Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Cisco CDR: How to remove two columns in report ext...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cisco CDR: How to remove two columns in report extraction
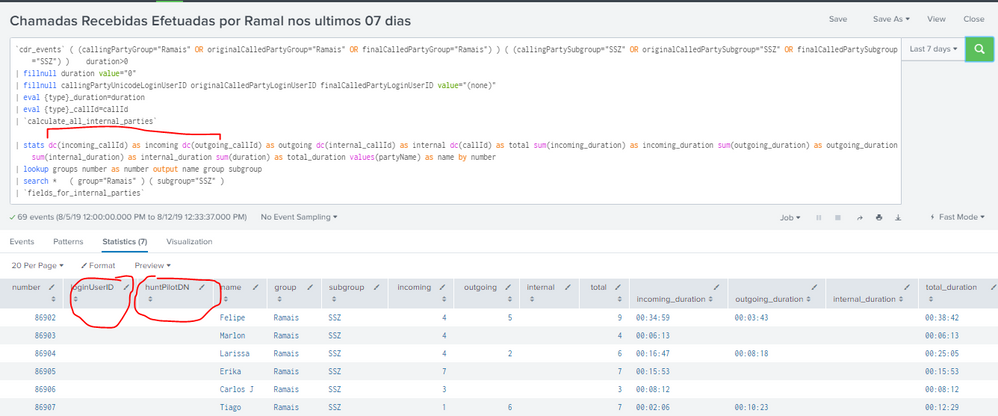
I need to remove these two columns in the report extraction, I already removed the values in the "search" for these columns, but still they are displayed.
I need remove "loginUserID" and "huntPilotDN" ;
My search:
cdr_events ( (callingPartyGroup="Ramais" OR originalCalledPartyGroup="Ramais" OR finalCalledPartyGroup="Ramais") ) ( (callingPartySubgroup="SSZ" OR originalCalledPartySubgroup="SSZ" OR finalCalledPartySubgroup="SSZ") ) duration>0
| fillnull duration value="0"
| fillnull callingPartyUnicodeLoginUserID originalCalledPartyLoginUserID finalCalledPartyLoginUserID value="(none)"
| eval {type}_duration=duration
| eval {type}_callId=callId
| calculate_all_internal_parties
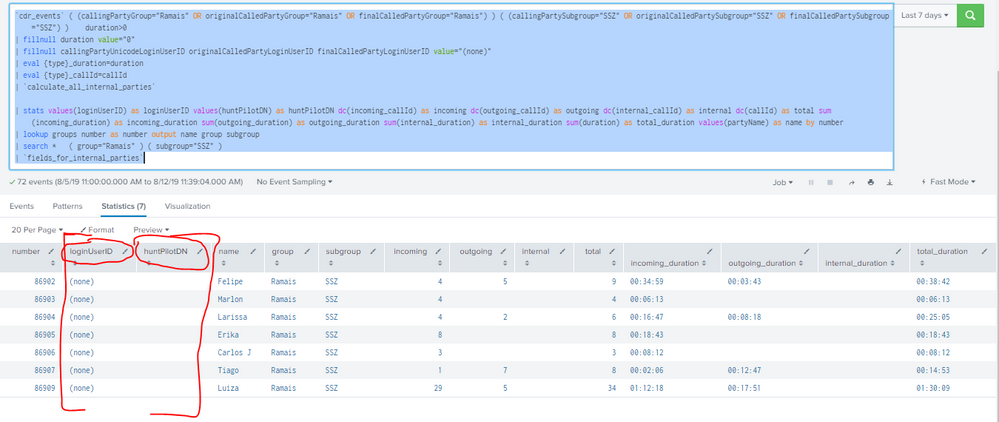
| stats values(loginUserID) as loginUserID values(huntPilotDN) as huntPilotDN dc(incoming_callId) as incoming dc(outgoing_callId) as outgoing dc(internal_callId) as internal dc(callId) as total sum(incoming_duration) as incoming_duration sum(outgoing_duration) as outgoing_duration sum(internal_duration) as internal_duration sum(duration) as total_duration values(partyName) as name by number
| lookup groups number as number output name group subgroup
| search * ( group="Ramais" ) ( subgroup="SSZ" )
| fields_for_internal_parties
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry for the delayed response! I hadn't noticed this question until now - no idea how that escaped me.
To fix your problem, you can simply - as the very last item in that search - trim out the fields you don't need. For instance, in your case you probably want to add a line
... all your other stuff...
| fields - loginUserID huntPilotDN
That will use the fields command to remove ( -) the two fields loginUserID and huntPilotDN from the output, leaving all else as the same.
One other way would be to use the table command and just rewrite which field goes where and, if desired, drop other fields out. For instance, you could remove those two field, and also move total_duration to the left, by
... all your other stuff...
| table total_duration text number name group subgroup incoming outgoing internal business_hours off_hours total incoming_duration outgoing_duration internal_duration business_hours_duration off_hours_duration
But as you can see, that's quite a bit more work and more precarious - you have to use the right capitalization for each field or else it'll just be blank. So it is much simpler if all you need is to remove a field or two to just use the fields command as shown above. But I thought if you DID need a more complete "change my columns around a bit" I'd give it with that table command.
Let us know if this worked for you by marking it as Accepted, please! If it did not, please post back and we can make it jump through any additional hoops you need!
Happy Splunking,
Richfez
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Alguma sugestão ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@fiveitsplunk remove following two aggregates from your stats
values(loginUserID) as loginUserID values(huntPilotDN) as huntPilotDN
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, I removed it from the fields but it still returns after "re-searching".
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content