Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Field extraction using rex
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I am new to splunk, I am trying to extract specific message from my log event. The pattern I am looking from below message
[ERROR] 2020-09-28T11:50:06.108Z 6012c275-5df5-4839-95a0-260057509041 |HLX|Task Failure Occured:{'jobid': 'FLOW-134', 'taskid': 'T-09', 'subtaskid': 'a88f6260-0180-11eb-9ccc-3e5cb494596a'}
I need to extract everything after |HLX| and create another field. Its fine even if it includes |HLX|. I have tried multiple patterns but none are working. Any help would be appreciated.
Thank you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @avanijjain16 ... i created a log event with your sample log and ran the rex from @493669 , it works fine. you just have to use the field namev (if ur field name is _raw, simply run "|rex field=_raw.. ") and ".+" or ".*" - both are same.
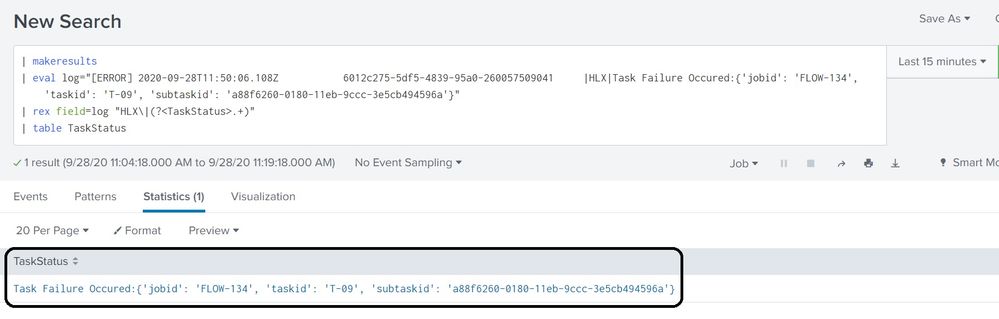
| makeresults
| eval log="[ERROR] 2020-09-28T11:50:06.108Z 6012c275-5df5-4839-95a0-260057509041 |HLX|Task Failure Occured:{'jobid': 'FLOW-134', 'taskid': 'T-09', 'subtaskid': 'a88f6260-0180-11eb-9ccc-3e5cb494596a'}"
| rex field=log "HLX\|(?<TaskStatus>.*)"
| table TaskStatus
Sekar
PS - If this or any post helped you in any way, pls consider upvoting, thanks for reading !
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @avanijjain16 ... i created a log event with your sample log and ran the rex from @493669 , it works fine. you just have to use the field namev (if ur field name is _raw, simply run "|rex field=_raw.. ") and ".+" or ".*" - both are same.
| makeresults
| eval log="[ERROR] 2020-09-28T11:50:06.108Z 6012c275-5df5-4839-95a0-260057509041 |HLX|Task Failure Occured:{'jobid': 'FLOW-134', 'taskid': 'T-09', 'subtaskid': 'a88f6260-0180-11eb-9ccc-3e5cb494596a'}"
| rex field=log "HLX\|(?<TaskStatus>.*)"
| table TaskStatus
Sekar
PS - If this or any post helped you in any way, pls consider upvoting, thanks for reading !
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So I did some search and found that it’s pre-pattern and then (? Creates new field name TaskStatus that follows HLX and matching with pattern .* (basically everything except /n) . I have some logs where there is chance of \n coming in. It would not match in those cases. Any idea how to allow that. \n can appear any where followed by HLX.
"HLX\|(?<TaskStatus>.*)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content