Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Help with stats: identify the latest result for ea...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
mydog8it
Builder
10-26-2015
02:59 PM
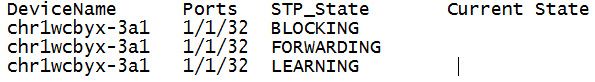
I am searching through the router and switch syslog data trying to find spanning tree state changes for a given time period. Once found I want to put the device name, port and STP state in a table. I also want to identify which of the STP states(BLOCKING, LEARNING, FORWARDING) for each Device/interface combination is the Current State. The stats string below identifies all but the current state correctly:
Search command |stats dc(DeviceName) AS "Device Names" values(Port) AS "Ports" dc(Port) AS "Ps" values(STP_State) AS "State" by DeviceName,STP_State
| eval stats first(STP_State)="Current State"
Desired output would look something like:
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
somesoni2
Revered Legend
10-26-2015
06:31 PM
Try this
Search command |stats dc(DeviceName) AS "Device Names" values(Port) AS "Ports" dc(Port) AS "Ps" values(STP_State) AS "State" latest(STP_State) as "Current State" by DeviceName
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
somesoni2
Revered Legend
10-26-2015
06:31 PM
Try this
Search command |stats dc(DeviceName) AS "Device Names" values(Port) AS "Ports" dc(Port) AS "Ps" values(STP_State) AS "State" latest(STP_State) as "Current State" by DeviceName
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Richfez

SplunkTrust
10-26-2015
04:10 PM
What does the output of the stats command get you (without the eval)? Just a line or two would be fine.
Get Updates on the Splunk Community!
Index This | When is October more than just the tenth month?
October 2025 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with this ...
Observe and Secure All Apps with Splunk
Join Us for Our Next Tech Talk: Observe and Secure All Apps with SplunkAs organizations continue to innovate ...
What’s New & Next in Splunk SOAR
Security teams today are dealing with more alerts, more tools, and more pressure than ever. Join us for an ...