Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How do I edit my search to calculate a percentage ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, I wonder whether someone may be able to help me please
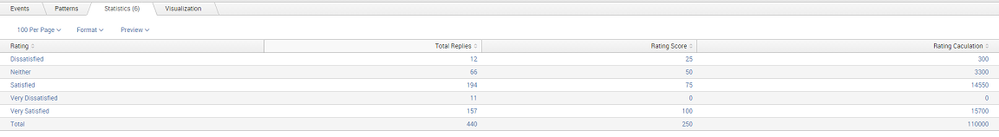
I'm using the search below to produce the screenshot as shown in the attachment:
index=main auditSource=frontend auditType=Survey detail.overall!="None"
| replace frontend with "Overall Satisfaction"
| rename detail.overall As "Rating"
| replace 1 with "Very Satisfied", 2 with "Satisfied", 3 with "Neither", 4 with "Dissatisfied", 5 with "Very Dissatisfied"
| chart count by Rating
| eval "Rating Score"=case(Rating="Very Satisfied", 100, Rating="Satisfied", 75 , Rating="Neither", 50, Rating="Dissatisfied", 25, Rating="Very Dissatisfied", 0 , 1=1, 0)
| addcoltotals | fillnull value="Total" | rename count as "Total Replies"
| table "Rating", "Total Replies", "Rating Score"
| eval "Rating Calculation" = 'Total Replies' * 'Rating Score'
I don't even know whether this possible, but what I'd like to do is perform the following calculation using only the "Total" row figures.
Rating Calculation / Total Replies and formatted to a percentage with one decimal point.
I've spent a couple of days searching the web to see if I can find suitable solutions without any success.
NB. I will be putting this is a dashboard if it helps.
I just wondered whether someone may be able to look at this please and offer some guidance on how I may be able to achieve this.
Many thanks and kind regards
Chris
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
At the end of your search, add the following line
| eval Percentage=if(Rating=="Total",tostring(round('Rating Calculation' *100 / 'Total Replies',1)) + "%",null())
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
At the end of your search, add the following line
| eval Percentage=if(Rating=="Total",tostring(round('Rating Calculation' *100 / 'Total Replies',1)) + "%",null())
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI @iguinn, thank you very much for taking the time to come back to me with this.
I needed to make a very minor tweak changing *100 to 1 and it works great.
Once many thanks for your help and kind regards
Chris