Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Search
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Has anyone been able to figure out how to search i...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Has anyone been able to figure out how to search indexed XmlWinEventLog sourcetype sample logs in the Ingest Action GUI?
tjones130
Engager
05-10-2023
06:05 AM
Has anyone been able to figure out how to search indexed XmlWinEventLog sourcetype sample logs in the Ingest Action GUI? The actual search being used uses the |where command which seems to be the issue.
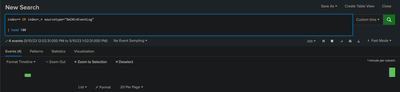
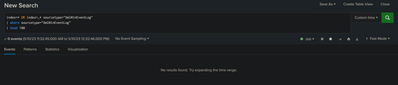
index=* OR index=_* sourcetype="XmlWinEventLog" | where sourcetype="XmlWinEventLog" | head 100
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fjiang

Splunk Employee
07-25-2024
02:47 PM
Hi there!
This was published as a known issue first in 9.0.2: https://docs.splunk.com/Documentation/Splunk/9.0.2/ReleaseNotes/KnownIssues
See the entry for SPL-235416.
The preview UI in Ingest Actions has since been fixed in:
Splunk Enterprise version 9.0.5+
Splunk Cloud Platform version 9.0.2303+
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ITWhisperer

SplunkTrust
05-10-2023
06:26 AM
where is case-sensitive, search is not. Check the exact spelling and case of the sourcetype you are searching for.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
tjones130
Engager
05-10-2023
06:46 AM
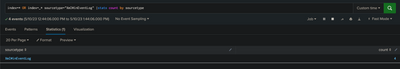
I have tried multiple variations of case-sensitivity, with no luck. The sourcetype that returns when running index=* sourcetype="XmlWinEventLog" is "XmlWinEventLog".
Get Updates on the Splunk Community!
Why am I not seeing the finding in Splunk Enterprise Security Analyst Queue?
(This is the first of a series of 2 blogs).
Splunk Enterprise Security is a fantastic tool that offers robust ...
Index This | What are the 12 Days of Splunk-mas?
December 2024 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with another ...
Get Inspired! We’ve Got Validation that Your Hard Work is Paying Off
We love our Splunk Community and want you to feel inspired by all your hard work! Eric Fusilero, our VP of ...