Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Getting text from raw event with regex
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi everyone,
I'm trying to get a simple text from a raw event, but I can't make it works.
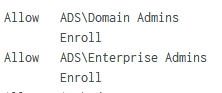
The event looks like this:
and my regex looks like this:
| rex field=_raw "Allow\s(?<GroupName>\w.+)\s+Enroll"
my issue is, that I only going to get a few of those groups, but not all... for example I will get the Domain Users but not the Enterprise Users which is in the same raw file...
Could please someone help me with this regex?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's not clear to me what the problem is, but I think the rex command is not extracting all instances of the "Allow" field. If so, then the max_match option should help.
| rex field=_raw max_match=0 "Allow\s(?<GroupName>\w.+)\s+Enroll" If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's not clear to me what the problem is, but I think the rex command is not extracting all instances of the "Allow" field. If so, then the max_match option should help.
| rex field=_raw max_match=0 "Allow\s(?<GroupName>\w.+)\s+Enroll" If this reply helps you, Karma would be appreciated.