Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Counting the number of responses and displaying in...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I'd like to count the number of responses by the following status codes: 2xx, 4xx and 5xx.
I'm basically counting the number of 2xx, 4xx and 5xx statuses for each API that is read line by line from a CSV file.
The only problem that I'm struggling with is I can't figure out how to sum and group the number of counted 2xx and 4xx status codes under a common label named: non5xx that refers to non-server error status codes and then display it in a pie/column/bar chart.
So far, I've come up with the follwing query, but it fails to meet my expectations:
[| inputlookup api_names_file.csv | rename AppName to app_name | table app_name] | chart count(eval(like(status, "2%"))) AS successResponses, count(eval(like(status, "4%"))) as clientErrorResponses, count(eval(like(status, "5%"))) AS 5xx BY app_name | eval total = (successResponses + clientErrorResponses) | eventstats sum(total) AS non5xx by app_name | fields non5xx, 5xx
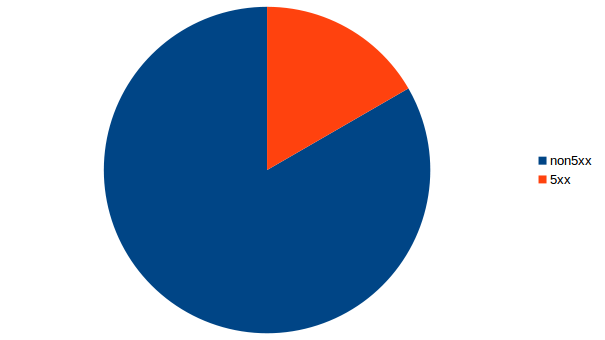
Eventually, I'd like to end up with the following chart:
- The non5xx group would refer to the sum of counted 2xx and 4xx statuses grouped together.
- The 5xx group picture the number of 5xx server error responses.
Is is possible to group the counted 2xx and 4xx status codes under a common label, just like on the aforementioned pie chart?
Of course, it may an arbitrary type of chart including the column, and bar ones as well.
Thank you in advance
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @wjz,
Can you please try these searches??
Search for the count of status like 2xx,4xx & 5xx.
| inputlookup api_names_file.csv | eval status=case(like(status, "2%"),"2xx",like(status, "4%"),"4xx",like(status, "5%"),"5xx") | stats count by status
Search for the count of status like non5xx & 5xx.
| inputlookup api_names_file.csv | eval status=case(like(status, "2%") OR like(status, "4%"),"non5xx",like(status, "5%"),"5xx") | stats count by status
Just change the visualization to the pie chart.
Happy Splunking
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Adding to this thread if we need to have a pie- section based on 4 values 2xx,4xx,5xx,"Others". Others are the codes not in 2xx,4xx,5xx
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @wjz,
Can you please try these searches??
Search for the count of status like 2xx,4xx & 5xx.
| inputlookup api_names_file.csv | eval status=case(like(status, "2%"),"2xx",like(status, "4%"),"4xx",like(status, "5%"),"5xx") | stats count by status
Search for the count of status like non5xx & 5xx.
| inputlookup api_names_file.csv | eval status=case(like(status, "2%") OR like(status, "4%"),"non5xx",like(status, "5%"),"5xx") | stats count by status
Just change the visualization to the pie chart.
Happy Splunking
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Assuming this query gives you count of 2xx, 4xx and 5xx error for each app_names
[| inputlookup api_names_file.csv | rename AppName to app_name | table app_name] | chart count(eval(like(status, "2%"))) AS successResponses, count(eval(like(status, "4%"))) as clientErrorResponses, count(eval(like(status, "5%"))) AS 5xx BY app_name
Use this query to get the consolidated pie chart data you need.
[| inputlookup api_names_file.csv | rename AppName to app_name | table app_name]
| eval type=if(like(status,"5%"),"5xx","non5xx")
| stats count by type