Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Dealing with Lists
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
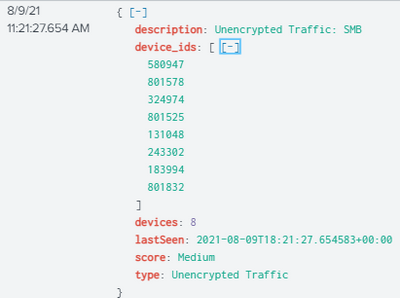
I have network logs that show various network device communication that are in an index in Splunk. I have another index that has information about the devices that I need to report on. But I'm having issues because the network logs are summarizing the network activity and showing all the devices with the same activity, as seen below:
How can I get the individual information about the devices and/or how can I enumerate the information above. If I send to a table, the device_ids will be blank, even if there is only one device in the list.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
your first search
| rename device_ids as device_id
| append [your second search
| rename device_field as device_id]
| stats values(*) as * by device_id- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
device_ids still come in as a list and doesn't expand to find the device from the second list. What am I doing wrong?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you share the raw event rather than an image of the formatted event?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The base index of assets is:
index=asset sourcetype=Network:Asset
| table id ipAddress macAddress name type tags
The index with network activity is:
index=test sourcetype=network | table description device_ids devices lastSeen score type
I'm trying to merge the data together with the asset information so I know what and where the activity is. I'd like a table like this:
id ipAddress name description lastSeen score type macAddress tags
I could join the indexes to get what I'm looking for using device ids as you suggested. But the issue I'm having is the second SPL with the list of ids in the device_ids field. I don't know how to enumerate them to merge the asset index with the test index.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can't see how we can help you without you sharing the events you are dealing with because we have suggested things based on our assumptions, which you say don't give you what you want, so our assumptions are probably incorrect. It is fine for you to not share, but I can't see how we can help you further in that case.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
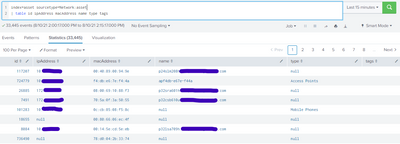
Here is the table output of the first SPL
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
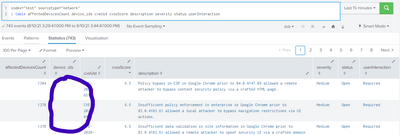
Here is the second SPL in table format, you can see the device_ids are blank but the affectedDevicesCount show there are over 1300 ids in the device_ids field. That is why I posted the _raw unformated data to open because I could expand the list given for the device_ids field.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It looks like the field is not being extracted. In order to help you extract it in the search, we need to see the raw data from the events. You haven't posted the raw event - rerun the search in verbose mode, click on the events tab, expand one (or more) of the event (if it has more lines to show) and copy the raw data from the event.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
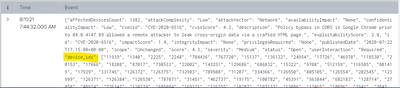
Sorry, I'm a n00b. Here is the first event in the previous screenshot. You can see the device_ids are returned, but not shown on the table. I need to take each device_id and return an event for each id, that way I can join with the other index for network asset information. As you can see now, I don't know what asset it transmitting the packets.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| spath device_ids{} output=device_ids
| mvexpand device_ids- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you, that is exactly what I was looking for.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Break the list up into separate events by using mvexpand device_ids.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I attempted to use mxexpand but the same result on search was returned. Only 1 event exactly as shown above. How will this command create new events with the same data, only an individual device_id? I tried using a table, but still nothing:
index="test" sourcetype="network"
| mvexpand device_ids
| table device_ids description devices lastSeen score type
Sorry, I'm a n00b