Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Help with creating an index search based on th...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Help with creating an index search based on the _time value (beginner)
Beginner here, I'm trying to run a search on unique logins for a web-based application. The current logs, however, do not indicate the information I need to be able to count which app the user logged into.
It may be easier to illustrate the search:
What I am trying to archive is on the _time value all those events (hidden) are triggered at the exact same time. I want to use that value as a unique ID to evaluate all the events that happened at that time as a group.
The information I require is from a_app
Could some explain to me a way to archive this?
I guess in summary if the UserAuthicationQuery had an actual log that identified what the user was logging into it would then work but the a_app for this process is done in a central location and not associated with the actual app the user is entering.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
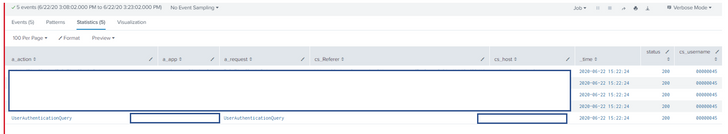
As mentioned this is the closest I have:
But it includes every event at those timestamps. I only want the timestamp in which a_action = UserAuthenticationQuery. if I include UserAuthenticationQuery in search then it drops off all events. I don't know why it still doesn't append the multiple app values under appList field?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ahh, why do you use stats in between ? It removes the UserAuthenticationQuery field from the results.
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So I should remove it? If I do, it doesn't change anything I still get 2,730 results. I grabbed this from you on the first page you mentioned:
As you said , it might not be accurate. However, if you want to get the app list for a user with time as a common factor (seconds' precision) , try this
"your search" |eval timeIdentifier=strftime(_time,"%Y-%m-%d-%H-%M-%S") |stats values(a_app) as appList by timeIdentifier,cs_username
appList should have the list of apps. We converted time to string just to make sure that we take until seconds precision. You may user _time directly as well
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
that was for that specific solution.
Try the latest search please without the stats. Also have a look at the search's construction to understand how it works. That will help you to troubleshoot
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks again, yes I did remove it as mentioned. It didn't resolve anything other then list all events and not in a table format.
I have looked many times at the search construction and tried many things... I get what I want but do not understand the logic on how to link the two time events to no another.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
post your current search and sample events
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi sorry for the delay. I have worked out an alternative to my search. I have another question. Is there a way to dedup a field by another event?
I seem to being getting my results but when I dedup username, it just randomly selects an event and lists that in my stats. I want to only dedup the username based on UserAuthenticationQuery event?
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
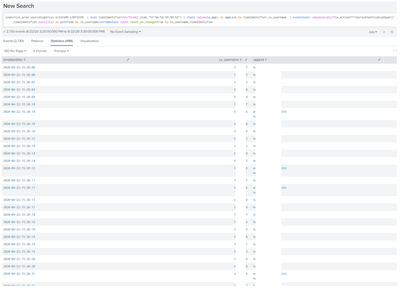
As mentioned this is the closest I have:
But it includes every event at those timestamps. I only want the timestamp in which a_action = UserAuthenticationQuery. if I include UserAuthenticationQuery in search then it drops off all events. I don't know why it still doesn't append the multiple app values under appList field?