Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Create Multi-Value field based 4 fields
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
jachockey012
Explorer
01-06-2021
11:44 PM
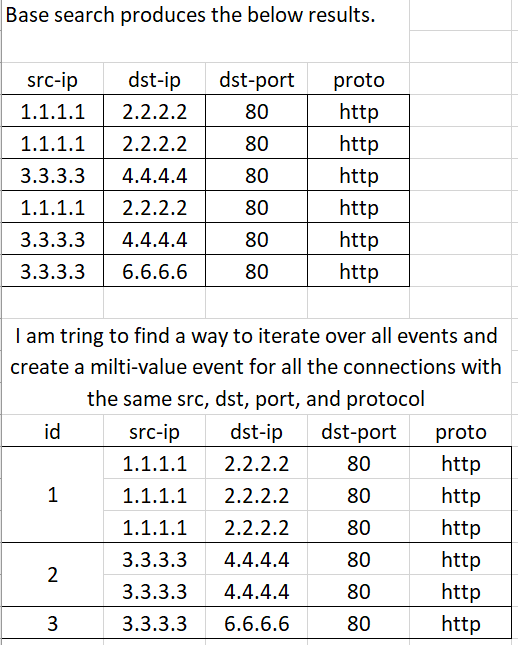
So basically I have some network logs and by base search filters down to source IP, destination IP, destination port, and protocol. I am trying to figure out a way to iterate over all events and group based off the 4-tuple data mentioned above. Below is an image of what I am thinking. You'll notice I added an ID field and I figured that would somehow be the equivalent to ID+=1 at the end of a loop or something.
The original data is bro logs. If you need a list of all the fields below is a link and the source is the conn.log (the green box on the first page)
http://gauss.ececs.uc.edu/Courses/c6055/pdf/bro_log_vars.pdf
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ITWhisperer

SplunkTrust
01-07-2021
01:29 AM
| eval tuple='src-ip'.'dst-ip'.'dst-port'.'proto'
| stats list(src-ip) as src-ip list(dst-ip) as dst-ip list(dst-port) as dst-port list(proto) as proto by tuple
| streamstats count as id
| fields - tuple- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ITWhisperer

SplunkTrust
01-07-2021
01:29 AM
| eval tuple='src-ip'.'dst-ip'.'dst-port'.'proto'
| stats list(src-ip) as src-ip list(dst-ip) as dst-ip list(dst-port) as dst-port list(proto) as proto by tuple
| streamstats count as id
| fields - tuple- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
jachockey012
Explorer
01-07-2021
05:18 AM
Effective... Thank you very much.
Get Updates on the Splunk Community!
App Platform's 2025 Year in Review: A Year of Innovation, Growth, and Community
As we step into 2026, it’s the perfect moment to reflect on what an extraordinary year 2025 was for the Splunk ...
Operationalizing Entity Risk Score with Enterprise Security 8.3+
Overview
Enterprise Security 8.3 introduces a powerful new feature called “Entity Risk Scoring” (ERS) for ...
Unlock Database Monitoring with Splunk Observability Cloud
In today’s fast-paced digital landscape, even minor database slowdowns can disrupt user experiences and ...