Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Error using lookup command
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Error using lookup command
I am running the below query,
sourcetype="email" | rename SenderAddress as indicator |lookup tci indicator output type,rating|where isnotnull(type)|dedup indicator|table indicator FromIP rating type
It all works fine except if I add a field named attrib.val or tag.name like below
sourcetype="email" | rename SenderAddress as indicator |lookup tci indicator output type,rating,tag.name|where isnotnull(type)|dedup indicator|table indicator FromIP rating type tag.name
It throws error like,
Error in 'lookup' command: Could not find all of the specified destination fields in the lookup table.
But actually I have a field named tag.name in tci lookup. I suspect if it is because of"." in the field names.
Kindly suggest.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Fields containing dots should not cause any problem. It works in 8.x.
Provide output field in double-quotes.
sourcetype="email" | rename SenderAddress as indicator | lookup tci indicator output type, rating, "tag.name"
If this reply helps you, an upvote/like would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @manjunathmeti
I tried like below,
sourcetype="email*" | rename SenderAddress as indicator |lookup tci indicator output type,"tag.name" as tag|where isnotnull(type)|dedup indicator|table indicator tag
Even this is returning the error,
Error in 'lookup' command: Could not find all of the specified destination fields in the lookup table.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try to run the query with CSV file directly. If it works then check the definition for lookup tci and see if proper CSV file is configured to it.
sourcetype="email*" | rename SenderAddress as indicator | lookup tci_filename.csv indicator OUTPUT type, "tag.name" as tag- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @manjunathmeti
The lookup tci is of type KV store and not file type.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am not sure if the lookup command on KVstore collection supports fields with dotted notation. Try this:
sourcetype="email*" | rename SenderAddress as indicator | append [| inputlookup tci | rename "tag.name" as tag | fields type, tag, indicator] | stats latest(*) as * by indicator
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @manjunathmeti
If I give subsearch I am getting truncated results since my lookup and sourcetype have heavy results. Thats the reason I decided to move to lookup command,
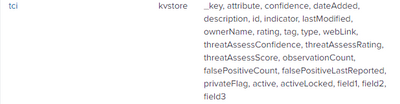
Also I looked into definition of tci lookup where I could see in supported field column it is, "tag".
So I ran the query as below,
sourcetype="ms:o365*" | rename SenderAddress as indicator |lookup tci indicator output type,rating,tag|where isnotnull(type)|dedup indicator|table indicator tag
Now I am not getting any error, but my tag column is empty.
Then I tried running the below query without renaming tag.name field since tag field was supported in earlier query,
|inputlookup tci|search indicator="*"|table indicator tag
Here it says, No matching fields exist.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My case is same as described in post suggested by you,
https://community.splunk.com/t5/All-Apps-and-Add-ons/Lookup-command-doesn-t-support-dot-notation-in-...
The field itself is mentioned only "tag" in definition. PFB the image,
But when I run |inputlookup tci|search indicator="*" the results are like below with tag.name field,
Also I tried,
sourcetype="email*"|lookup tci indicator output type,rating,tag as tag.name|where isnotnull(type)|dedup indicator|table indicator tag.name
Still getting empty field.
Is there any other way where I can rename my field manually except getting into lookup definitions.