Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How can I do a sum of count for if statement?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
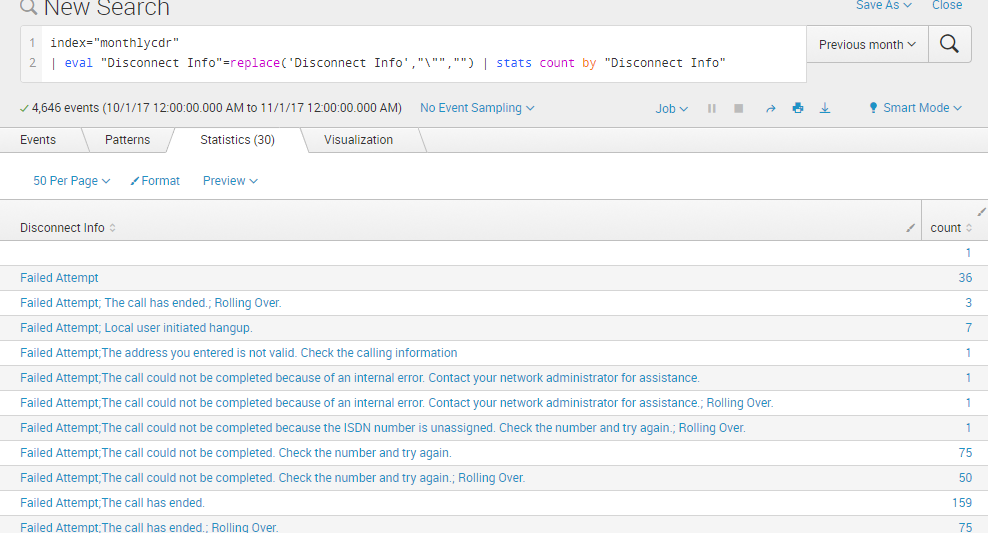
When I do a stats count by a specific column. The count for each of them work. Here is the picture:
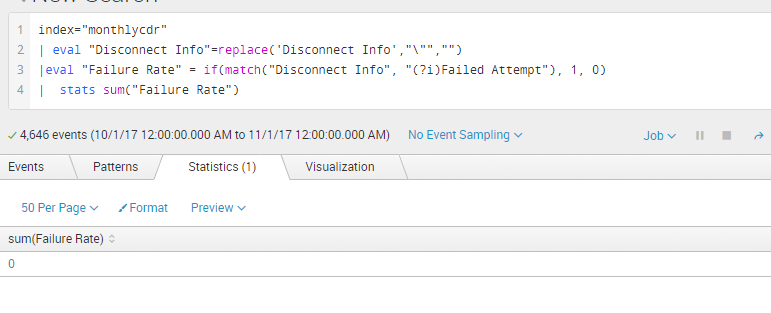
But when I actually try to count only the Failed Attempt call. The result is 0. Did I do something wrong here?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In the eval command expressions (and where command too), if a field name contains spaces, you need to enclose them in single quotes not double quotes. With double quotes, they are treated as literal string instead of fields. You did it correctly in line 2 (replace command) but missed in line three. Correcting that would resolve your issue.
Like this
index="monthlycdr"
| eval "Disconnect Info"=replace('Disconnect Info' ,"\"","")
| eval "Failure Rate" = if(match('Disconnect Info',"(?i)Failed Attempt"),1,0)
| stats sum("Failure Rate")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can you avoid the spaces? SPL works better, generally, without them.
index=monthlycdr
|eval DisconnectInfo=replace('Disconnect Info',"\"","")
|eval "FailureRate"=if(match(DisconnectInfo,"(?i)Failed Attempt"),1,0)
|stats sum(FailureRate) as "Failure Rate"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In the eval command expressions (and where command too), if a field name contains spaces, you need to enclose them in single quotes not double quotes. With double quotes, they are treated as literal string instead of fields. You did it correctly in line 2 (replace command) but missed in line three. Correcting that would resolve your issue.
Like this
index="monthlycdr"
| eval "Disconnect Info"=replace('Disconnect Info' ,"\"","")
| eval "Failure Rate" = if(match('Disconnect Info',"(?i)Failed Attempt"),1,0)
| stats sum("Failure Rate")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think following is the only query required. | eval "Disconnect Info"=replace('Disconnect Info' ,"\"","") before stats is required only if double quotes may be present between "Failed Attempt" pattern being matched.
index="monthlycdr"
| stats count(eval(match('Disconnect Info',"(?i)^Failed Attempt"))) as "Failed Attempt"
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks guys