- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Custom Command Protocol Version 2-What needs to be...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Custom Command Protocol Version 2-What needs to be changed when switching from version 1 to version 2?
Hi all,
I am currently a little bit stuck ...
Commands.conf looks like this:
[tc]
chunked = true
filename = tc.py
[t]
retainsevents = true
streaming = true
filename = t.py
tc is the same command as t but it should use protocol version 2 instead of 1
The version 1 script works but when using the version 2 script, it just says
"Could not locate the time (_time) field on some results returned from the external search command 'tc'"
Documentation on version 2 is a little bit sketchy so,
--> what needs to be changed when switching from version 1 to version 2?
--> is there a sample custom streaming command for version 2 ?
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ha, yep, I had to guess this myself. The custom search commands (or splunklib in general) docs could use some work.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried to load the SDK for Python and encountered a syntax error because the SDK was created using Python 2.7 and I am using Python 3.5. Am I doing something wrong? I loaded the SDK egg that has a time stamp of 2016. Is there a new version of the SDK?
Thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi liujie
This question was posted 2 years ago. If none of the answers were able to help you with your question, please post a new question so you can get maximum exposure and help.
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello guys,
is the now maybe a other documentation out, which explains the interface?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
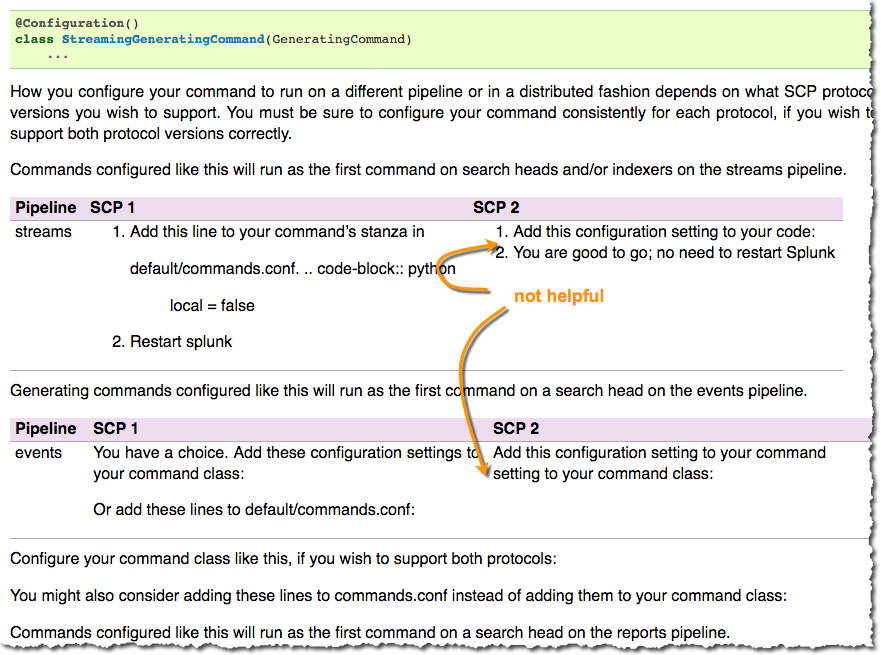
I had the same questions. The online documentation provides not helpful advice like:
Turns out it's a problem with their documentation parsing from the source code. You can find this info in the comments of splunklib/searchcommands/generating_command.py. eg:
Reporting Generating command
============================
Commands configured like this will run as the first command on a search head on the reports pipeline.
+----------+---------------------------------------------------+------+
| Pipeline | ... | SCP 2 |
+==========+=...==+===================================================+
| events | ... | Add this configuration setting to your command |
| | ... | setting to your command class: |
| | ... | |
| | ... | .. code-block:: python |
| | ... | @Configuration(type='reporting') |
| | ... | class SomeCommand(GeneratingCommand) |
| | ... | ... |
| | ... | |
| | ... | |
| | ... | |
| | ... | |
| | ... | |
| | ... | |
+----------+---------------------------------------------------+------+
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
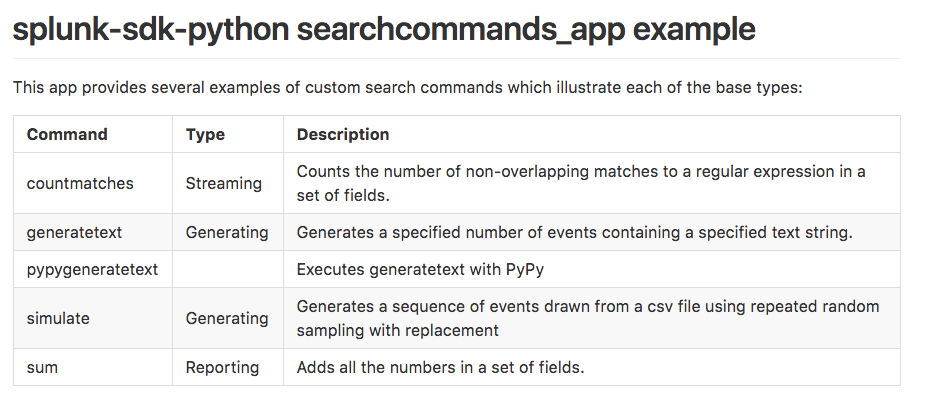
There are some great examples in the Python SDK:
https://github.com/splunk/splunk-sdk-python/tree/master/examples/searchcommands_app
At time of writing:
├── bin
│ ├── splunklib
│ │ └── searchcommands ....... splunklib.searchcommands module
│ ├── countmatches.py .......... CountMatchesCommand implementation
│ ├── generatetext.py .......... GenerateTextCommand implementation
│ ├── pypygeneratetext.py ...... Executes generatetext.py with PyPy
│ ├── simulate.py .............. SimulateCommand implementation
│ ├── sum.py ................... SumCommand implementation
│ └──
├── default
│ ├── data
│ │ └── ui
│ │ └── nav
│ │ └── default.xml ..
│ ├── app.conf ................. Used by Splunk to maintain app state [1]
│ ├── commands.conf ............ Search command configuration [2]
│ ├── logging.conf ............. Python logging[3] configuration in ConfigParser[4] format
│ └── searchbnf.conf ........... Search assistant configuration [5]
└── metadata
└── local.meta ............... Permits the search assistant to use searchbnf.conf[6]
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well, there's nothing wrong with your configuration. I can't look into the Python script or the query so it's really hard to debug. As inspiration you might want to look a what others wrote, e.g.: https://answers.splunk.com/answers/387430/cant-we-use-a-custom-search-command-with-stats-in.html
Hope this helps...