? Did i miss anything with respect to the syntax. I apologize for asking the basic question
source="report1447097285313.csv" host="ca2indslogprd02" index="poc" sourcetype="csv" "Lost Detail"="*" host="*"
| eval "Lost Detail" = case(match("Lost Detail", "(?i)duplicate.*"), "duplicate", "Lost Detail"**)**
| top limit=20 "Lost Detail"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry ! It should've been if, not case.
Case takes pairs of arguments e.g. case(X, Y, X, Y,...) where each x is a boolean and y is the returned value if x is true.
If however takes 3 arguments, e.g. if(X,Y,Z), where x is boolean - if true, return y, else, return z.
Was also missing a ending parens. My bad.
@praneethkodali
@sundareshr
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thank you, it worked. I used single quotes for the 'Lost Detail' field in match and if functions from your answer.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Haha I missed those too ! I will update the answer for future people but sorry for my sloppiness. Glad you got it working.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try removing the space in your field name eg. "Lost Detail" s/b Lost_Detail See if that helps. You can always add the space back with a replace commande