- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Eliminate Specific results & include specific ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
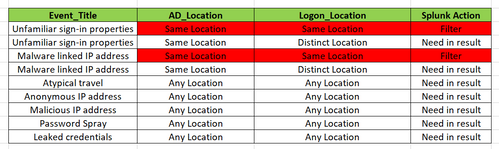
If the user's AD & Logon locations are the same, then I am filtering the results with the below query.
| rex field=Logon_Location "(?<logloc>\w\w$)"
| rex field=AD_Location "(?<adloc>\w\w$)"
| where logloc!=adloc
Now I want to filter the results for only below 2 "Event_Titles".
Event_Title = "Unfamiliar sign-in properties"
Event_Tilte = "Malware linked IP address"
And I want to also get all Event_Titles if the user's AD & Logon location is unique and different.
Please help here.
@scelikok @soutamo @saravanan90 @thambisetty @ITWhisperer @gcusello @bowesmana @to4kawa @woodcock
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| rex field=Logon_Location "(?<logloc>\w\w$)"
| rex field=AD_Location "(?<adloc>\w\w$)"
| where logloc!=adloc OR (Event_Title != "Unfamiliar sign-in properties" AND Event_Title != "Malware linked IP address")- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is this what you mean?
| rex field=Logon_Location "(?<logloc>\w\w$)"
| rex field=AD_Location "(?<adloc>\w\w$)"
| where logloc!=adloc AND Event_Title != "Unfamiliar sign-in properties" AND Event_Tilte != "Malware linked IP address"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ITWhisperer Thanks much for your reply!
This query filters both Event_Title in the results.
But I want to get all Event_Title in the result & particularly filter, if AD & Logon locations are same for "Unfamiliar sign-in properties" & "Malware linked IP address"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does this match what you are asking for, i.e. only and all events for A in either ad loc or log loc so long as A is in ad loc and log loc at the same time for both the event titles you are interested in?
| ad loc | log loc | event title | keep |
| A | A | Unfamiliar sign-in properties | Yes |
| A | A | Malware linked IP address | Yes |
| A | B | Something else | Yes |
| B | A | Something else | Yes |
| B | B | Unfamiliar sign-in properties | No |
| B | C | Malware linked IP address | No |
| C | B | Malware linked IP address | No |
| B | C | Something else | No |
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ITWhisperer Thanks for your prompt reply.
Below is the requirement
Any Location means no matter it is Same or Distinct location but needs to capture in the result.
Below query is filtering results for same AD & Logon location for all the alerts.
But I want to filter for only for "Unfamiliar sign-in properties & Malware linked IP address" alert if the AD & Logon locations are different.
| rex field=Logon_Location "(?<logloc>\w\w$)"
| rex field=AD_Location "(?<adloc>\w\w$)"
| where logloc!=adloc
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| rex field=Logon_Location "(?<logloc>\w\w$)"
| rex field=AD_Location "(?<adloc>\w\w$)"
| where logloc!=adloc OR (Event_Title != "Unfamiliar sign-in properties" AND Event_Title != "Malware linked IP address")- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| rex field=Logon_Location "(?<logloc>\w\w$)"
| rex field=AD_Location "(?<adloc>\w\w$)"
| where logloc!=adloc OR Event_Title!= "Unfamiliar sign-in properties" |where logloc!=adloc OR Event_Title!= "Malware linked IP address"
@ITWhisperer Thanks much. Above also gives the same result.