- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How can I monitor user activity pattern search?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How can I monitor user activity pattern search?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
..
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You still haven't illustrated what the output from my search is, and demonstrate desired result so I can see the difference; also, you haven't illustrated any valid JSON events to demonstrate what happened when your went on-prem, and what happened when you went home to connect via VPN. Without data, troubleshooting data analytics problems is nearly impossible. Without demonstration of your desired results, a lot of what we discuss is pure speculation.
Perhaps there's a discrepancy between your desired results and your original description, too. You originally said "search by user on a daily basis":
if they have accessed OKTA and ( "anyconnect" or Cisco) if they do, we populate VPN connected for that date. If they only have accessed OKTA and NOT ("anyconnect" or Cisco), then we populate ON Prem Connected for that date. If they have neither we populate none for the date.
(Highlights are mine.) This means that for any given date, you only populate one state. This is particularly important with scenario 2, when Okta and VPN logons are independent events. (In scenario 1, you automatically get multiple states if state changes within one day.) What is the criteria to tell which VPN logon is supposed to be grouped with which Okta logon? You have not even described in which order the two type of events would happen in real data if they are associated with one user action. (Also, is such order stable in Splunk? For example, if they occur within 1ms from each other, will Splunk always give the accurate order?)
Suppose Okta happens first, VPN happens second. Your last week's experience (I assume you were describing your change of location within one day) would produce the following events.
- Okta logon,
- Okta logon,
- VPN logon
Unless there is a logoff event between 1 and 2 that Splunk is aware of, or if there exist other criteria that you can describe in terms of Splunk data, there is no way to know how the two Okta logon events relate to each other, are they from one user action or two, and so on.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My output is
_time user logon connectivity_type
7/13/23 xyz Okta VPN
VPN
How do you want me to send _raw event to Json ?
*how we can bound connectivity_type this with time ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
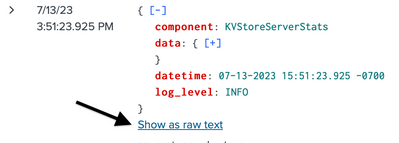
To get raw JSON even, first search for the events in which user xyz (you) logged on that day, both okta events and VPN events. For JSON events, you'll see a link "Show as raw text" in events window. Click it to get raw text. Load them into an editor and anonymize. (I thought you did this in the original description, except the anonymization did not preserve the original JSON format so the posted text is not valid JSON. Be careful with editing; use a JSON helper/validator if needed.)
Back to the output. I see that the search correctly captures both logon types. In that case, try another test on user xyz (you) on this day when you had both on-prem and VPN connections.
index=xyz sourcetype=Okta* userid="xyz" ((eventType=user.* displayMessage = "User single sign on to app")
OR (targetAppAlternateId = "cisco*" OR targetAppAlternateId = "anyconnect*) earliest=-30d
| eval logon = case(match(displayMessage, "User single sign on to app"), "Okta", match(targetAppAlternateId, "anyconnect|Cisco"), "VPN")
| eval timestamp = strftime(_time, "%FT%H:%M:%S")
| where isnotnull(logon)
| bin span=1d@d _time
| stats list(logon) as logon list(timestamp) as timestamp by _time userid
| eval connectivity_type = if(logon == "Okta", if(logon == "VPN", "VPN", "On-prem"), "none")What is the output?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let's settle one subject at a time. (It would be much easier if you posted output in text.) So, on this given day, you had two pairs of logon events. From first (top) to last (bottom):
| 1 | 2023-06-21T10:12:09 | VPN |
| 2 | 2023-06-21T10:12:09 | Okta |
| 3 | 2023-06-21T17:18:03 | VPN |
| 4 | 2023-06-21T17:18:03 | Okta |
First of all, I observe that events in each pair happened within the same calendar second. Is this sufficient condition to deem 1-2 the same user action, and 3-4 the same?
Secondly, how does this indicate that one of them is from home, one of them on-prem? To me, these two pairs indicate the exact same kind of user action, namely at home.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
..
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do not understand.
In this we get to see the Cisco auth ....
{
"actor": {
"id": "00u12x51ytWyIKps6357",
"type": "User",
"alternateId": "xyz.com",...
This event doesn't contain the field targetAppAlternateId at all. How could this yield VPN? For the search to show VPN, it much satisfy match(targetAppAlternateId, "anyconnect|Cisco").
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@yuanliu
Hi,
Here we get to see the "legacyEventType": "app.auth.sso, I believe this is the one related to auth!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here we get to see the "legacyEventType": "app.auth.sso, I believe this is the one related to auth!
A better field would be eventType that you mentioned earlier.
So, I have painstakingly examined the event samples for 2023-06-21 you provided, correcting for minor syntax errors introduced in anonymization. My conclusion is that all 4 of them are of one type of user action: Cisco VPN logon.
Field "published" contains time resolution to millisecond. It allows me to establish the order of the events in one group. So, I use that as event _time. The following are values of fields of particular interest:
| _time | alternateId | displayMessage | eventType | legacyEventType | type |
| 2023-06-21 11:48:03.367 | Cisco | User single sign on to app | user.authentication.sso | app.auth.sso | AppInstance |
| 2023-06-21 11:48:03.230 | cisco | Evaluation of sign-on policy | policy.evaluate_sign_on | null | AppInstance |
| 2023-06-21 04:42:09.708 | cisco | User single sign on to app | user.authentication.sso | app.auth.sso | AppInstance |
| 2023-06-21 04:42:09.551 | cisco | Evaluation of sign-on policy | policy.evaluate_sign_on | null | AppInstance |
Several notes here:
- Syntax errors in sample data include not putting anonymized strings in quotation marks, putting unbalanced quotes surrounding them, not preserving comma after anonymization, etc. These are very difficult to correct, especially when event is complex. I literally scrubbed them for hours and hours. Please avoid them.
- Your sample data contain no fields named "app" and "targetAppAlternateId", but you repeatedly mentioned them or implied in sample code. It is extremely difficult to understand a question or comment when they do not relate to data in a direct manner. After hours and hours, I finally concluded that "targetAppAlternateId" is perhaps target{}.alternateId (shown above as alternateId) when target{}.type (shown above as type) is AppInstance. We could have saved tons of time and agony if data sample is accurately provided, and we can use accurate reference that is commonly accepted in SPL.
- It is possible that your Splunk instance has some sort of knowledge object that automatically populate a field named targetAppAlternateId based on the above calculation. But volunteers would have no way to make this connection unless you explicitly explain it.
- My interpretation of the above time table (in reverse time order) is that each VPN logon triggers two events: "Evaluation of sign-on policy" a few millisecond earlier, followed by "User single sign on to app". Both of them correspond to target{}.alternateId and target{}.displayName "cisco". Therefore they both correspond to VPN logon. (At one point, you mentioned that EventType "user.authentication.sso" is sufficient to filter out VPN logon events.)
- This table uses Zulu time (UTC). It is much easier if we can standardize on one time zone. Because this is a global forum, the most natural is Zulu.
- Keep in mind that few people in a data analytics forum have intimate knowledge about "firewall index i.e vpn logs", let alone customizations in your deployment. If you want concrete help in search, you must accurately demonstrate relevant data, explain critical characteristics of sample data, explain the logic (without using code) that connects illustrated data with desired results.
Bottom line:
- Sample data thus far are insufficient to determine which conditions correspond to on-prem logon. (It is clear that VPN logon also triggers an event that satisfies match(displayMessage, "User single sign on to app").)
- Without a logout, timeout, or some other type of termination/revocation event, it is perhaps impossible to determine that a user logged on on-prem then logged on via VPN or vice versa.
In all cases, you need to keep looking for events that you can explain to volunteers how to determine that the user had activities using two different network paths on the same day WITHOUT showing any SPL. Just illustrate data and explain. I strongly suggest that you include termination/revocation events in your search. (It is possible that even "eventType=user.*", "sourcetype=Okta*", etc. are too restrictive.)
Data emulation
Just so I don't loose my hours of cleansing, here is the emulation that I used to produce the above table. You can (and should) play with it to see if it accurately reflects characteristics of real data.
| makeresults
| eval data = split("{
\"actor\": {
\"id\": \"00u12x51ytWyIKps6357\",
\"type\": \"User\",
\"alternateId\": \"xyz\",
\"displayName\": \"xyz\",
\"detailEntry\": null
},
\"client\": {
\"userAgent\": {
\"rawUserAgent\": \"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36\",
\"os\": \"Mac OS X\",
\"browser\": \"CHROME\"
},
\"zone\": \"null\",
\"device\": \"Computer\",
\"id\": null,
\"ipAddress\": \"xxx.xxx.xxx.xxx\",
\"geographicalContext\": {
\"city\": \"xxx\",
\"state\": \"xxxx\",
\"country\": \"xx\",
\"postalCode\": \"xxxxx\",
\"geolocation\": {
\"lat\": \"xx.074\",
\"lon\": \"xy.885\"
}
}
},
\"device\": null,
\"authenticationContext\": {
\"authenticationProvider\": null,
\"credentialProvider\": null,
\"credentialType\": null,
\"issuer\": null,
\"interface\": null,
\"authenticationStep\": 0,
\"externalSessionId\": \"1024RuQTjVbRuCwGJUigehMQQ\"
},
\"displayMessage\": \"User single sign on to app\",
\"eventType\": \"user.authentication.sso\",
\"outcome\": {
\"result\": \"SUCCESS\",
\"reason\": null
},
\"published\": \"2023-06-21T11:48:03.367Z\",
\"securityContext\": {
\"asNumber\": 17665,
\"asOrg\": \"ten g network solution private limited\",
\"isp\": \"oneott intertainment limited\",
\"domain\": \".\",
\"isProxy\": false
},
\"severity\": \"INFO\",
\"debugContext\": {
\"debugData\": {
\"audience\": \"https://cp-vpn.cisco.com:443/SAML20/SP\",
\"subject\": \"xyz\",
\"signOnMode\": \"SAML 2.0\",
\"authenticationClassRef\": \"urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport\",
\"authTime\": \"2023-06-21T11:47:53.940Z\",
\"requestUri\": \"/login/sessionCookieRedirect\",
\"issuer\": \"http://www.okta.com\",
\"url\": \"/login/sessionCookieRedirect?\",
\"initiationType\": \"SP_INITIATED\",
\"authnRequestId\": \"ZJLjaRWsg8s_z3NAOxrMMAAAD0A\",
\"requestId\": \"ZJLjchWsg8s_z3NAOxrMlwAAD0A\",
\"dtHash\": \"88fc37626c5fd644f5b668d172e9784a3a30ada9f3d0689f273014770f217bef\",
\"expiryTime\": \"2023-06-21T11:53:03.357Z\",
\"issuedAt\": \"2023-06-21T11:48:03.357Z\",
\"threatSuspected\": \"false\",
\"jti\": \"id7809089890\"
}
},
\"legacyEventType\": \"app.auth.sso\",
\"transaction\": {
\"type\": \"WEB\",
\"id\": \"hghuhuh\",
\"detail\": {}
},
\"uuid\": \"xyz\",
\"version\": \"0\",
\"request\": {
\"ipChain\": [
{
\"ip\": \"xxx.xxx.xxx.xxx\",
\"geographicalContext\": {
\"city\": \"xxxx\",
\"state\": \"xxx\",
\"country\": \"xxx\",
\"postalCode\": \"xxxxx\",
\"geolocation\": {
\"lat\": \"xx.xxx\",
\"lon\": \"xx.xxx\"
}
},
\"version\": \"V4\",
\"source\": null
}
]
},
\"target\": [
{
\"id\": \"0oa5z8j61vqsPAEk2357\",
\"type\": \"AppInstance\",
\"alternateId\": \"Cisco\",
\"displayName\": \"Cisco\",
\"detailEntry\": {
\"signOnModeType\": \"SAML_2_0\"
}
},
{
\"id\": \"JJDFIFFK\",
\"type\": \"AppUser\",
\"alternateId\": \"xxxx\",
\"displayName\": \"xxx\",
\"detailEntry\": \"xxx\"
}
]
}
{
\"actor\": {
\"id\": \"0xxx\",
\"type\": \"User\",
\"alternateId\": \"xxx\",
\"displayName\": \"xxx\",
\"detailEntry\": null
},
\"client\": {
\"userAgent\": {
\"rawUserAgent\": \"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36\",
\"os\": \"Mac OS X\",
\"browser\": \"CHROME\"
},
\"zone\": \"null\",
\"device\": \"Computer\",
\"id\": null,
\"ipAddress\": \"xxx.xxx.xxx.xxx\",
\"geographicalContext\": {
\"city\": \"xxx\",
\"state\": \"xx\",
\"country\": \"xxx\",
\"postalCode\": \"xxxx\",
\"geolocation\": {
\"lat\": \"xx\",
\"lon\": \"7xx\"
}
}
},
\"device\": null,
\"authenticationContext\": {
\"authenticationProvider\": null,
\"credentialProvider\": null,
\"credentialType\": null,
\"issuer\": null,
\"interface\": null,
\"authenticationStep\": 0,
\"externalSessionId\": \"xxxx\"
},
\"displayMessage\": \"Evaluation of sign-on policy\",
\"eventType\": \"policy.evaluate_sign_on\",
\"outcome\": {
\"result\": \"ALLOW\",
\"reason\": \"Sign-on policy evaluation resulted in REQUIRE_FACTOR\"
},
\"published\": \"2023-06-21T11:48:03.230Z\",
\"securityContext\": {
\"asNumber\": \"xxx\",
\"asOrg\": \"xxx\",
\"isp\": \"xx\",
\"domain\": \".\",
\"isProxy\": false
},
\"severity\": \"INFO\",
\"debugContext\": {
\"debugData\": {
\"authnRequestId\": \"xxxx\",
\"requestId\": \"xxxx\",
\"authMethodFirstVerificationTime\": \"2023-06-21T11:48:01Z\",
\"dtHash\": \"xxxxx\",
\"authMethodFirstType\": \"OKTA_VERIFY_PUSH\",
\"authMethodFirstEnrollment\": \"xxx\",
\"requestUri\": \"/login/sessionCookieRedirect\",
\"threatSuspected\": \"false\",
\"url\": \"/login/sessionCookieRedirect?\",
\"logOnlySecurityData\": \"{\\\"risk\\\":{\\\"level\\\":\\\"LOW\\\"},\\\"behaviors\\\":{\\\"New Geo-Location\\\":\\\"NEGATIVE\\\",\\\"New Device\\\":\\\"NEGATIVE\\\",\\\"New IP\\\":\\\"NEGATIVE\\\",\\\"New State\\\":\\\"NEGATIVE\\\",\\\"New Country\\\":\\\"NEGATIVE\\\",\\\"Speed based login\\\":\\\"NEGATIVE\\\",\\\"New City\\\":\\\"NEGATIVE\\\"}}\"
}
},
\"legacyEventType\": null,
\"transaction\": {
\"type\": \"WEB\",
\"id\": \"xxx\",
\"detail\": {}
},
\"uuid\": \"7xxx1\",
\"version\": \"0\",
\"request\": {
\"ipChain\": [
{
\"ip\": \"xxx\",
\"geographicalContext\": {
\"city\": \"xx\",
\"state\": \"xx\",
\"country\": \"xx\",
\"postalCode\": \"xxx\",
\"geolocation\": {
\"lat\": \"1xx\",
\"lon\": \"7xx\"
}
},
\"version\": \"V4\",
\"source\": null
}
]
},
\"target\": [
{
\"id\": \"xxx\",
\"type\": \"PolicyRule\",
\"alternateId\": \"unknown\",
\"displayName\": \"MFA Always\",
\"detailEntry\": null
},
{
\"id\": \"0oa5z8j61vqsPAEk2357\",
\"type\": \"AppInstance\",
\"alternateId\": \"cisco\",
\"displayName\": \"cisco\",
\"detailEntry\": {
\"signOnModeType\": \"SAML_2_0\",
\"signOnModeEvaluationResult\": \"ALLOW\"
}
}
]
}
{
\"actor\": {
\"id\": \"xxx\",
\"type\": \"User\",
\"alternateId\": \"xxxx\",
\"displayName\": \"xxx\",
\"detailEntry\": null
},
\"client\": {
\"userAgent\": {
\"rawUserAgent\": \"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36\",
\"os\": \"Mac OS X\",
\"browser\": \"CHROME\"
},
\"zone\": \"null\",
\"device\": \"Computer\",
\"id\": null,
\"ipAddress\": \"xxxxx\",
\"geographicalContext\": {
\"city\": \"xxxx\",
\"state\": \"xx\",
\"country\": \"xxxx\",
\"postalCode\": \"xxxxx\",
\"geolocation\": {
\"lat\": \"xxx\",
\"lon\": \"xxx\"
}
}
},
\"device\": null,
\"authenticationContext\": {
\"authenticationProvider\": null,
\"credentialProvider\": null,
\"credentialType\": null,
\"issuer\": null,
\"interface\": null,
\"authenticationStep\": 0,
\"externalSessionId\": \"10220hjdBn7Ray8rtAq5IAvTA\"
},
\"displayMessage\": \"User single sign on to app\",
\"eventType\": \"user.authentication.sso\",
\"outcome\": {
\"result\": \"SUCCESS\",
\"reason\": null
},
\"published\": \"2023-06-21T04:42:09.708Z\",
\"securityContext\": {
\"asNumber\": 334343,
\"asOrg\": \"google\",
\"isp\": \"google\",
\"domain\": \"googleusercontent.com\",
\"isProxy\": false
},
\"severity\": \"INFO\",
\"debugContext\": {
\"debugData\": {
\"audience\": \"https://cp-vpn.cisco:443/SAML20/SP\",
\"subject\": \"xxxx\",
\"signOnMode\": \"SAML 2.0\",
\"authenticationClassRef\": \"urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport\",
\"authTime\": \"2023-06-21T04:41:59.510Z\",
\"requestUri\": \"/app/cisco_prismaaccessnew_1/exk5z8j61uVsvkdn6357/sso/saml\",
\"issuer\": \"http://www.okta.com/\",
\"url\": \"/app/cisco_prismaaccessnew_1/exk5z8j61uVsvkdn6357/sso/saml?SAMLRequest=xxx\",
\"initiationType\": \"SP_INITIATED\",
\"authnRequestId\": \"fdfdfdkg\",
\"requestId\": \"fdfdfdf\",
\"dtHash\": \"gfgfgef\",
\"expiryTime\": \"2023-06-21T04:47:09.700Z\",
\"issuedAt\": \"2023-06-21T04:42:09.700Z\",
\"jti\": \"id2fefef60\"
}
},
\"legacyEventType\": \"app.auth.sso\",
\"transaction\": {
\"type\": \"WEB\",
\"id\": \"xxx\",
\"detail\": {}
},
\"uuid\": \"xxx\",
\"version\": \"0\",
\"request\": {
\"ipChain\": [
{
\"ip\": \"xxx.xxxx.xx\",
\"geographicalContext\": {
\"city\": \"XXX\",
\"state\": \"xxx\",
\"country\": \"Ixx\",
\"postalCode\": \"xx\",
\"geolocation\": {
\"lat\": \"xxx\",
\"lon\": \"xxx\"
}
},
\"version\": \"V4\",
\"source\": null
}
]
},
\"target\": [
{
\"id\": \"trtrAEk2357\",
\"type\": \"AppInstance\",
\"alternateId\": \"cisco\",
\"displayName\": \"ciscot\",
\"detailEntry\": {
\"signOnModeType\": \"SAML_2_0\"
}
},
{
\"id\": \"0ua5zuozt0CEFGIB7357\",
\"type\": \"AppUser\",
\"alternateId\": \"xxxx\",
\"displayName\": \"xxx\",
\"detailEntry\": null
}
]
}
{
\"actor\": {
\"id\": \"xxx\",
\"type\": \"User\",
\"alternateId\": \"xxx\",
\"displayName\": \"xxx\",
\"detailEntry\": null
},
\"client\": {
\"userAgent\": {
\"rawUserAgent\": \"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36\",
\"os\": \"Mac OS X\",
\"browser\": \"CHROME\"
},
\"zone\": \"null\",
\"device\": \"Computer\",
\"id\": null,
\"ipAddress\": \"xxxx\",
\"geographicalContext\": {
\"city\": \"xxi\",
\"state\": \"xx\",
\"country\": \"xx\",
\"postalCode\": \"xx\",
\"geolocation\": {
\"lat\": \"xx\",
\"lon\": \"xx6\"
}
}
},
\"device\": null,
\"authenticationContext\": {
\"authenticationProvider\": null,
\"credentialProvider\": null,
\"credentialType\": null,
\"issuer\": null,
\"interface\": null,
\"authenticationStep\": 0,
\"externalSessionId\": \"1xxx\"
},
\"displayMessage\": \"Evaluation of sign-on policy\",
\"eventType\": \"policy.evaluate_sign_on\",
\"outcome\": {
\"result\": \"ALLOW\",
\"reason\": \"Sign-on policy evaluation resulted in REQUIRE_FACTOR\"
},
\"published\": \"2023-06-21T04:42:09.551Z\",
\"securityContext\": {
\"asNumber\": \"xx\",
\"asOrg\": \"google\",
\"isp\": \"google\",
\"domain\": \"googleusercontent.com\",
\"isProxy\": false
},
\"severity\": \"INFO\",
\"debugContext\": {
\"debugData\": {
\"authnRequestId\": \"xxx\",
\"requestId\": \"xxx\",
\"authMethodFirstVerificationTime\": \"2023-06-21T04:42:07Z\",
\"dtHash\": \"88fc37626c5fd644f5b668d172e978xxxxx\",
\"authMethodFirstType\": \"OKTA_VERIFY_PUSH\",
\"authMethodFirstEnrollment\": \"opfrp4q83eGFPVdFx357\",
\"requestUri\": \"/app/cisco_prismaaccessnew_1/exk5z8j61uVsvksss7/sso/saml\",
\"url\": \"/app/cisco_prismaaccessnew_1/exk5z8j61uVsvkdn6357/sso/saml?SAMLRequest=PHNccddddVzdCB4bWxuczpzYW1scD0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOnByb3RvY29sIiBBc3NlcnRpb25Db25zdddddd9Imh0dHBzOi8vY3AtdnBuLmNvbHBhbC5jb206NDQzL1NBTUwyMC9TUC9BQ1MiIERlc3RpbmF0aW9uPSJodHRwczovL3Nzby5jb2xwYWwuY29tL2FwcC9jb2xnYXRlcGFsbW9saXZlX3ByaXNtYWFjY2Vzc25ld18xL2V4azV6OGo2MXVWc3ZrZG42MzU3L3Nzby9zYW1sIiBJRD0iXzdhNmQ1NWZjMDlmYWYzYzJiOGZmODEzYWRhNDhhMDYwIiBJc3N1ZUluc3RhbnQ9IjIwMjMtMDYtMjFUMDQ6NDE6NDBaIiBQcm90b2NvbEJpbmRpbmc9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjIuMDpiaW5kaW5nczpIVFRQLVBPU1QiIFZlcnNpb249IjIuMCI%2BPHNhbWw6SXNzdWVyIHhtbG5zOnNhbWw9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjIuMDphc3NlcnRpb24iPmh0dHBzOi8vY3AtdnBuLmNvbHBhbC5jb206NDQzL1NBTUwyMC9TUDwvc2FtbDpJc3N1ZXI%2BPC9zYW1scDpBdXRoblJlcXVlc3Q%2B&RelayState=M1MMAJOsVmQzMDIzZGJhYTJlYThhOWE4MzA0MjVmZjVmMzAyOGRhNjc4&OKTA_INVALID_SESSION_REPOST=true&fromLoginToken=dddddddddddddddddddddg-KswZ4hoNAw2B4A3JJK9UqslopoakK8M12S6MfRvLjdrBWRFDo7289iCzYy0QA879iRF-ZQoJyeEzr4sXKrgySnjpdHn10SvudyTepTjbkfA4HM7hD7CUpYbw3zX97iqxZ-iHwzLAWmhcFEcQorruhuHDePIlvDanDvxWQfVihZKxKqF7cB0600-iWeL0Np9pXo-LD30_1OSNH9yLkV52W3OZYu4sQqTbEw0thBvZ6LTw\",
\"logOnlySecurityData\": \"{\\\"risk\\\":{\\\"level\\\":\\\"LOW\\\"},\\\"behaviors\\\":{\\\"New Geo-Location\\\":\\\"NEGATIVE\\\",\\\"New Device\\\":\\\"NEGATIVE\\\",\\\"New IP\\\":\\\"NEGATIVE\\\",\\\"New State\\\":\\\"NEGATIVE\\\",\\\"New Country\\\":\\\"NEGATIVE\\\",\\\"Speed based login\\\":\\\"NEGATIVE\\\",\\\"New City\\\":\\\"NEGATIVE\\\"}}\"
}
},
\"legacyEventType\": null,
\"transaction\": {
\"type\": \"WEB\",
\"id\": \"xxx\",
\"detail\": {}
},
\"uuid\": \"xxxx\",
\"version\": \"0\",
\"request\": {
\"ipChain\": [
{
\"ip\": \"xxx\",
\"geographicalContext\": {
\"city\": \"xxx\",
\"state\": \"xx\",
\"country\": \"India\",
\"postalCode\": \"xxx\",
\"geolocation\": {
\"lat\": \"xx\",
\"lon\": \"xxx\"
}
},
\"version\": \"V4\",
\"source\": null
}
]
},
\"target\": [
{
\"id\": \"xxxx\",
\"type\": \"PolicyRule\",
\"alternateId\": \"unknown\",
\"displayName\": \"MFA Always\",
\"detailEntry\": null
},
{
\"id\": \"0xxx\",
\"type\": \"AppInstance\",
\"alternateId\": \"cisco\",
\"displayName\": \"cisco\",
\"detailEntry\": {
\"signOnModeType\": \"SAML_2_0\",
\"signOnModeEvaluationResult\": \"ALLOW\"
}
}
]
}", "
")
| mvexpand data
| eval _time = strptime(json_extract(data, "published"), "%FT%H:%M:%S.%3NZ")
```| eval 0keys = json_keys(data)```
| rename data AS _raw
| spath path=target{}
| mvexpand target{}
| spath input=target{} path=type
| where type="AppInstance"
| spath input=target{} path=alternateId
| spath path=legacyEventType
| spath path=eventType
| spath path=displayMessage
| fields - _raw target{}
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@yuanliu
Hi,
These are Okta Events 1.
{
"actor": {
"id": "xxxx",
"type": "User",
"alternateId": "xyz@cisco.com",
"displayName": "xyz",
"detailEntry": null
},
"client": {
"userAgent": {
"rawUserAgent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36",
"os": "Windows 10",
"browser": "CHROME"
},
"zone": "null",
"device": "Computer",
"id": null,
"ipAddress": "192.168.1.1",
"geographicalContext": {
"city": "London",
"country": "UK",
"postalCode": "Lu20al",
"geolocation": {
"lat": 80.4692,
"lon": -54.6996
}
}
},
"device": null,
"authenticationContext": {
"authenticationProvider": null,
"credentialProvider": null,
"credentialType": null,
"issuer": null,
"interface": null,
"authenticationStep": 0,
"externalSessionId": "fhiorifjds;kkd"
},
"displayMessage": "Verify user identity",
"eventType": "user.authentication.verify",
"outcome": {
"result": "SUCCESS",
"reason": null
},
"published": "2023-07-17T19:01:40.062Z",
"securityContext": {
"asNumber": 396982,
"asOrg": "Cisco networks inc",
"isp": "google",
"domain": "."
"isProxy": false
},
"severity": "INFO",
"debugContext": {
"debugData": {
"authnRequestId": "uofwiofkw[",
"behaviors": "{New Geo-Location=NEGATIVE, New Device=NEGATIVE, New IP=NEGATIVE, New State=NEGATIVE, New Country=NEGATIVE, Speed based login=NEGATIVE, New City=NEGATIVE}",
"requestId": "jfjslfjljkkjk",
"dtHash": "ouioeuijide",
"risk": "{level=LOW}",
"requestUri": "/app/UserHome",
"url": "xxxxxxxxx"
}
},
"legacyEventType": null,
"transaction": {
"type": "WEB",
"id": "xxxx",
"detail": {}
},
"uuid": "xxxx",
"version": "0",
"request": {
"ipChain": [
{
"ip": "192.168.1.1",
"geographicalContext": {
"city": "London",
"country": "Uk",
"postalCode": "Lu20al",
"geolocation": {
"lat": 80.6992,
"lon": -45.4996
}
},
"version": "V4",
"source": null
}
]
},
"target": null
}
2.
{
"actor": {
"id": "xxxx",
"type": "User",
"alternateId": "xxxx",
"displayName": "xxx",
"detailEntry": null
},
"client": {
"userAgent": {
"rawUserAgent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36",
"os": "Windows 10",
"browser": "CHROME"
},
"zone": "null",
"device": "Computer",
"id": "okta.2xxxxxxxxxx",
"ipAddress": "xxxx",
"geographicalContext": {
"city": "xxx",
"state": "xxx",
"country": "xx",
"postalCode": "xxx",
"geolocation": {
"lat": xxx,
"lon": -xxx
}
}
},
"device": null,
"authenticationContext": {
"authenticationProvider": null,
"credentialProvider": null,
"credentialType": null,
"issuer": null,
"interface": null,
"authenticationStep": 0,
"externalSessionId": "unknown"
},
"displayMessage": "User single sign on to app",
"eventType": "user.authentication.sso",
"outcome": {
"result": "SUCCESS",
"reason": null
},
"published": "2023-07-17T19:01:41.401Z",
"securityContext": {
"asNumber": 5768,
"asOrg": "Cisco networks inc",
"isp": "google",
"domain": ".",
"isProxy": false
},
"severity": "INFO",
"debugContext": {
"debugData": {
"initiationType": "NA",
"redirectUri": "https://sso.cisco.com/enduser/callback",
"requestId": "xx",
"dtHash": "xxx",
"signOnMode": "OpenID Connect",
"requestUri": "/oauth2/v1/token",
"threatSuspected": "false",
"url": "/oauth2/v1/token?"
}
},
"legacyEventType": "app.auth.sso",
"transaction": {
"type": "WEB",
"id": "xxx",
"detail": {}
},
"uuid": "xxxxx",
"version": "0",
"request": {
"ipChain": [
{
"ip": "xxxx",
"geographicalContext": {
"city": "xxx",
"state": "xxx",
"country": "xxx",
"postalCode": "xx",
"geolocation": {
"lat": xxx
"lon": xxx
}
},
"version": "V4",
"source": null
}
]
},
"target": [
{
"id": "0oa8kdeb4lLaTivPe357",
"type": "AppInstance",
"alternateId": "Okta Dashboard",
"displayName": "Okta Dashboard",
"detailEntry": {
"signOnModeType": "OPENID_CONNECT"
}
},
{
"id": "xxx",
"type": "AppUser",
"alternateId": "xxx",
"displayName": "xxxx",
"detailEntry": null
}
]
}
3.
{
"actor": {
"id": "xxx",
"type": "User",
"alternateId": "xxx",
"displayName": "xxx",
"detailEntry": null
},
"client": {
"userAgent": {
"rawUserAgent": "xxx",
"os": "Unknown mobile",
"browser": "UNKNOWN"
},
"zone": "null",
"device": "Mobile",
"id": null,
"ipAddress": "xxx",
"geographicalContext": {
"city": "xxr",
"state": "xxx",
"country": "xxx",
"postalCode": "xx",
"geolocation": {
"lat": xxx,
"lon": -xx
}
}
},
"device": null,
"authenticationContext": {
"authenticationProvider": "FACTOR_PROVIDER",
"credentialProvider": "OKTA_CREDENTIAL_PROVIDER",
"credentialType": null,
"issuer": null,
"interface": null,
"authenticationStep": 0,
"externalSessionId": "xxxx"
},
"displayMessage": "Authentication of user via MFA",
"eventType": "user.authentication.auth_via_mfa",
"outcome": {
"result": "SUCCESS",
"reason": null
},
"published": "2023-07-17T19:02:03.863Z",
"securityContext": {
"asNumber": 701,
"asOrg": "verizon",
"isp": "verizon",
"domain": "verizon.net",
"isProxy": false
},
"severity": "INFO",
"debugContext": {
"debugData": {
"authnRequestId": "xxx",
"behaviors": "{New Geo-Location=NEGATIVE, New Device=NEGATIVE, New IP=NEGATIVE, New State=NEGATIVE, New Country=NEGATIVE, Speed based login=NEGATIVE, New City=NEGATIVE}",
"requestId": "xxxx",
"risk": "{level=LOW}",
"requestUri": "xx",
"threatSuspected": "false",
"factor": "OKTA_VERIFY_PUSH",
"url": "xxx"
}
},
"legacyEventType": "core.user.factor.attempt_success",
"transaction": {
"type": "WEB",
"id": "xxx",
"detail": {}
},
"uuid": "xxxxxxxxx",
"version": "0",
"request": {
"ipChain": [
{
"ip": "xxx",
"geographicalContext": {
"city": "xxx",
"state": "xxx",
"country": "xxx",
"postalCode": "xx",
"geolocation": {
"lat": xxx
"lon": xxx
}
},
"version": "V4",
"source": null
}
]
},
"target": [
{
"id": "xxx",
"type": "User",
"alternateId": "xxx",
"displayName": "xxx",
"detailEntry": null
}
]
}
Cisco Events:
1.
{
"actor": {
"id": "xxx",
"type": "User",
"alternateId": "xxx",
"displayName": "xxx",
"detailEntry": null
},
"client": {
"userAgent": {
"rawUserAgent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36",
"os": "Windows 10",
"browser": "CHROME"
},
"zone": "null",
"device": "Computer",
"id": null,
"ipAddress": "xxxx",
"geographicalContext": {
"city": "xxx",
"state": "xxx",
"country": "xxx",
"postalCode": "xxx",
"geolocation": {
"lat": xx,
"lon": -xxx
}
}
},
"device": null,
"authenticationContext": {
"authenticationProvider": null,
"credentialProvider": null,
"credentialType": null,
"issuer": null,
"interface": null,
"authenticationStep": 0,
"externalSessionId": "xxxx"
},
"displayMessage": "Evaluation of sign-on policy",
"eventType": "policy.evaluate_sign_on",
"outcome": {
"result": "ALLOW",
"reason": "Sign-on policy evaluation resulted in REQUIRE_FACTOR"
},
"published": "2023-07-18T12:09:36.137Z",
"securityContext": {
"asNumber": 396982,
"asOrg": "Cisco networks inc",
"isp": "google",
"domain": ".",
"isProxy": false
},
"severity": "INFO",
"debugContext": {
"debugData": {
"authnRequestId": "xxx",
"requestId": "xx",
"authMethodFirstVerificationTime": "2023-07-18T12:09:34Z",
"dtHash": "4xxxe",
"authMethodFirstType": "OKTA_VERIFY_PUSH",
"authMethodFirstEnrollment": "oxxx",
"requestUri": "/login/sessionCookieRedirect",
"threatSuspected": "false",
"url": "/login/sessionCookieRedirect?",
"logOnlySecurityData": "{\"risk\":{\"level\":\"LOW\"},\"behaviors\":{\"New Geo-Location\":\"NEGATIVE\",\"New Device\":\"NEGATIVE\",\"New IP\":\"NEGATIVE\",\"New State\":\"NEGATIVE\",\"New Country\":\"NEGATIVE\",\"Speed based login\":\"NEGATIVE\",\"New City\":\"NEGATIVE\"}}"
}
},
"legacyEventType": null,
"transaction": {
"type": "WEB",
"id": "xxx,
"detail": {}
},
"uuid": "xx",
"version": "0",
"request": {
"ipChain": [
{
"ip": "xxx",
"geographicalContext": {
"city": "Somerset",
"state": "xx",
"country": "xxx",
"postalCode": "xxx",
"geolocation": {
"lat": xxx,
"lon": -xxx
}
},
"version": "V4",
"source": null
}
]
},
"target": [
{
"id": "xxx",
"type": "PolicyRule",
"alternateId": "unknown",
"displayName": "MFA Always",
"detailEntry": null
},
{
"id": "xxx",
"type": "AppInstance",
"alternateId": "Cisco",
"displayName": "Cisco",
"detailEntry": {
"signOnModeType": "SAML_2_0",
"signOnModeEvaluationResult": "ALLOW"
}
}
]
}
2.
{
"actor": {
"id": "xxxxxxx",
"type": "User",
"alternateId": "xxx",
"displayName": "xxx",
"detailEntry": null
},
"client": {
"userAgent": {
"rawUserAgent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36",
"os": "Windows 10",
"browser": "CHROME"
},
"zone": "null",
"device": "Computer",
"id": null,
"ipAddress": "xxx",
"geographicalContext": {
"city": "xxx",
"state": "xxx",
"country": "xxx",
"postalCode": "xxxx",
"geolocation": {
"lat": xxxx,
"lon": -xxxx
}
}
},
"device": null,
"authenticationContext": {
"authenticationProvider": null,
"credentialProvider": null,
"credentialType": null,
"issuer": null,
"interface": null,
"authenticationStep": 0,
"externalSessionId": "xxxx"
},
"displayMessage": "User single sign on to app",
"eventType": "user.authentication.sso",
"outcome": {
"result": "SUCCESS",
"reason": null
},
"published": "2023-07-18T12:09:36.277Z",
"securityContext": {
"asNumber": 396982,
"asOrg": "cisco networks inc",
"isp": "google",
"domain": ".",
"isProxy": false
},
"severity": "INFO",
"debugContext": {
"debugData": {
"audience": "https://cp-vpn.cisco.com:443/SAML20/SP",
"subject": "xxxx",
"signOnMode": "SAML 2.0",
"authenticationClassRef": "urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport",
"authTime": "2023-07-18T12:09:27.141Z",
"requestUri": "/login/sessionCookieRedirect",
"issuer": "http://www.okta.com/xxxx",
"url": "/login/sessionCookieRedirect?",
"initiationType": "SP_INITIATED",
"authnRequestId": "xxxx",
"requestId": "xxxxx",
"dtHash": "xxxxx",
"expiryTime": "2023-07-18T12:14:36.268Z",
"issuedAt": "2023-07-18T12:09:36.268Z",
"threatSuspected": "false",
"jti": "xxx"
}
},
"legacyEventType": "app.auth.sso",
"transaction": {
"type": "WEB",
"id": "xxxxx",
"detail": {}
},
"uuid": "xxx",
"version": "0",
"request": {
"ipChain": [
{
"ip": "xxx",
"geographicalContext": {
"city": "xxx",
"state": "xxxx",
"country": "United xxx",
"postalCode": "xxx",
"geolocation": {
}
},
"version": "V4",
"source": null
}
]
},
"target": [
{
"id": "xxxx",
"type": "AppInstance",
"alternateId": "Cisco",
"displayName": "Cisco",
"detailEntry": {
"signOnModeType": "SAML_2_0"
}
},
{
"id": "xxxxxxxxxxxxxxxxxxx",
"type": "AppUser",
"alternateId": "xyz.com",
"displayName": "xyz",
"detailEntry": null
}
]
}
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you pls edit this search...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
..
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
..
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To confirm, the Okta info can be discerned from displayMessage when eventType=user.*, and Cisco Anyconnect info can be from targetAppAlternateId when sourcetype=Okta*. Correct? I want to push the solution further by assuming that
- "User single sign on to app" is the complete value for displayMessage.
- targetAppAlternateId begins with "Cisco" or "Anyconnect".
These assumptions are used to make the base search narrower. You can adjust these or abandon them.
More importantly for efficiency, usually you want to avoid join. So I'm combining the two searches into the base search. Following that, it's just an exercise of stats.
index=xyz ((eventType=user.* displayMessage = "User single sign on to app")
OR (sourcetype=Okta* (targetAppAlternateId = "cisco *" OR targetAppAlternateId = "anyconnect*")) earliest=-30d
| eval logon = case(match(displayMessage, "User single sign on to app"), "Okta", match(targetAppAlternateId, "anyconnect | Cisco"), "VPN")
| bin span=1d@d _time
| stats values(logon) as logon by _time userid
| eval connectivity_type = if(logon == "Okta", if(logon == "VPN", "VPN", "On-prem"), if(isnull(logon), "none", "!!Anomaly - no Okta, but on VPN"))Given that Cisco Anyconnect only occurs in sourcetype Okta*, the anomaly I'm trying to flag is probably impossible. So, you can get rid of that, too.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm confused. I didn't use anything like 1 == 1. I also did not try to define "none" in case, because it is more expressive to just use if based on your definition of VPN vs on-prem. In fact, if sourcetype is always okta*, the base search can be further simplified. But this begs the question: Can displayMessage and targetAppAlternateId appear in the same event? If a VPN logon event satisfies both match(targetAppAlternateId, "anyconnect|Cisco") and match(displayMessage, "User single sign on to app"), you would be correct that the anomaly is impossible so you don't have to capture it. The order of the first case function, meanwhile, needs to be adjusted. In fact, it would best be expressed as nested if.
index=xyz ((eventType=user.* displayMessage = "User single sign on to app")
OR (sourcetype=Okta* (targetAppAlternateId = "cisco*" OR targetAppAlternateId = "anyconnect*")) earliest=-30d
| eval logon = case(match(targetAppAlternateId, "anyconnect|Cisco"), "VPN", match(displayMessage, "User single sign on to app"), "Okta")
| bin span=1d@d _time
| stats values(logon) as logon by _time userid
| eval connectivity_type = if(logon == "Okta", if(logon == "VPN", "VPN", "On-prem"), "none")- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How we can bound this to time as last day i was on okta and in the same day i logged in via VPN
so it should show okta and VPN
bounding this with time will be like
Only Okta On Prem
in same day if Okta + VPN = VPN so for same date it should show On Prem & VPN
How we can achieve this ?
Thanks..
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
bounding this with time will be likeOnly Okta On Prem
in same day if Okta + VPN = VPN so for same date it should show On Prem & VPN
This is the reason why I asked for clarification: Do displayMessage and targetAppAlternateId appear in the same event? One step further: If I use VPN, will one single event satisfy both match(targetAppAlternateId, "anyconnect|Cisco") and match(displayMessage, "User single sign on to app")? My previous reply stated that the search was based on these being true as I inferred from your previous message. If these are not true, my first search should have already covered the case (save some additional assumption about actual matches). To really hone the solution, you will need to illustrate sample data (anonymize as needed), explain key features in the dataset that volunteers will need to pay attention to, and illustrate the desired results.
Here, I will relist the past two "solutions" based on data assumptions with some small refinements.
1. Solution 2, if a VPN logon will show in single event satisfying match(targetAppAlternateId, "anyconnect|Cisco") and match(displayMessage, "User single sign on to app"); an on-prem logon showing only events satisfying match(displayMessage, "User single sign on to app") and NOT match(targetAppAlternateId, "anyconnect|Cisco").
index=xyz sourcetype=Okta* ((eventType=user.* displayMessage = "User single sign on to app")
OR (targetAppAlternateId = "cisco*" OR targetAppAlternateId = "anyconnect*") earliest=-30d
| eval logon = case(match(targetAppAlternateId, "anyconnect|Cisco"), "VPN", match(displayMessage, "User single sign on to app"), "Okta")
| bin span=1d@d _time
| stats values(logon) as logon by _time userid
| eval connectivity_type = if(logon == "Okta", if(logon == "VPN", "VPN", "On-prem"), "none")This should work because match(targetAppAlternateId, "anyconnect|Cisco") would have implied match(displayMessage, "User single sign on to app") when data characteristics is as described.
2. If Akta logon and VPN logon are totally independent events, i.e., match(targetAppAlternateId, "anyconnect|Cisco") does not imply match(displayMessage, "User single sign on to app"),
index=xyz sourcetype=Okta* ((eventType=user.* displayMessage = "User single sign on to app")
OR (targetAppAlternateId = "cisco*" OR targetAppAlternateId = "anyconnect*) earliest=-30d
| eval logon = case(match(displayMessage, "User single sign on to app"), "Okta", match(targetAppAlternateId, "anyconnect|Cisco"), "VPN")
| bin span=1d@d _time
| stats values(logon) as logon by _time userid
| eval connectivity_type = if(logon == "Okta", if(logon == "VPN", "VPN", "On-prem"), if(isnull(logon), "none", "!!Anomaly - no Okta, but on VPN"))If your data have other characteristics not covered above, you need to elaborate.